You might have read many times during your studies that changing the native VLAN1 on Cisco switch trunk ports is highly recommended. Some documentations do not give any explanation about this recommendation, others might give a hint associating the recommendation to security, and still others might give a brief explanation referring to preventing VLAN Hopping Attack.
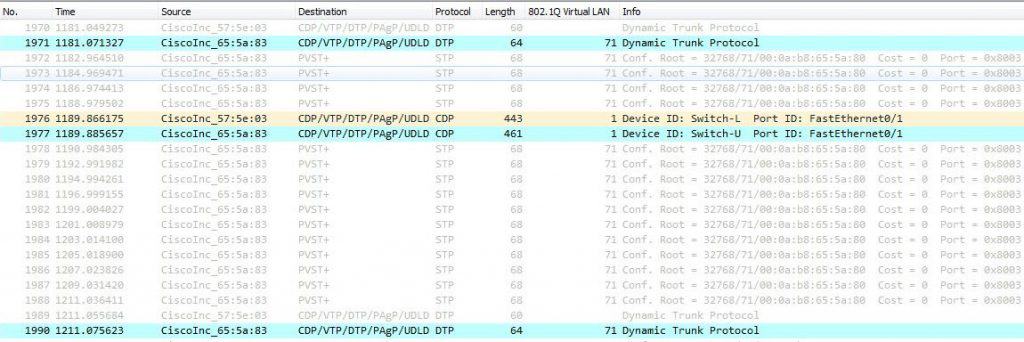
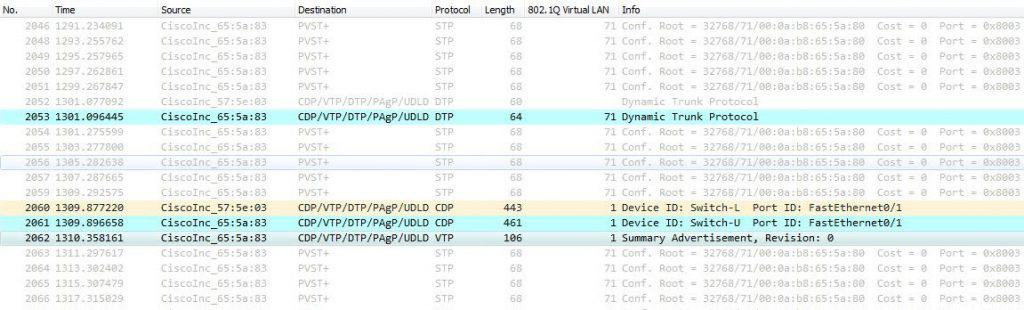
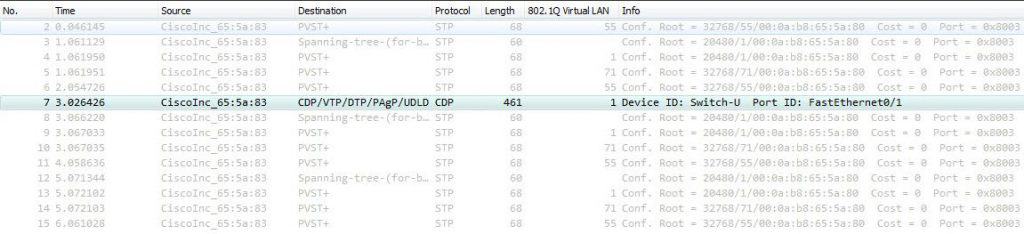
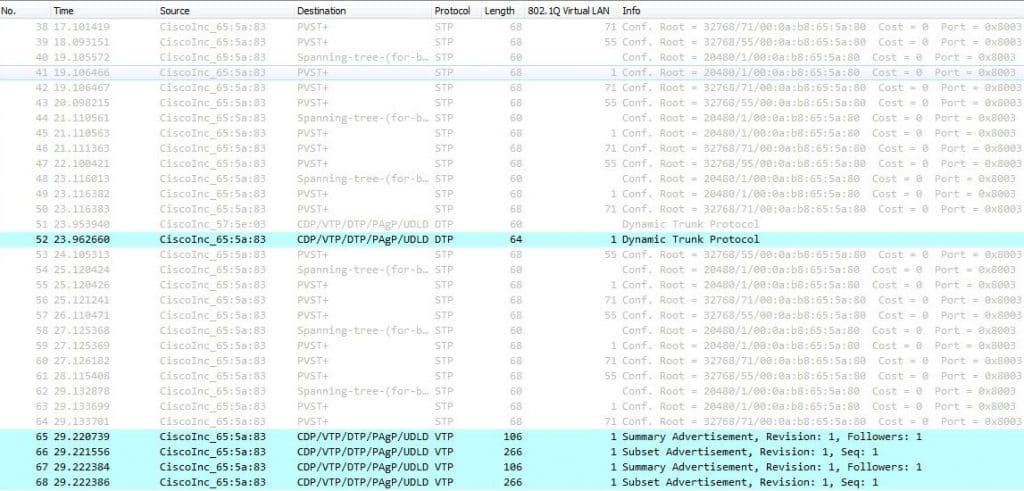
Why VLAN1 in particular?! What does VLAN1 have to do with VLAN Hopping Attack?! Isn’t VLAN1 like any other VLAN on the switch?! Well, VLAN1 is a real special VLAN on Cisco switches—it is the default access VLAN, it is the default native VLAN on trunk ports, and it is also the VLAN in which some L2 protocols exchange their traffic. L2 protocols such as CDP and VTP are VLAN1 dependent, which means they will keep sending traffic between switches in VLAN1 even if VLAN1 is not allowed on the trunk port. Only this behavior would make VLAN1 so special. Here are some screenshots for reference where VLAN71 is the native VLAN and VLAN1 is not allowed on the trunk port:
Below the native VLAN is VLAN1:
Now to get the point about why VLAN1 has to do with VLAN Hopping Attack, we need to go through some explanations of how VLAN Hopping Attack works. The simple definition of VLAN Hopping is to allow some traffic to be sent from one VLAN to another. In normal scenarios, this would be the expected and desired behavior where we have a L3 routing. However, in other scenarios, that would not be allowed as an example in L2 VLANs. However, VLAN Hopping Attack would give an attacker the ability to send traffic from a VLAN to another in those L2 VLANs scenarios.
VLAN Hopping Attack is unidirectional which means it could be accomplished in one way with no returning traffic to the attacker. This can still be harmful, because it could easily be used in a DoS or a DDoS attack and bring down a target machine by consuming its resources up to the point to make it unable to process any traffic. The target machine could be any device on the network—a server, a workstation, a door access controller, etc.
There are two methods to accomplish VLAN Hopping Attack, and each have some conditions to be met before an attacker would be able to successfully accomplish the attack. The two methods are Switch Spoofing and Double Tagging:
