This post will show you how to configure AnyConnect SSL VPN in FMC. However, it will show you a slightly different configuration comparing to the common one we mostly use. In this lab we will have a DHCP server inside our network, and that DHCP server will assign the AnyConnect clients IP addresses from the same internal range.
Therefore, both the internal and the AnyConnect clients will be served by the same DHCP scope. You might be wondering why we would need this rather than dedicating a specific pool for AnyConnect clients!, well, there is no specific answer or requirement for that.
The only thing I would think about that could be a reason is if you have a bunch of applications that restrict the accesses based on the clients IP addresses in addition to the usernames. Maybe it would not be easy enough to change those applications security policies.
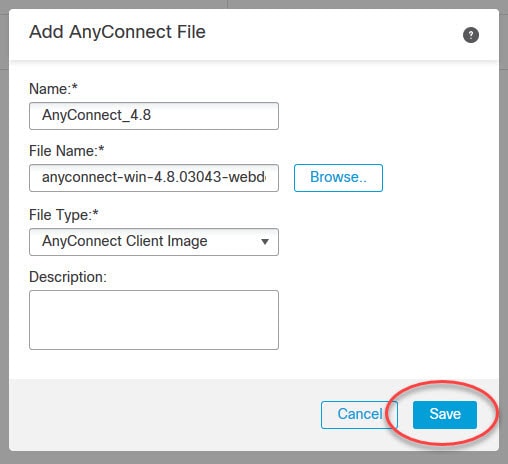
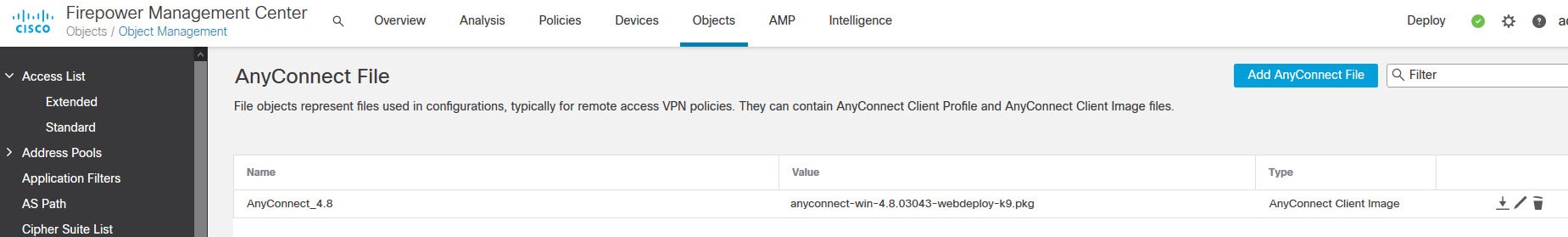
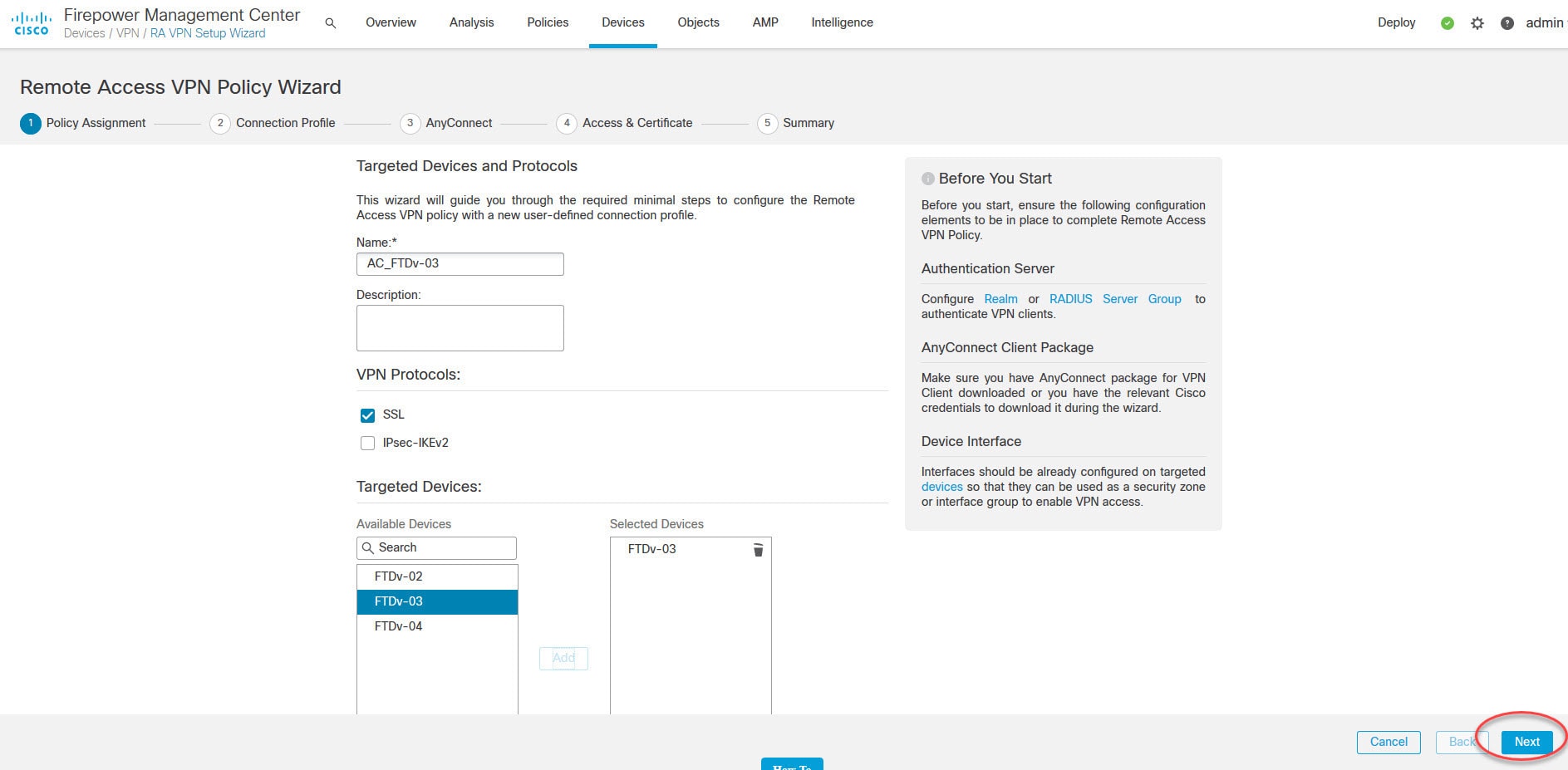
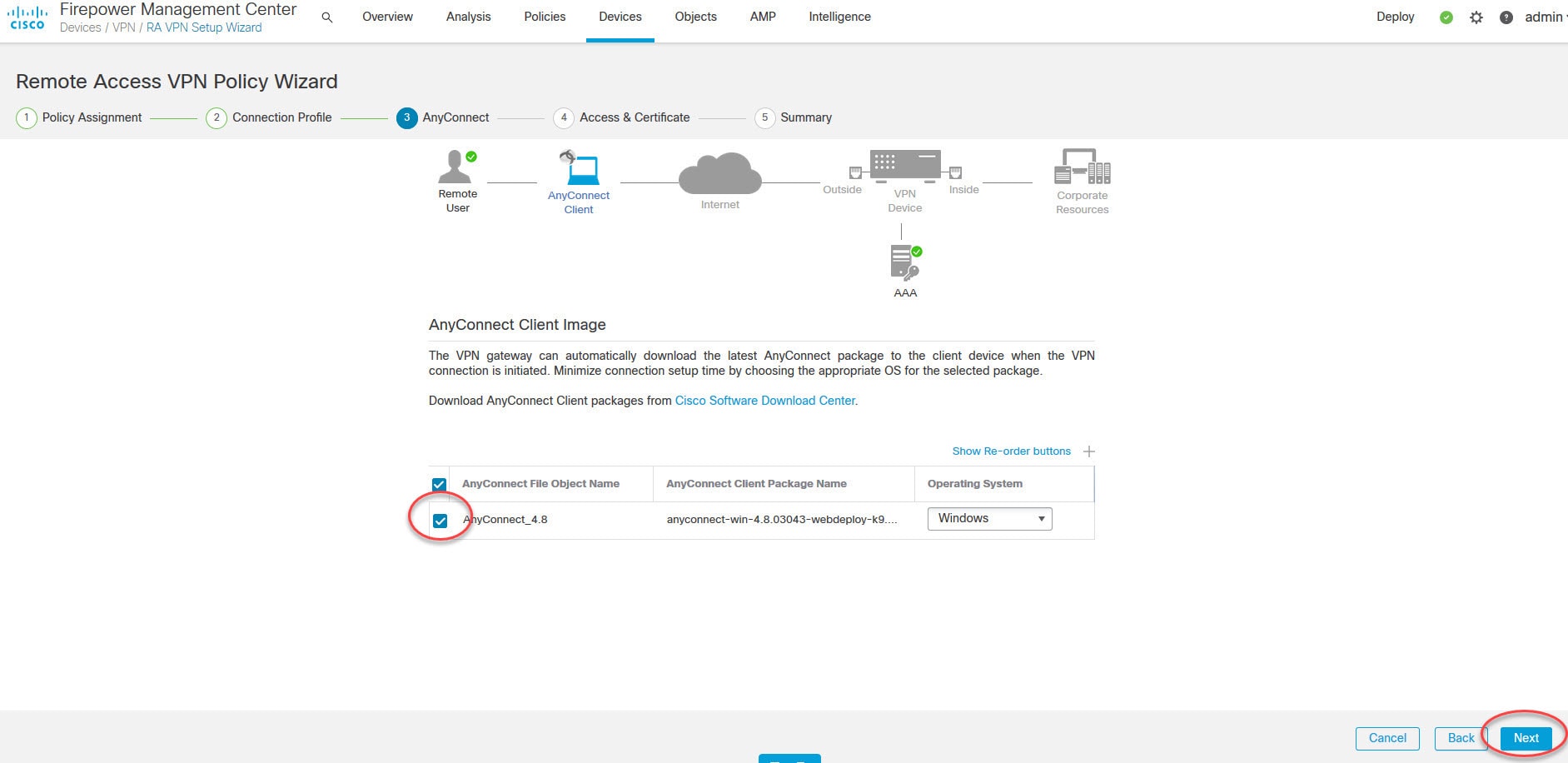
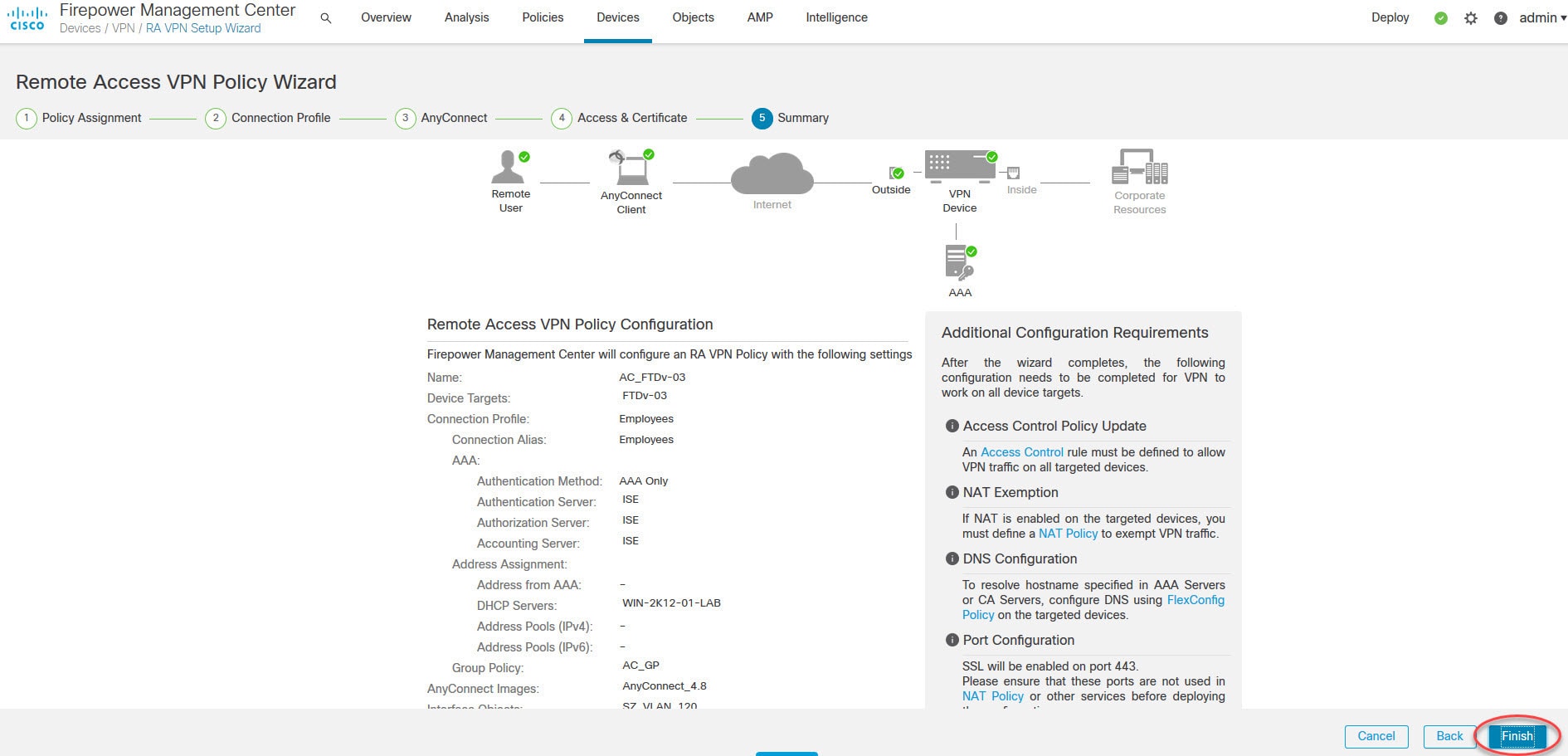
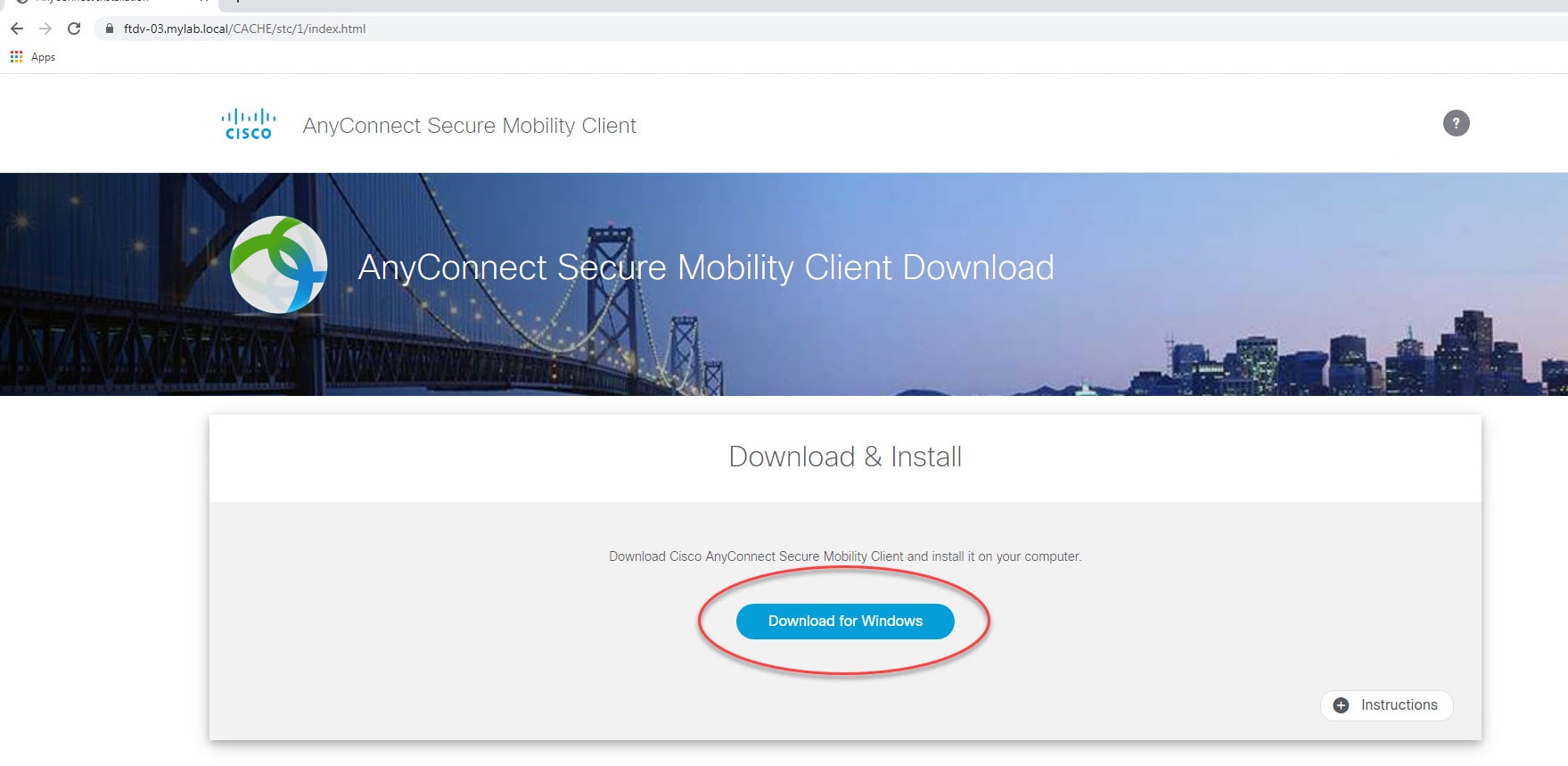
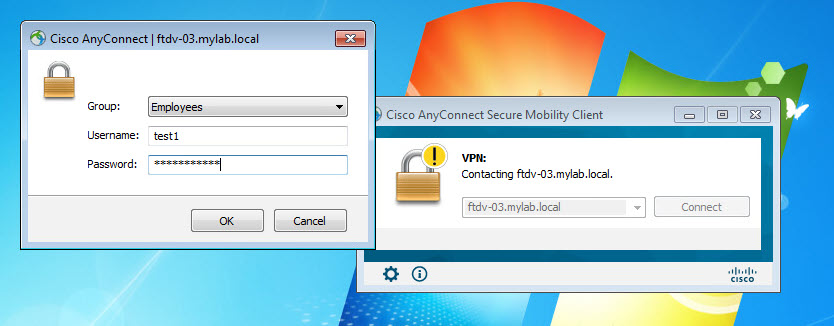
Both the FMC and the FTD device in our lab are running version 6.6.0. And AnyConnect version we are going to use is 4.8.03043. The design requires AnyConnect clients to connect to the FTD device VPN SSL webpage to download the AnyConnect client. And then they will connect to the VPN with their AD usernames and passwords.
