In this post I will share with you how to fix AnyConnect Management Tunnel Disconnected (connect failed) error, but before jumping in here is a quick heads up on what AnyConnect Management Tunnel is.
AnyConnect Management Tunnel is a very cool feature that allows us to do some maintenance works on the remote endpoints without asking the users any interaction. AnyConnect Management Tunnel leverages the Trusted Network Detection (TND) feature. This means it will automatically establish a management tunnel as soon as a laptop is connected to an untrusted network. But it will also establish the management tunnel as soon as the logged user logs off, or terminates the user tunnel.
Here is how it works, the management tunnel will be terminated when the user tunnel is initiated and active, and it will reconnect when the user tunnel is terminated. It is kind of a secure backdoor to keep the corporate devices accessible by the IT support team, and by the corporate resources. The corporate resources might be used to push updates, patches, software upgrade etc to the laptops.
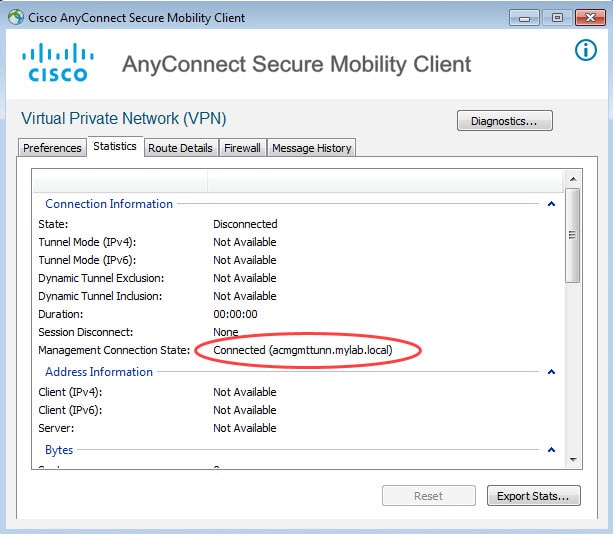
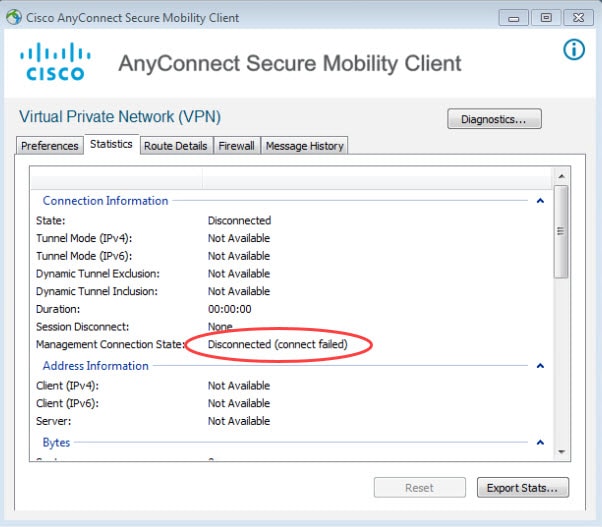
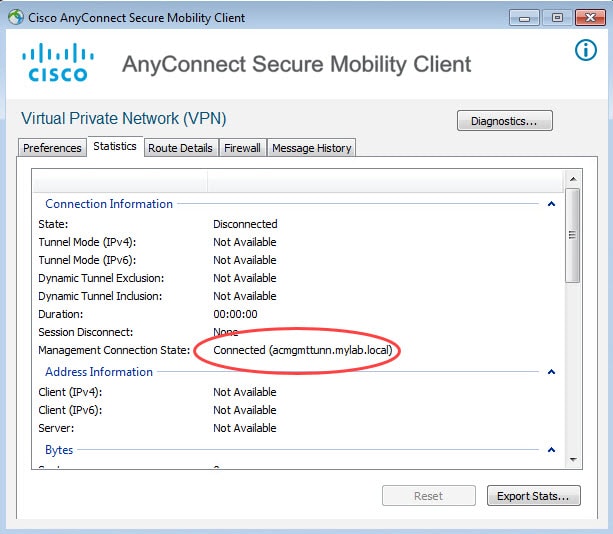
When AnyConnect Management Tunnel is established it will show as Connected along with the firewall FQDN as shown in the first pic below. However, sometimes the management tunnel might fail to establish for different reasons. When it fails it would show as Disconnected (connect failed).
I will cover AnyConnect Management Tunnel complete configuration in a separate post. However, in this post as mentioned we will only focus on AnyConnect Management Tunnel Disconnected (connect failed) error, and how to fix it. Let's take a look together!
