In this post you will see what could be the root cause of getting the "WARNING: The ID certificate associated with trust-point contains an Extended Key Usage (EKU) extension but without the Server Authentication purpose which is required for SSL use." message on the ASA when you try to associate a trust point to an interface, and how to fix it.
In this mini lab I have an ASA with a couple of trust points, one is just contains a root CA certificate imported and the other one is with both a root CA certificate and an identity certificate issued by that root CA. This trust point is called AC_TP_NEW, and it was configured to enrol via SCEP protocol against a Microsoft Windows 2012 R2 server to be used for AnyConnect Management Tunnel.
So far so good, no issues till here at all, the certificates have been imported successfully. However, when I went to associated the AC_TP_NEW trust point to the outside interface for SSL services, the ASA returned the "WARNING: The ID certificate associated with trust-point AC_TP_NEW contains an Extended Key Usage (EKU) extension but without the Server Authentication purpose which is required for SSL use." message.
Reading the message above it clearly states that the certificate I was trying to associate to the outside interface does not have the server authentication purpose in the EKU extension. Windows server by default uses the IPSec (Offline request) template to issue the certificates to the network devices through SCEP. So, I went to check the properties of the IPSec (Offline request) template, and in fact, the server authentication purpose was not there.
To fix this issue, I duplicated the IPSec (Offline request) template, added the server authentication purpose, and then renamed it as NDES. After that, I went to the registry editor and changed the default SCEP template to be NDES, then I restarted the IIS services. Once that all has done, the warning message was gone. Following are the relevant steps:
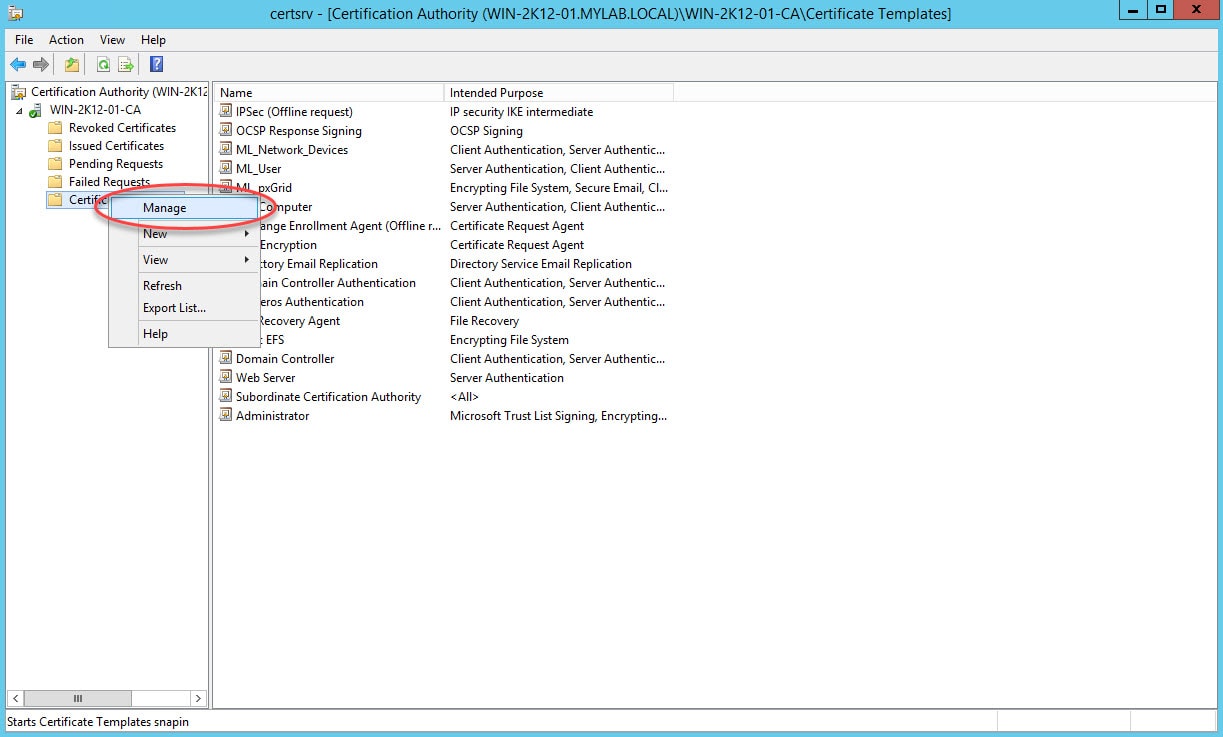
Step 1: Go to Certification Authority manager, right click on Certificate Templates and click Manage :
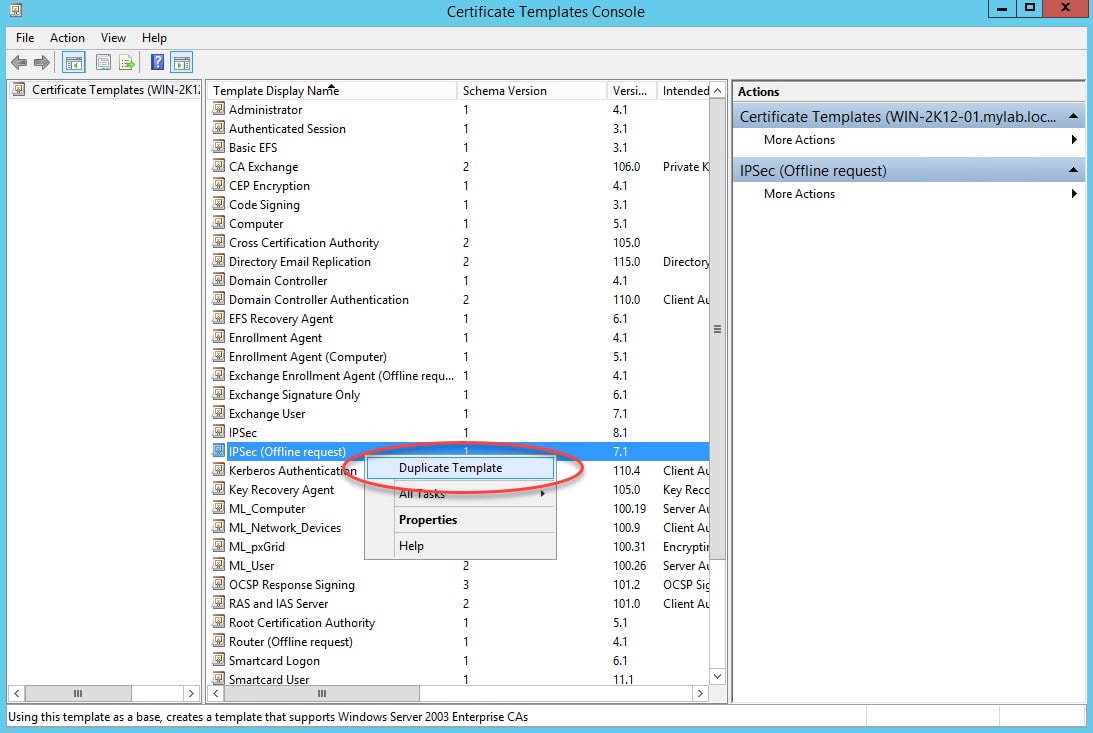
Step 2: Right click on the IPSec (Offline request) template and click Duplicate Template:
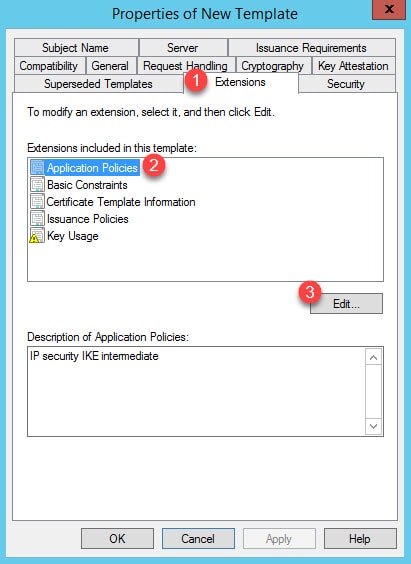
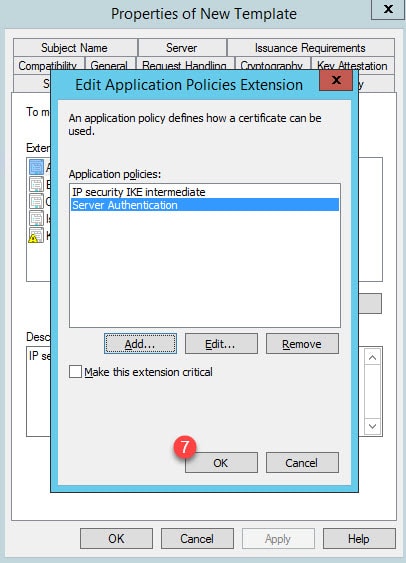
Step 3: Go to Extensions > Applications Policies > Edit:
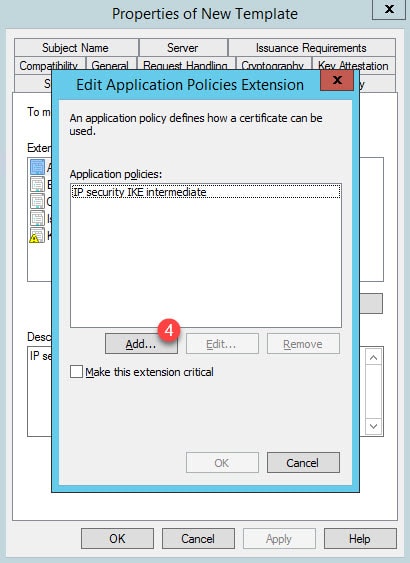
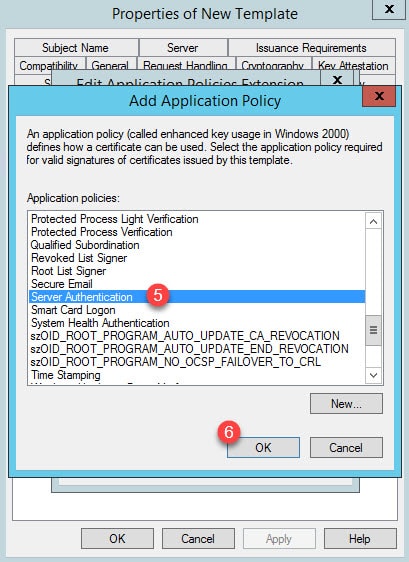
Step 4: Click Add and select Server Authentication from the list:
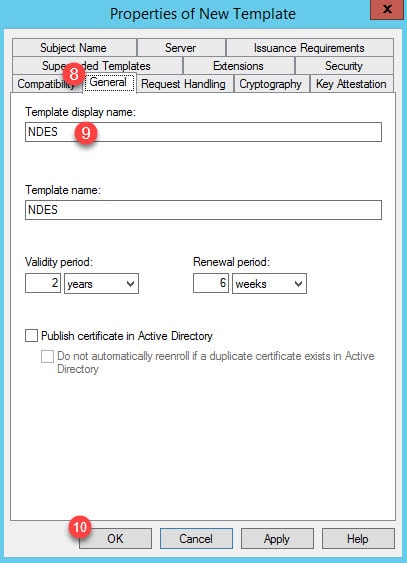
Step 5: Go to the General tab to rename the new template and give it a name:
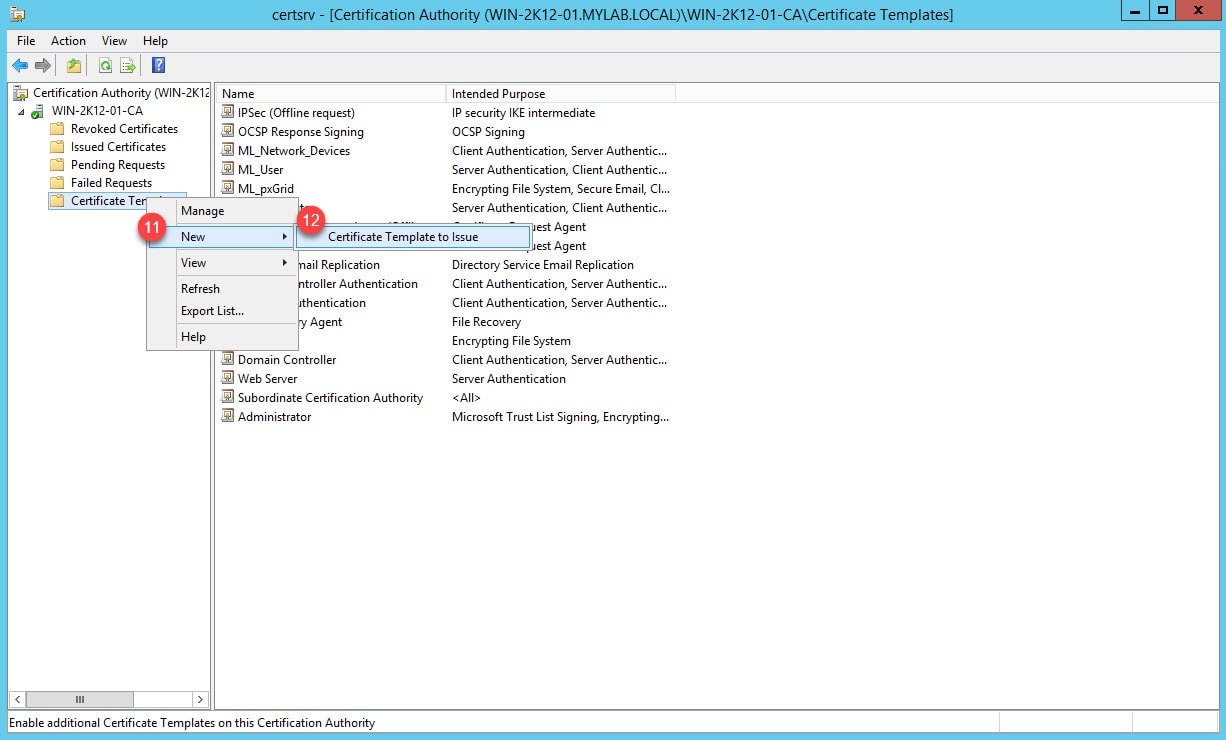
Step 6: Go back to the Certification Authority manager, right click on Certificate Templates > New > Certificate Template to Issue:
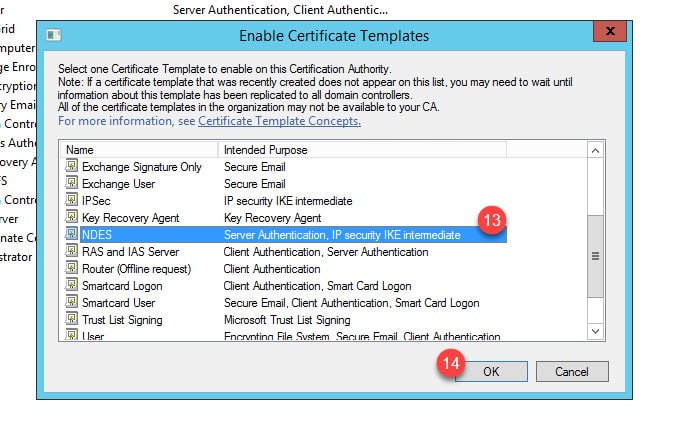
Step 7: Select the new template from the list and click OK:
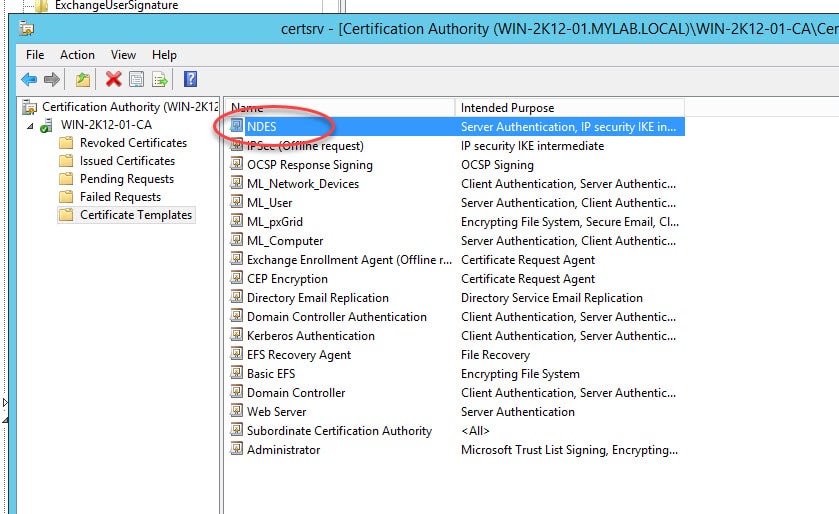