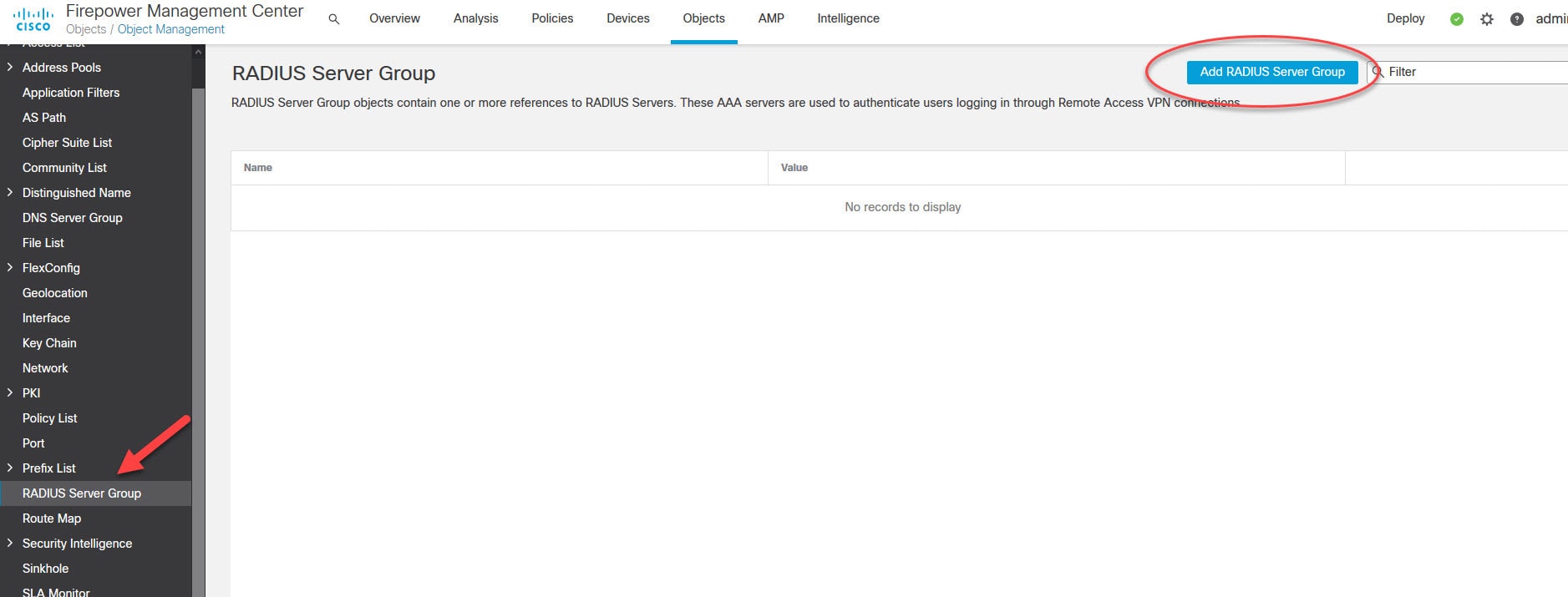
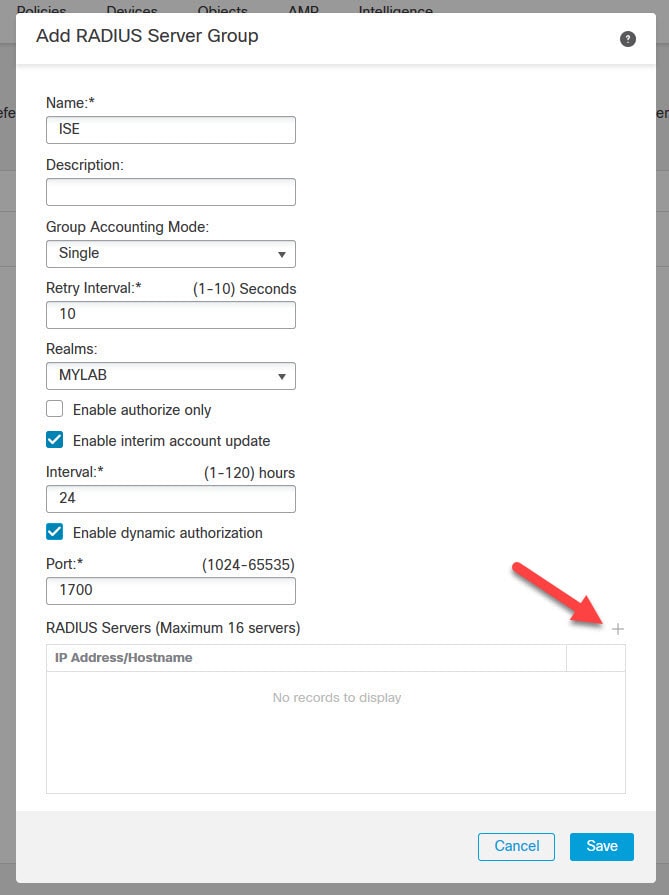
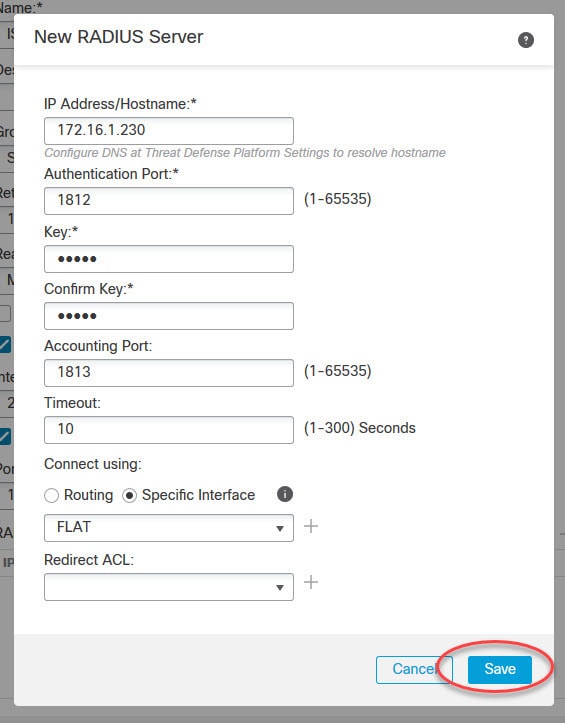
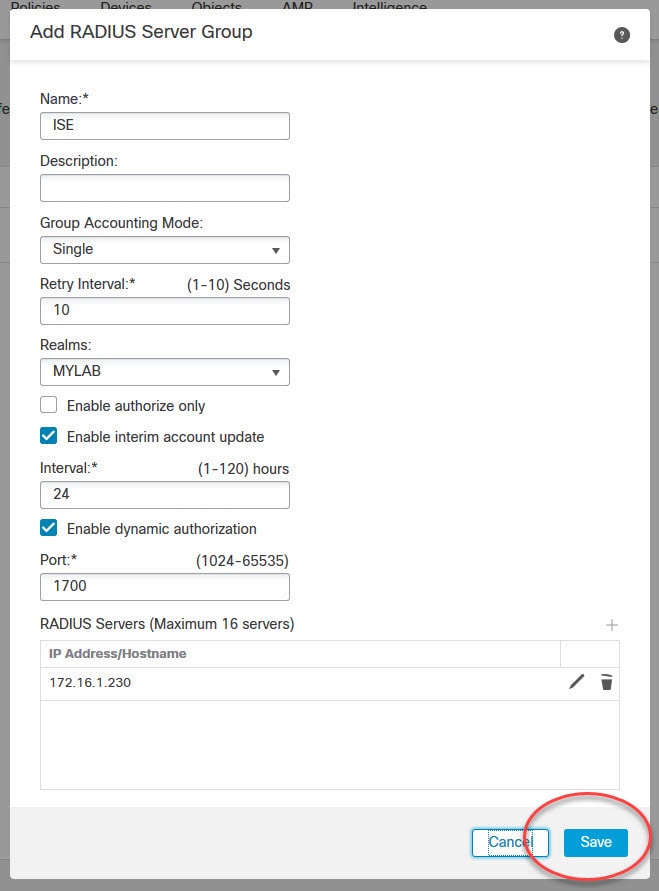
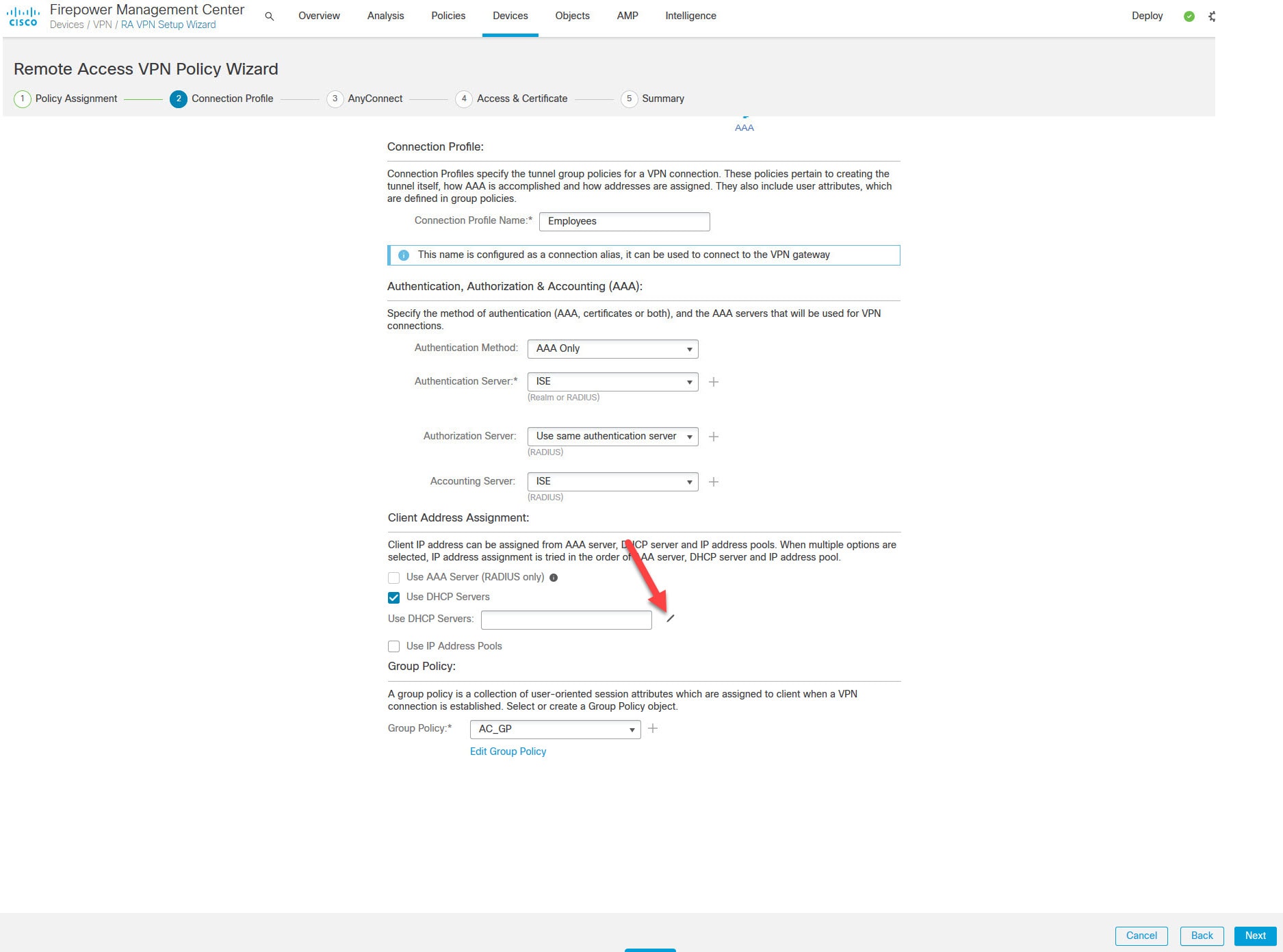
The RADIUS server we will be using is ISE. It is already joined to our Active Directory. I will cover ISE configuration for the AnyConnect SSL VPN in another post, stay tuned!