Here is how a functional AnyConnect Management Tunnel looks like:
And here is how it looks like when it failed establishing the tunnel with the error message Disconnected (connect failed):
By looking at the ASA management tunnel group policy and tunnel group, everything seems to be ok:
group-policy Mgmt_GP internal group-policy Mgmt_GP attributes dns-server value 172.16.1.229 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelall default-domain value mylab.local client-bypass-protocol enable anyconnect-custom ManagementTunnelAllAllowed value true webvpn anyconnect profiles value Mgmt-Profile type vpn-mgmt ! tunnel-group Mgmt_TG type remote-access tunnel-group Mgmt_TG general-attributes address-pool AC default-group-policy Mgmt_GP tunnel-group Mgmt_TG webvpn-attributes authentication certificate group-alias Mgmt_TG enable group-url https://acmgmttunn.mylab.local/Management enable without-csd
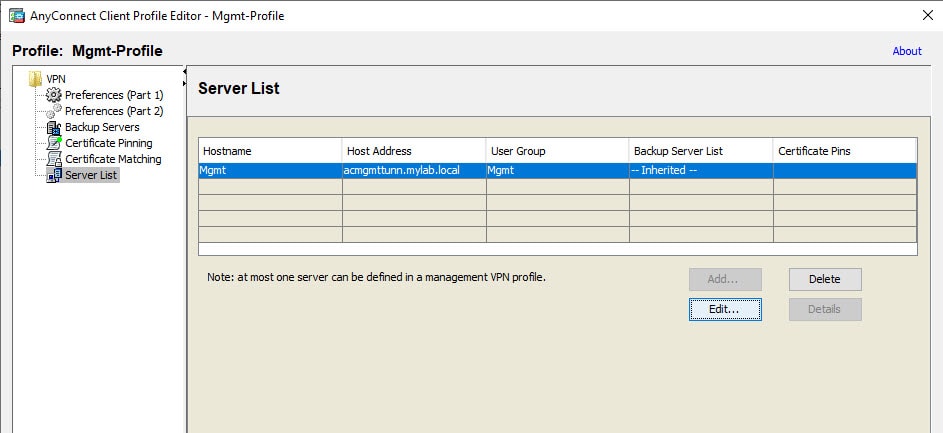
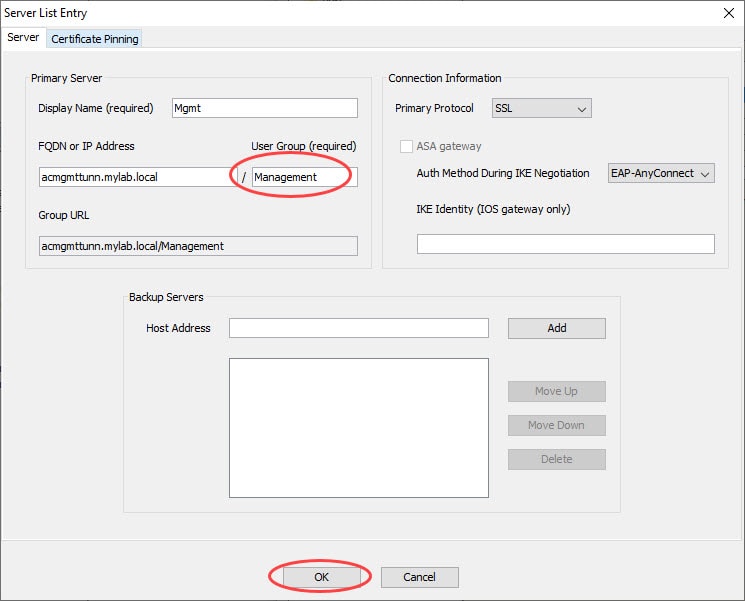
And here is the interested part of the AnyConnect Management Tunnel profile that is causing this failure:
As you could probably already noticed, there is an inconsistency in the tunnel group group URL configuration between the configs on the ASA and the one on the profile. On the ASA we can see the group URL is configured as Management, however, on the profile itself it is configured as Mgmt. This inconsistency causes the tunnel to fail.
The fix can be whether by changing the group URL configuration on the ASA to be the same as the one configured on the AnyConnect Management Tunnel profile. Or, by editing the one configured in the profile to be the same as the one on the ASA.
tunnel-group Mgmt_TG webvpn-attributes no group-url https://acmgmttunn.mylab.local/Management enable group-url https://acmgmttunn.mylab.local/Mgmt enable
Or
After amending one of the above changes, the management tunnel started working again:
This wraps up this post about AnyConnect Management Tunnel Disconnected (connect failed) error.
Thank you for reading!