You should see the newly imported template in the Certificate Templates list:
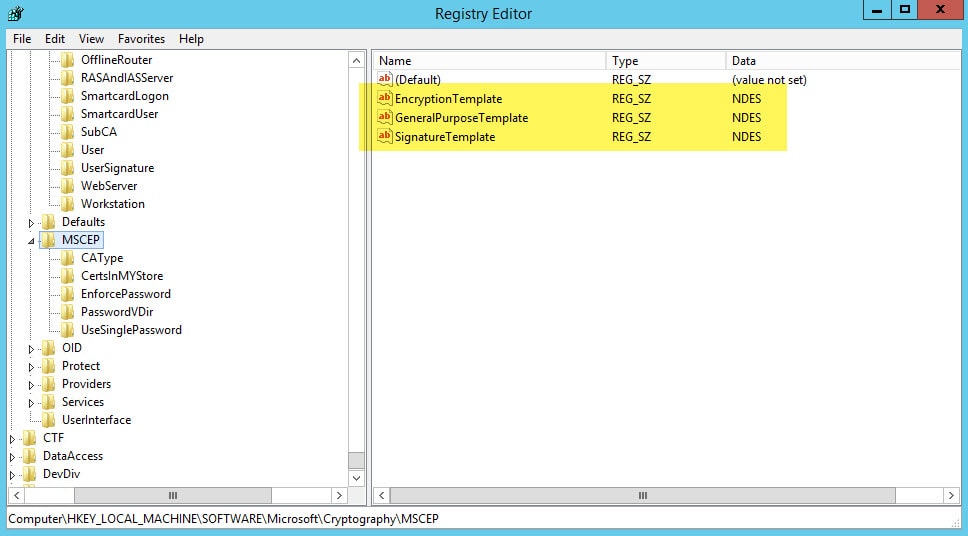
Step 8: Go to the Registry Editor > HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP, and change the REG_SZ value to be the name of the new template:
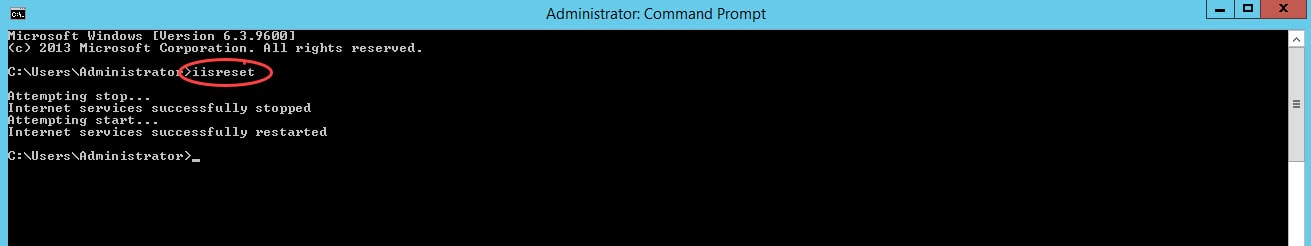
Step 9: To restart the IIS services, you can do that by going to the IIS manager and select restart, or through CMD. In this example I am using CMD to restart the services:
This wraps up this post about the "WARNING: The ID certificate associated with trust-point contains an Extended Key Usage (EKU) extension but without the Server Authentication purpose which is required for SSL use." message.
Thank You for reading!