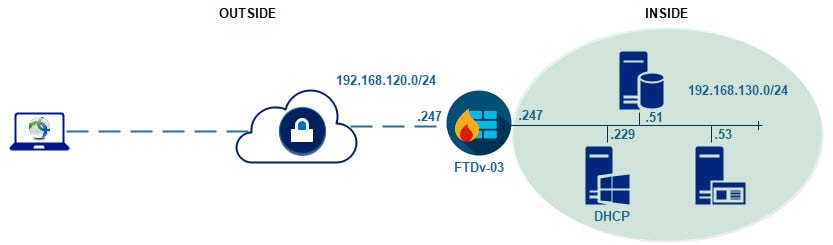
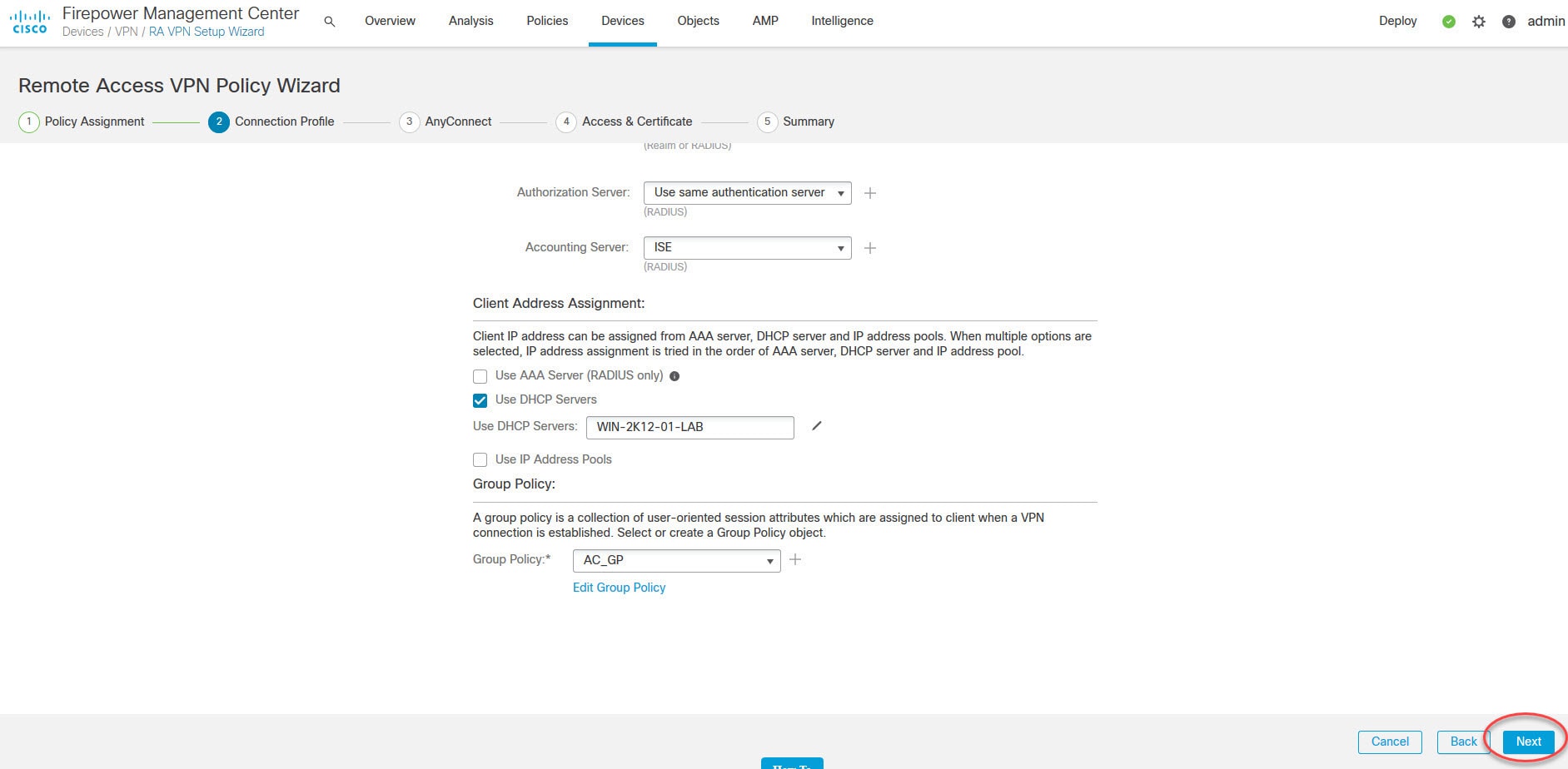
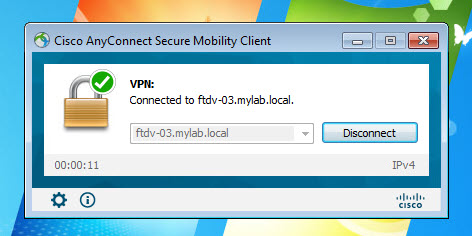
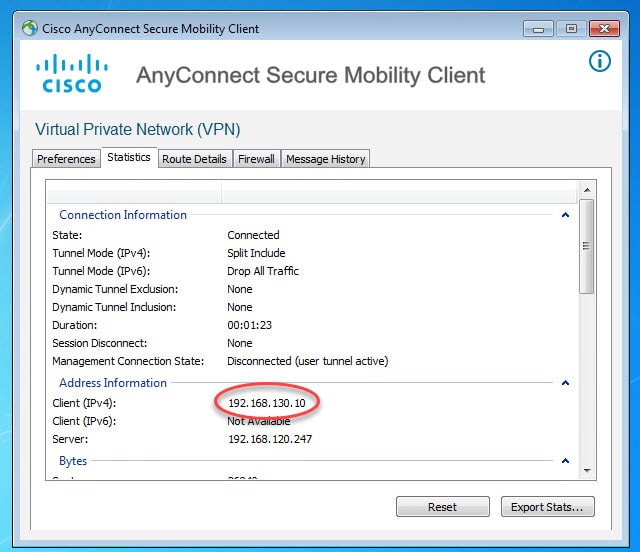
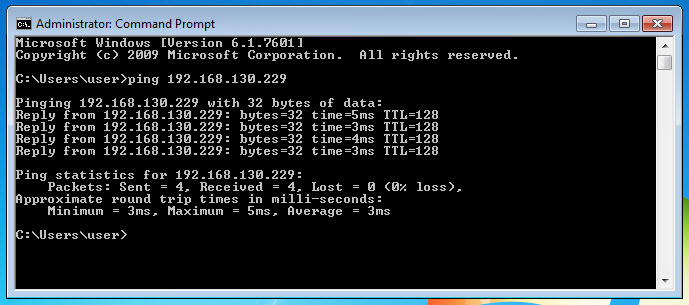
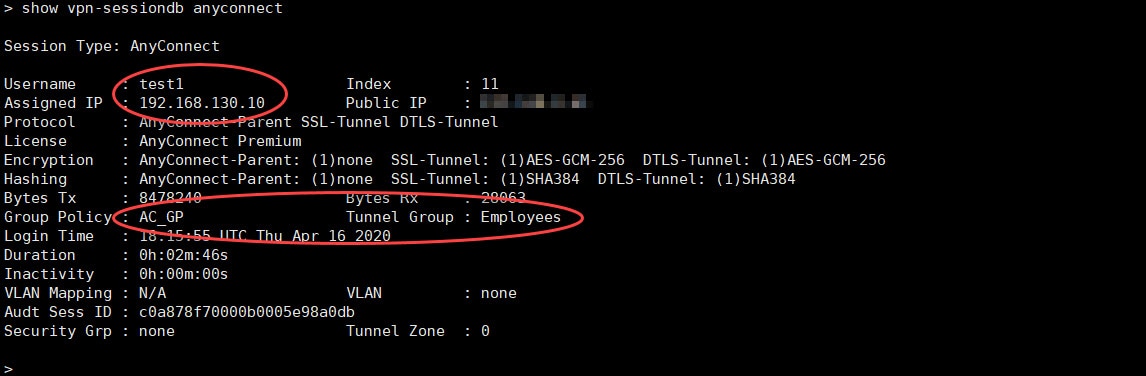
The AnyConnect SSL VPN tunnel will have ISE as its authentication, authorization, and accounting server. Once the clients are connected to the VPN, they will be assigned an IP address from the DHCP scope 192.168.130.0/24 which is configured on our AD.
Topology
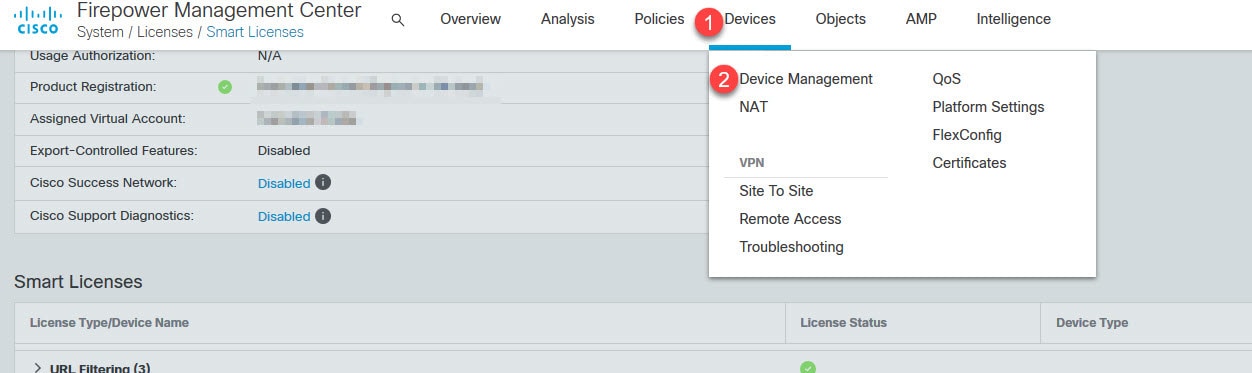
