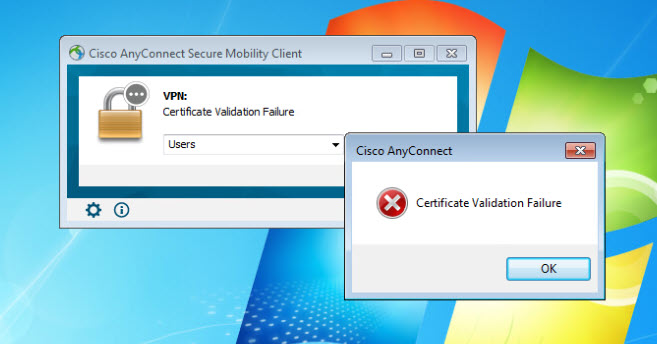
This post will cover one interesting root cause of getting AnyConnect Certificate Validation Failure. I was working on setting up a Cisco AnyConnect Management Tunnel, which I will cover in another post, and for some reason when I was trying to establish AnyConnect SSL VPN from a Windows client, it was just failing dropping the message Certificate Validation Failure on the screen.
I thought there was something wrong with the client certificate or maybe the trust point on the ASA that is configured to authenticate AnyConnect clients. Checking on the client side, all was looking good, and the user and machine certs were successfully installed, and the issuer root CA certificate was in the trusted store.
Similarly on the ASA side, the ASA identity certificate was looking good, as well as the trust point that is responsible to authenticate the clients. This trust point is configured with OCSP for the revocation check. the OCSP is a Windows server. I also checked the OCSP configuration on the Windows server and all was looking good and functional.
I then enabled debug crypto ca 7 on the ASA, and I tried to establish the VPN tunnel again to capture some debug. Here is a snippet from the debug output:
PKI[7]: revocation status queued for session 0x14981ed1 and cert_idx 0, rev_status 6 PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 0, pending: 1 PKI[7]: Evaluating session revocation status, 1 certs to check PKI[7]: starting OCSP FSM #0 CRYPTO_PKI: Attempting to find OCSP override for peer cert: serial number: <omitted>, subject name: CN=test1,CN=Users,DC=mylab,DC=local, issuer_name: CN=WIN-2K12-01-CA,DC=mylab,DC=local. CRYPTO_PKI: No OCSP overrides found. PKI[4]: no AIA for OCSP revocation checking, cert index 0 PKI[7]: OCSP revocation AIA list built for cert index 0 with 0 AIAs, error FALSE PKI[4]: No more AIAs found to try PKI[7]: revocation status queued for session 0x14981ed1 and cert_idx 0, rev_status 6 PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 0, pending: 1 PKI[7]: Evaluating session revocation status, 1 certs to check PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 1, pending: 0 PKI[7]: session: 0x14981ed1, all revocation processing complete PKI[5]: session: 0x14981ed1, error during revocation check of certificate 0 PKI[5]: session 0x14981ed1, Error in revocation check or revoked certs found
Looking online for some help, I found this Cisco documentation:
OCSP Service Nonces
Microsoft implementation of OCSP is compliant with RFC 5019 The Lightweight Online Certificate Status Protocol (OCSP) Profile for High-Volume Environments , which is a simplified version of RFC 2560 X.509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP .
The ASA uses RFC 2560 for OCSP. One of the differences in the two RFCs is that RFC 5019 does not accept signed requests sent by ASA.
It is possible to force the Microsoft OCSP service to accept those signed requests and reply with the correct signed response.
So, it clearly states that Windows servers and ASA use two different RFCs when it comes to OCSP. You can apply one of two fixes to fix this issue. One is through the OCSP responder configuration on the Windows server, and another on the ASA trust point that is configured to authenticate AnyConnect clients. However, Cisco does not recommend this fix on the ASA.
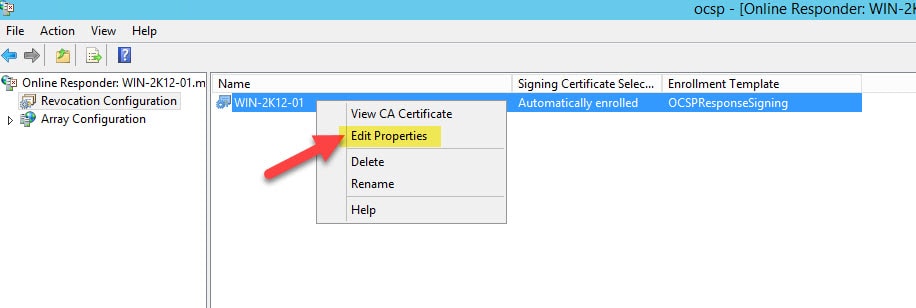
Option 1: Fix on OCSP Windows Server
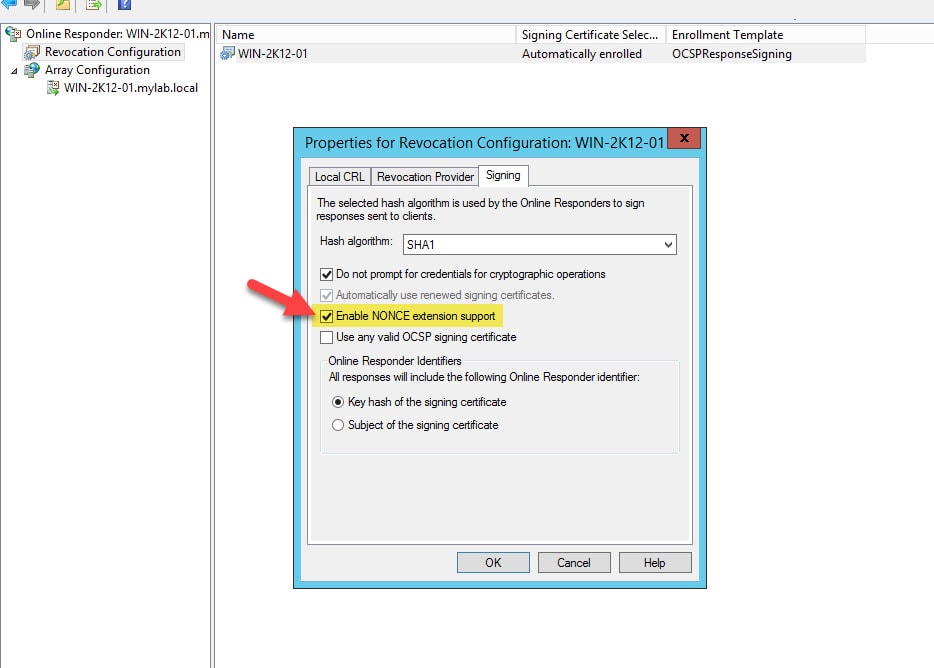
Go to Administrative Tools > Online Responder Management > Revocation Configuration and tick the checkbox next to Enable NONCE extension support
Option 2: Fix on ASA Trust Point (Not recommended by Cisco)
Disable the OCSP nonce under the ASA trust point that is authenticating AnyConnect clients.
ASA(config)# crypto ca trustpoint WIN-2K12-01_Root_CA ASA(config-ca-trustpoint)# ocsp disable-nonce
This wraps up this post about AnyConnect Certificate Validation Failure.
Thank you for reading!
Nice catch.
Do you have (or happened to see online) a post for the whole anyconnect certificate validation setup?
You mean how to set up AnyConnect with certificate authentication? if so, please check out this post:
https://bluenetsec.com/fmc-anyconnect-ssl-vpn/