- Switch Spoofing: Most if not all Cisco switches default port configurations are set to dynamically allow trunk negotiation; in other words, they are not configured as access ports. This would allow any additional switch to be connected to any of those ports and negotiating successfully a trunk connection to join the domain. That would also happen if the neighbor switch port is statically configured in trunk mode. The protocol that would make the dynamic negotiation to happen is Dynamic Trunking Protocol (DTP). When a new switch is connected to a dynamic port, it would try to negotiate the trunk connection by sending DTP frames. The dynamic trunk negotiation would happen if the neighbor switch port would be configured in Dynamic Auto or Dynamic Desirable.This negotiation does not necessarily have to be done by a real switch—it could also be done by a machine that would deceive the switch by sending DTP frames pretending to be a switch. The result would be the same—a trunk connection would be successfully negotiated and established. Here where an attacker machine would easily be able to send traffic between VLANs. This VLAN Hopping Attack method would be possible by having the attacker and the target machines connected to the same switch. The attacker in this case would use malicious software to add the target VLAN tag to the ethernet frame, when the switch receives the frame it would just forward it to the destination VLAN where the target machine resides.Let’s take an example, let’s assume the attacker has successfully negotiated a trunk connection with switch A, and the attacker wants to send malicious traffic to the target machine located in VLAN50 which has the MAC address of aaaa.bbbb.cccc. The attacker would inject VLAN ID 50 into the 802.1q tag and send it to the switch. If the switch knows the target machine port by doing a lookup on the CAM table, the switch would then forward the traffic directly to the target machine port. If the target machine MAC address has never been seen before on the switch or if it has been removed from the CAM table the switch would then broadcast the traffic to all the ports belonging to VLAN50. The result would be the target machine would receive and process that traffic, and that would complete the VLAN Hopping Attack.This VLAN Hopping Attack would be mitigated by configuring the end users switch ports in access mode.