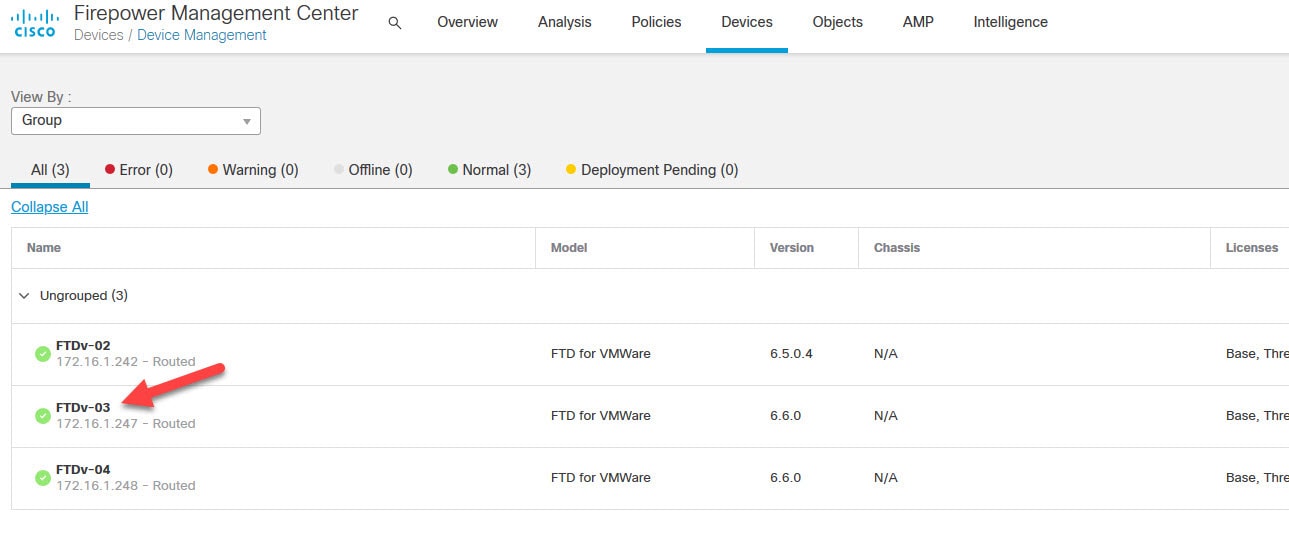
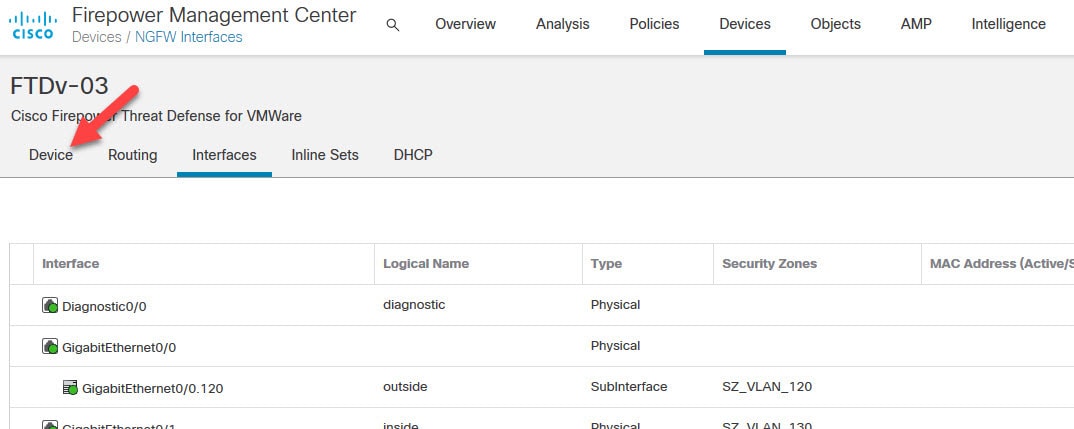
Go to Devices > Device Management and click on the interested FTD, and then click on Device tab
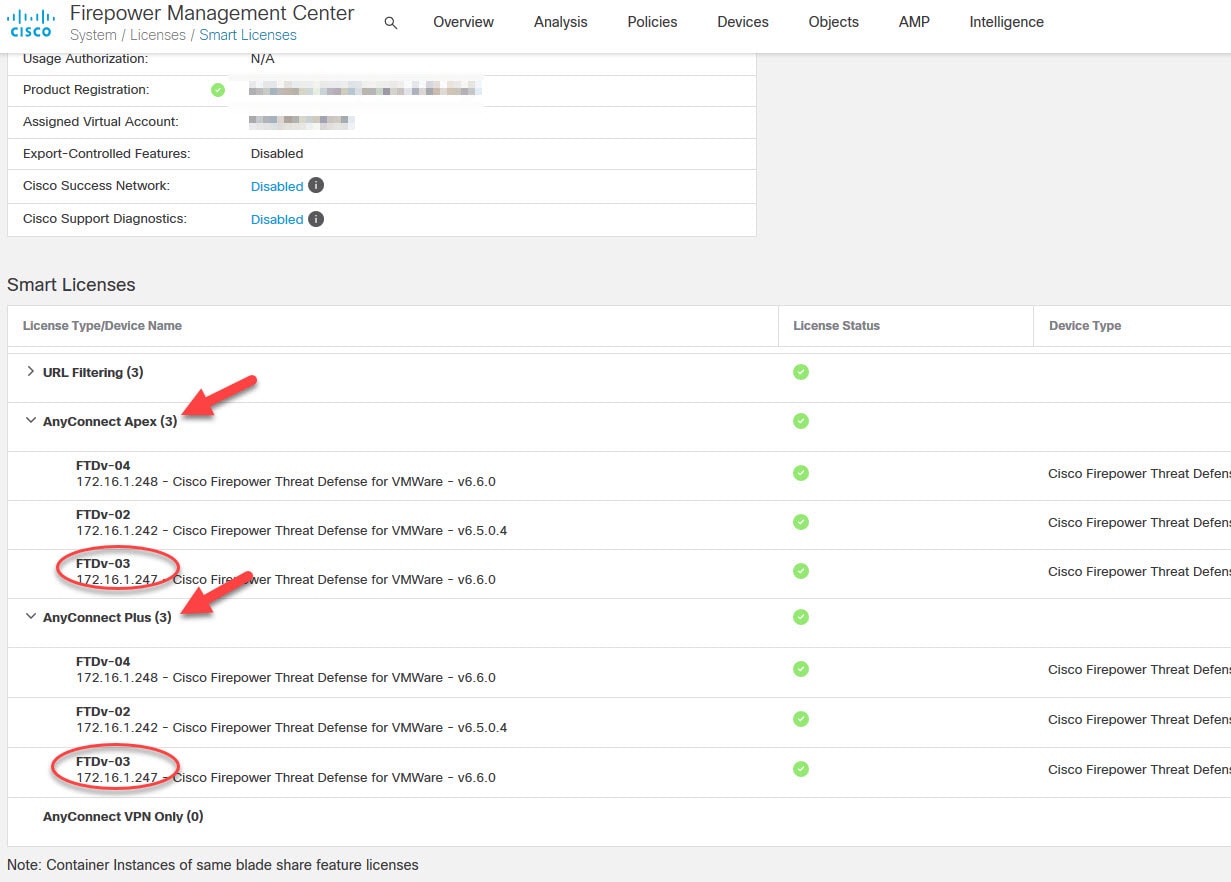
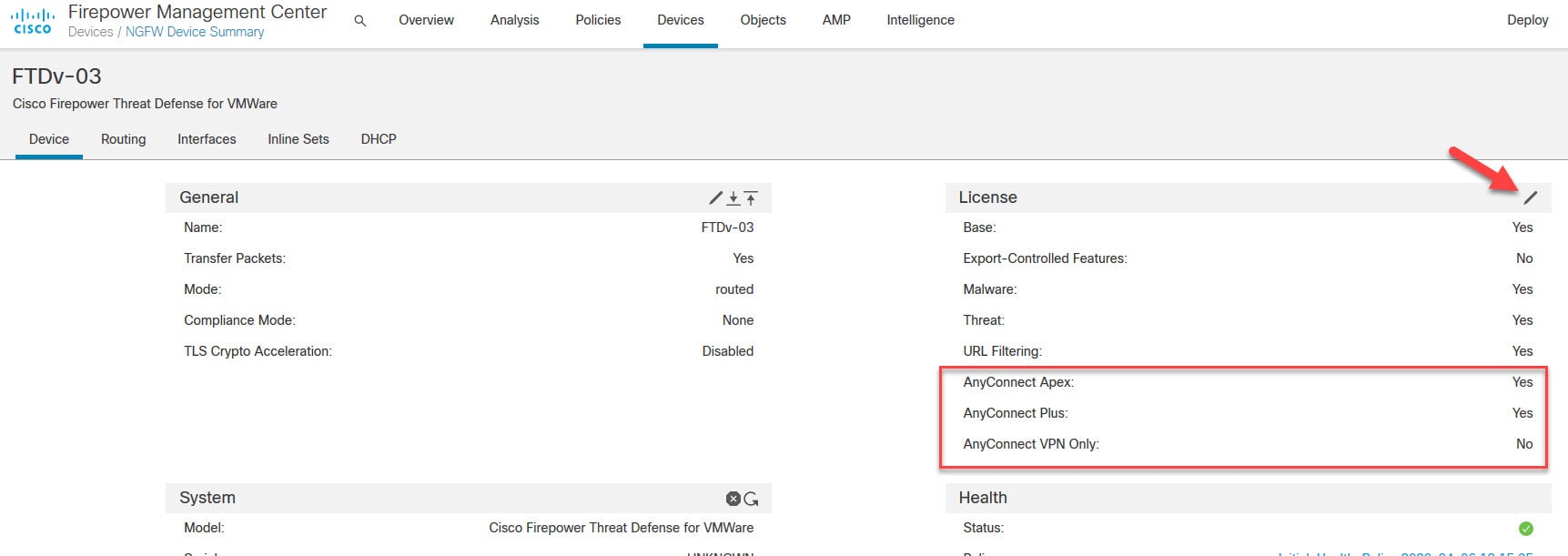
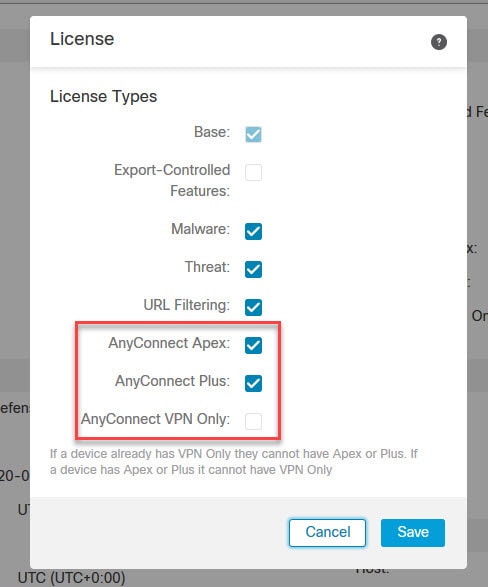
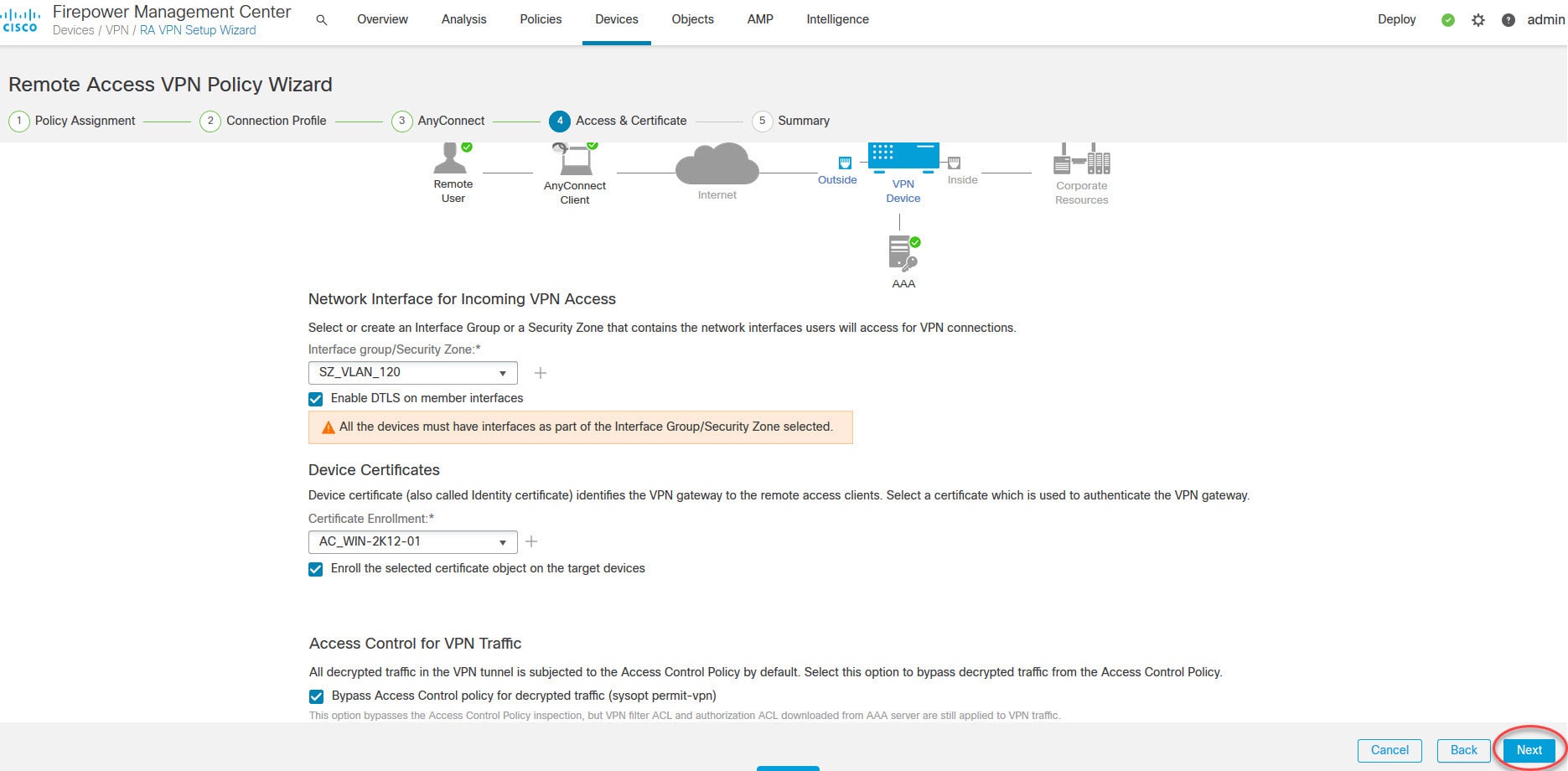
You should see the licenses associated to that FTD in the License section. If they are not enabled on that device, click on the pencil icon and tick the boxes next to the interested licenses.
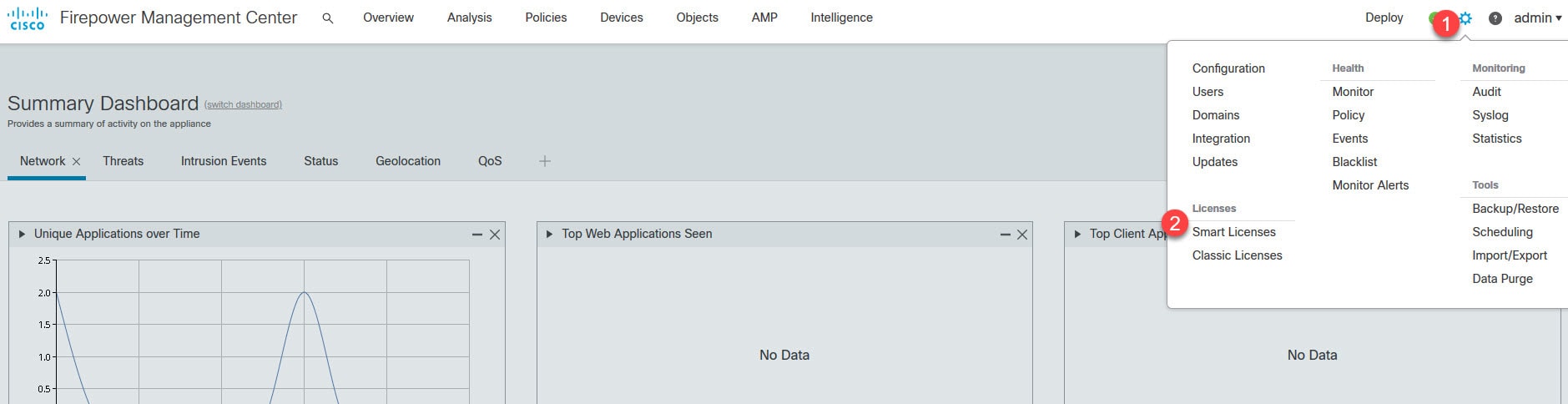
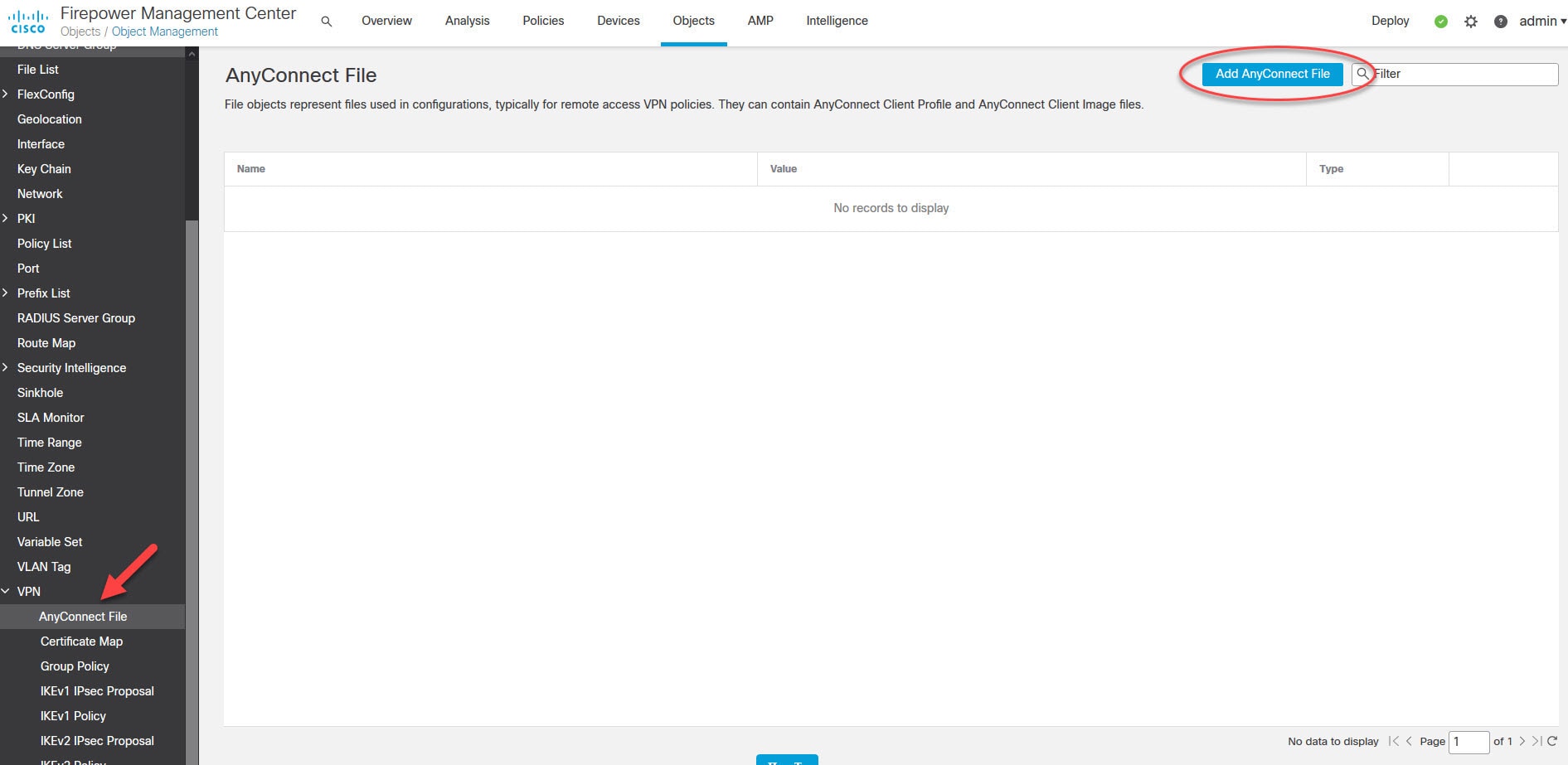
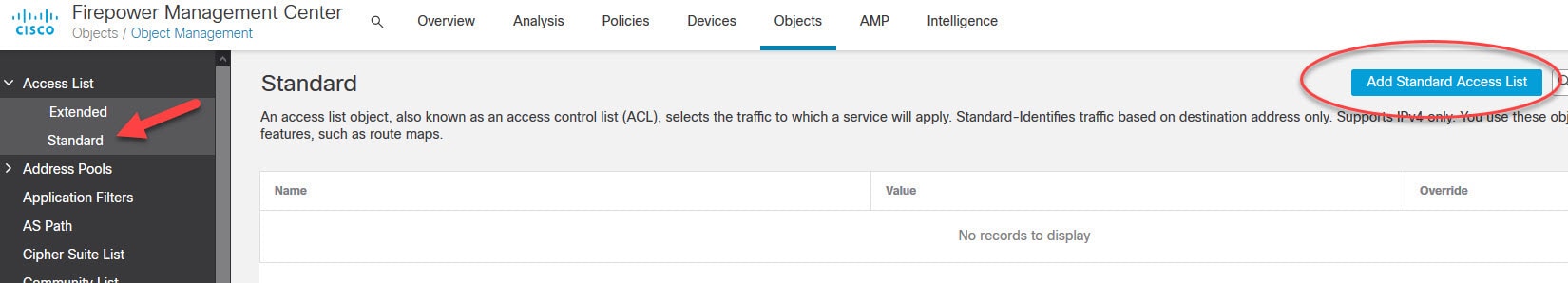
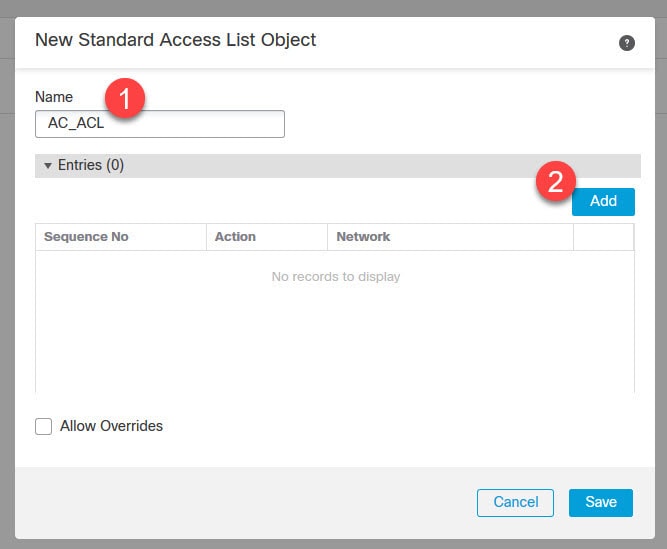
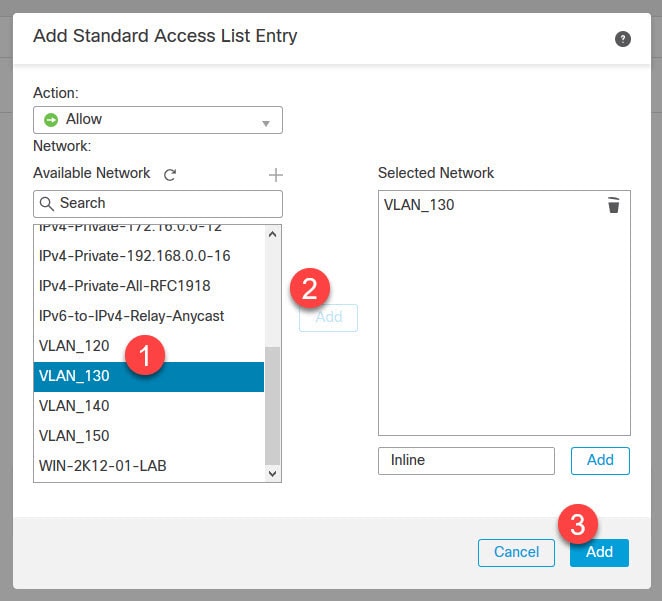
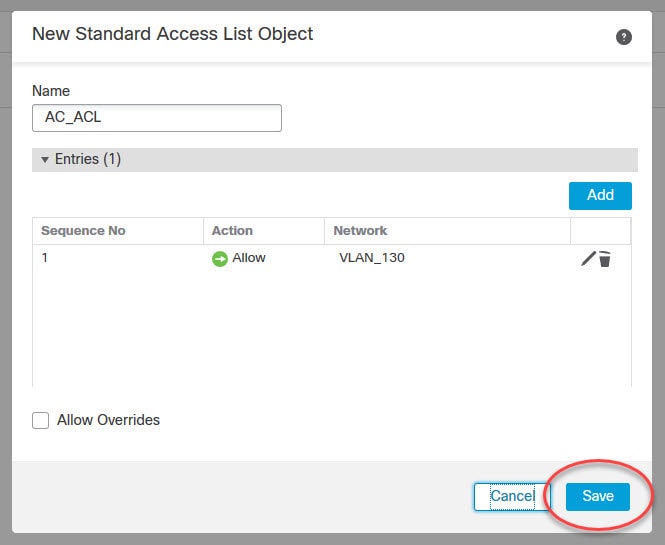
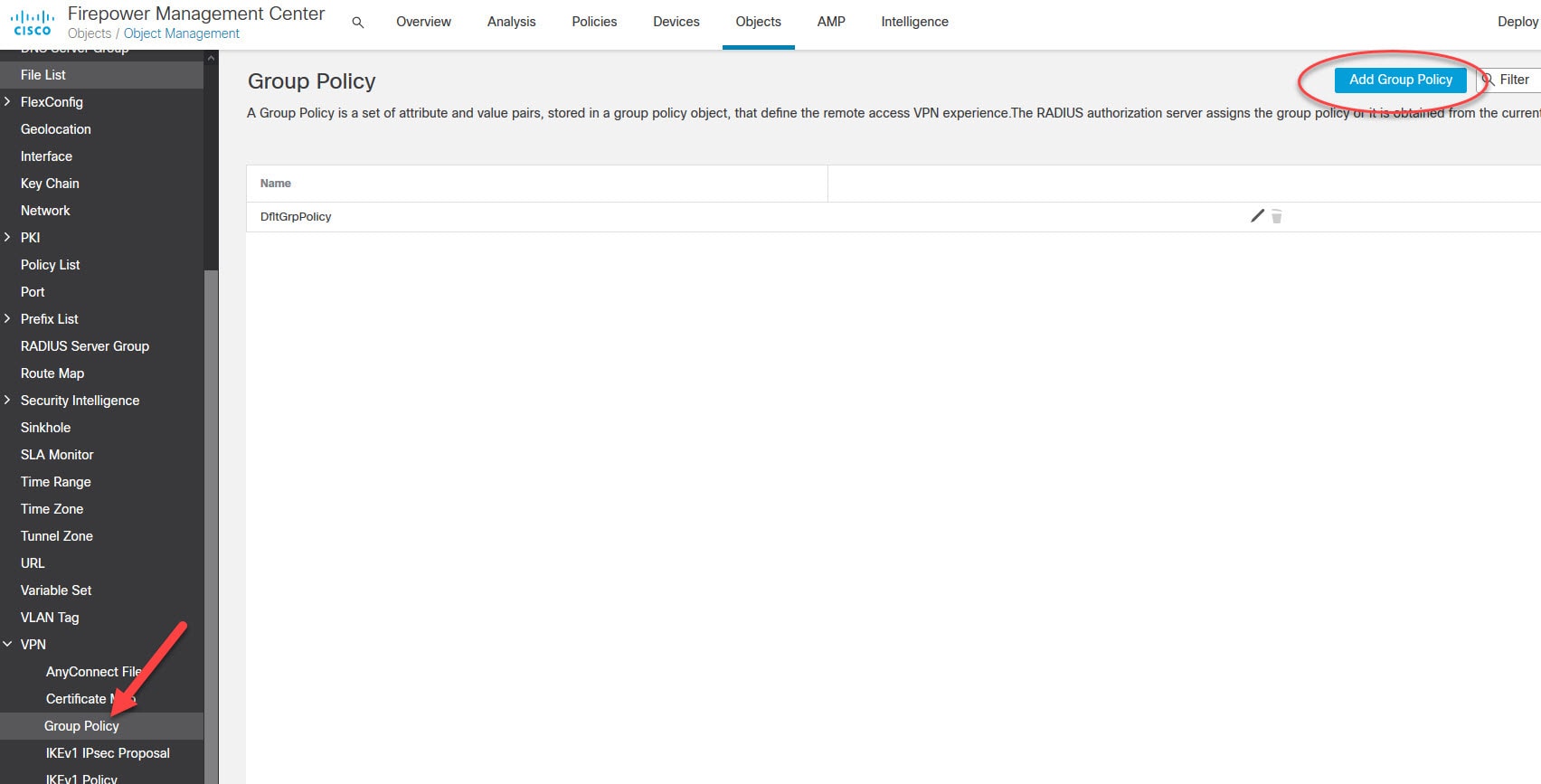
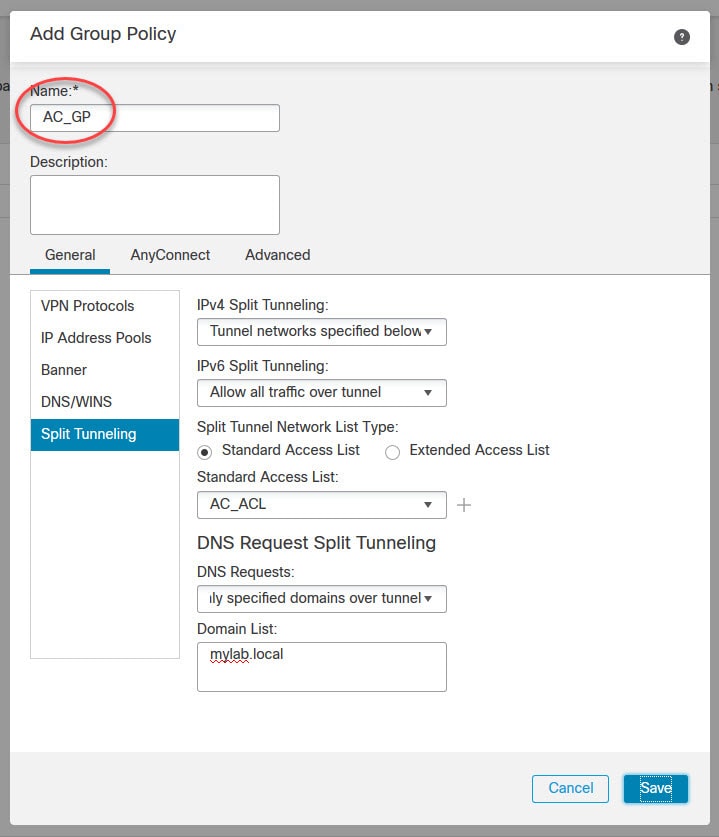
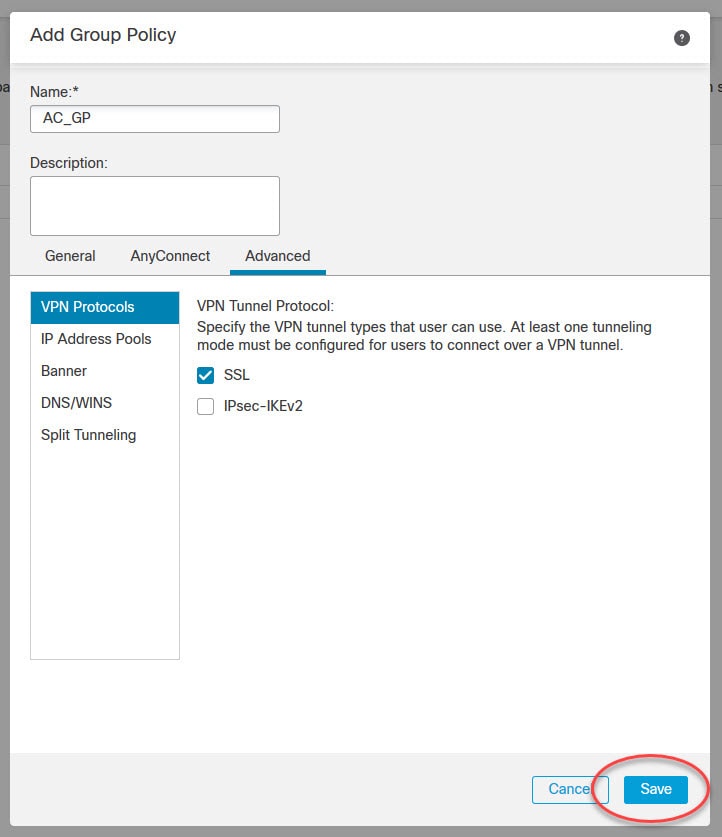