- Double Tagging: The conditions that should be met with double tagging before an attacker could accomplish the VLAN Hopping Attack would be to have two separate switches. Each of the attacker and the target machines have to be connected to a separate switch, and also the attacker switch port has to be configured in access mode in the same VLAN as the native VLAN on the trunk connection between the two switches. You might be wondering how an access port would allow tagged frames. The reality would be that switches would allow this to happen if the 802.1q tag would be the same as the access VLAN configured on the switch port, or if the received frame is a priority tagged frame 802.1p (QoS). However, a voice VLAN should be configured on the access port to allow the tagged frames. In that case the port would turn to be a hybrid port, not purely an access port nor purely a trunk port.The way an attacker would accomplish VLAN Hopping Attack in this scenario would be to use malicious software to inject double 802.1q tags. The inner tag would include the target machine VLAN ID, and the outer tag would include the attacker access VLAN ID, which is also the native VLAN on the trunk connection between the attacker and the target machine switches. When the local switch (where the attacker is connected) receives the frame, it would strip off the outer tag header, and then based on the second tag (which includes the target machine VLAN ID), the switch would then forward the frame across the trunk connection. When the remote switch (where the target machine is connected) receives the frame, it would then forward it to the target VLAN port, assuming the target machine MAC address would be already in the CAM table, or otherwise to all ports in the target machine VLAN. The target machine would receive and process the frame, and that would make the VLAN Hopping Attack successful.Let’s take an example assuming an attacker is connected to switch A to a port in VLAN1, which is also the native VLAN on the trunk connection between switch A and switch B. The target machine is connected to a port to switch B in VLAN50. For the attacker to be able to send malicious traffic to the target machine, the attacker has to inject two 802.1q tags in the ethernet frame, that could be easily achieved by using malicious software. The inner tag would include VLAN50, and the outer tag would include VLAN1. The attacker sends the frame to the switch, and the switch looks at the outer tag (VLAN1) and strips it off and then forwards the frame directly to the trunk connection if the target machine MAC address is known already by the switch, otherwise to all VLAN1 ports including the trunk connection. The frame travels over the trunk connection carrying the second tag (VLAN50) along. When the remote switch receives the frame, it would look at the tag and sees VLAN50, based on that the remote switch would forward the frame directly to the target machine if it knows already the target machine port based on the CAM table lookup, or otherwise to all VLAN50 ports. The target machine would then receive and process the frame, and that would make the VLAN Hopping Attack successful.This VLAN Hopping Attack would be mitigated by changing the native VLAN1 to something different that is not used anywhere else on the switch, or, to force the switch to tag the native VLAN frames. By changing the native VLAN, the attacker would not be able to deceive the switch by sending double tagging frame, because in that case the switch would drop the frame since its outer tag would have a VLAN ID (native VLAN ID) that is not the same as the access VLAN configured on the attacker port. The second option instead, which is forcing the switch to tag the native VLAN frames, would make the switch to add 802.1q tag to VLAN frames across the trunk connection. By doing so, even if the attacker sends a double tagged frame, the switch would not strip off the outer tag (native VLAN ID), and it would send it tagged across the trunk connection. When the remote switch receives that frame, it would look at the tag, and because it is the native VLAN ID tag, the switch would then send that frame to all native VLAN ports, where the target machine is not located, so the attack would fail. In other words, the second tag would never be considered.It would not hurt to apply all the above measures to mitigate the VLAN Hopping Attack. They are disabling trunk and dynamic ports where is not required by placing the ports in access mode, using a native VLAN on the trunk connection that is not used anywhere else on the switch, and forcing the switch to tag the native VLAN frames which are untagged by default.
I hope you enjoyed reading this blog, I would love to hear from you for any comment. Thank you for reading.