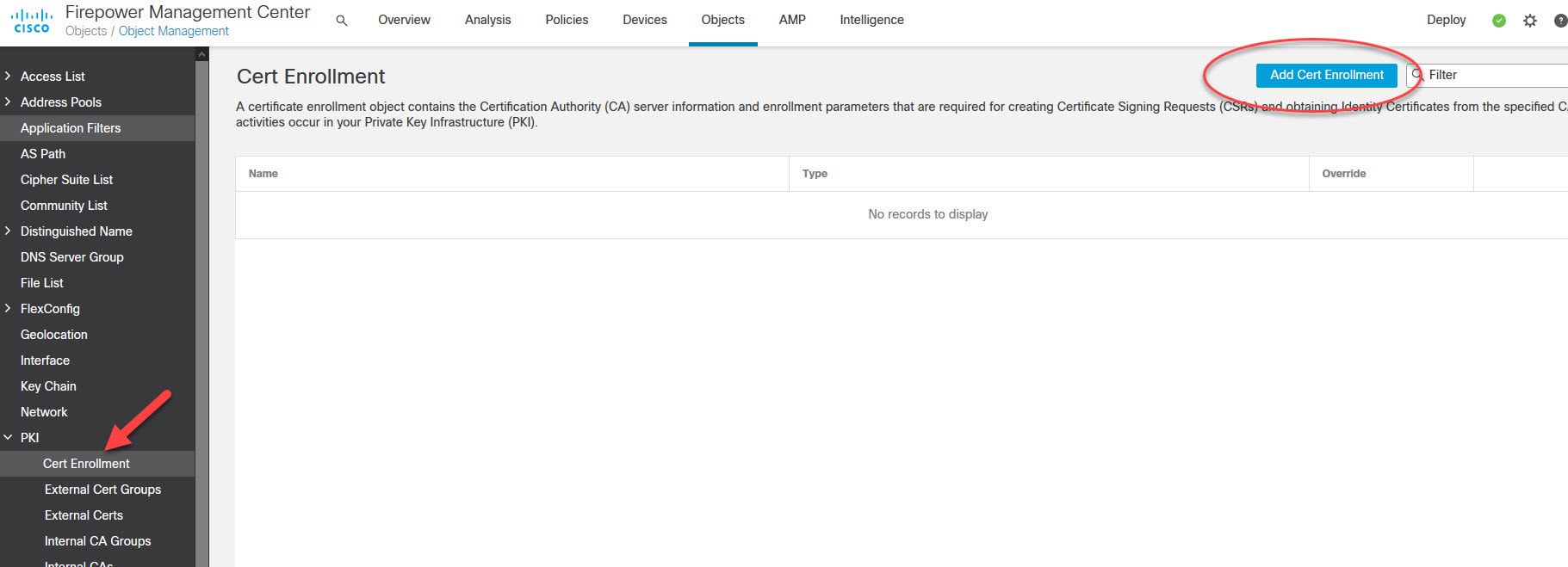
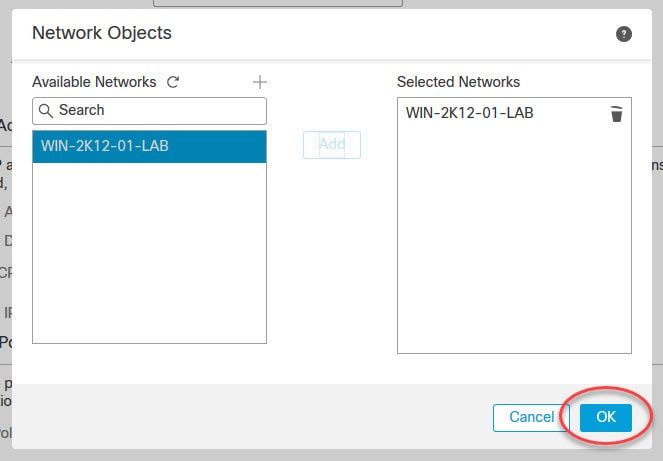
Now let's move to objects management section to create some objects that we need to configure AnyConnect SSL VPN in FMC.
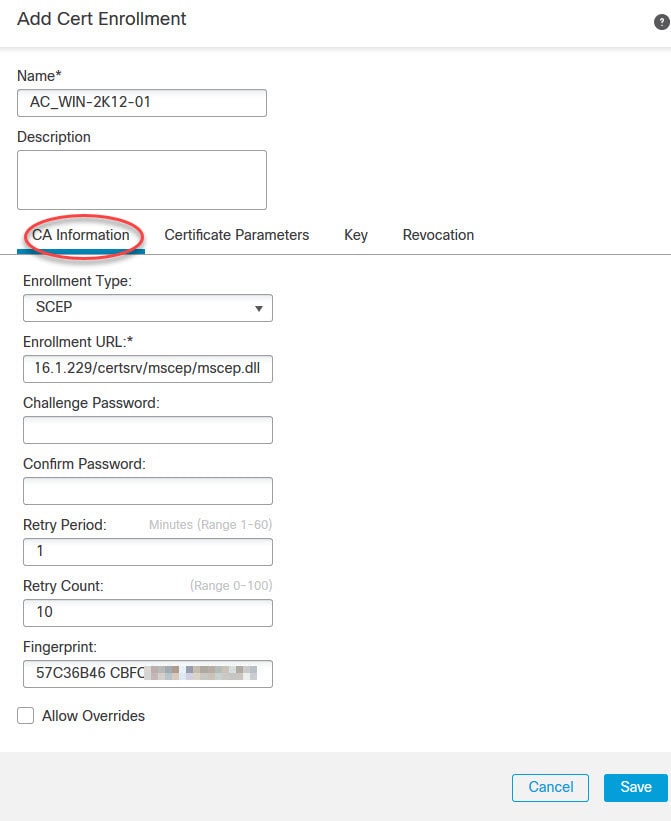
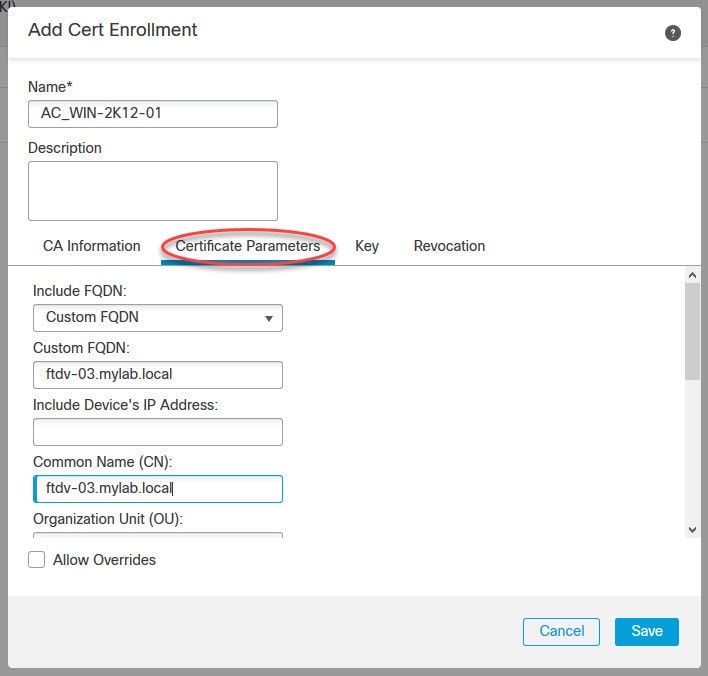
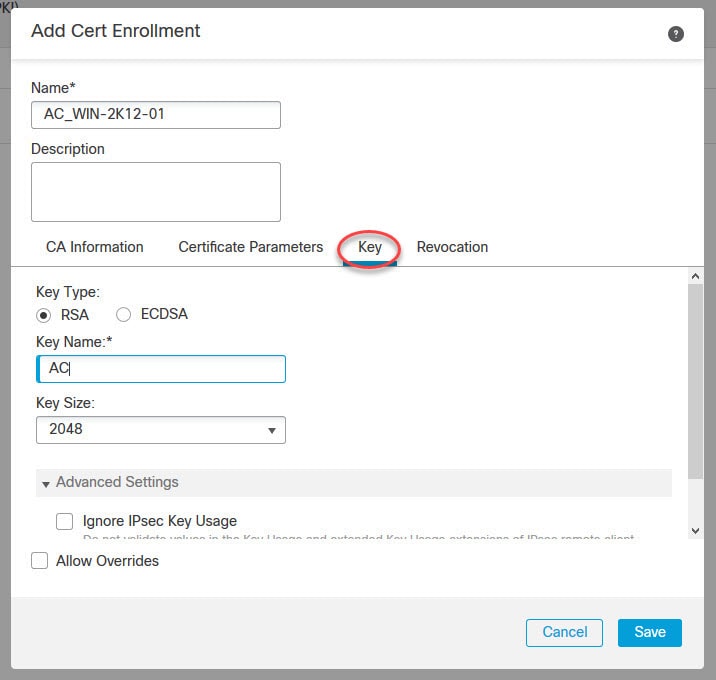
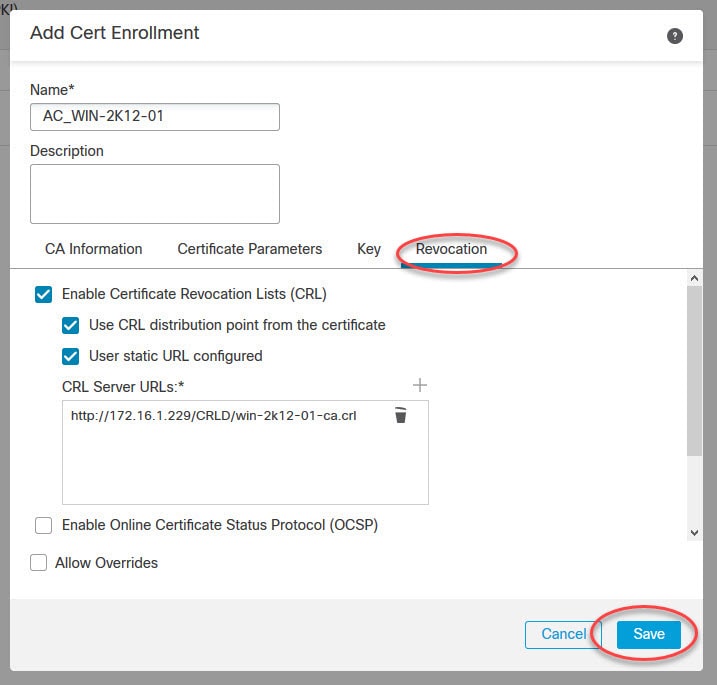

Hi, Can you please show how to configure Dynamic Split Tunneling Using FlexConfig, I want send/excluse FDQN based urls rather than IP address in split tunnel.
I will do my best to put something in in the next coming few weeks. You might want to subscribe to my newsletter to ensure you get the latest posts updates.