When we configure a site to site VPN in FMC, on the IKE tab, we see an authentication type option to use a Preshared Automatic Key. In this post we will see what that option does for us. FMC as you know can manage multiple FTD appliances. The appliances that would be managed by the FMC do not necessarily have to be located in the same domain. For instance, we might have an FTD in London and another in New York, both managed by the same FMC.
In that case, you might want to set up a site to site VPN between those two FTD appliances. Now because both of them are managed by the same FMC, the FMC can push whatever policies or settings to those appliances. Here where the Preshared Automatic Key would be used.
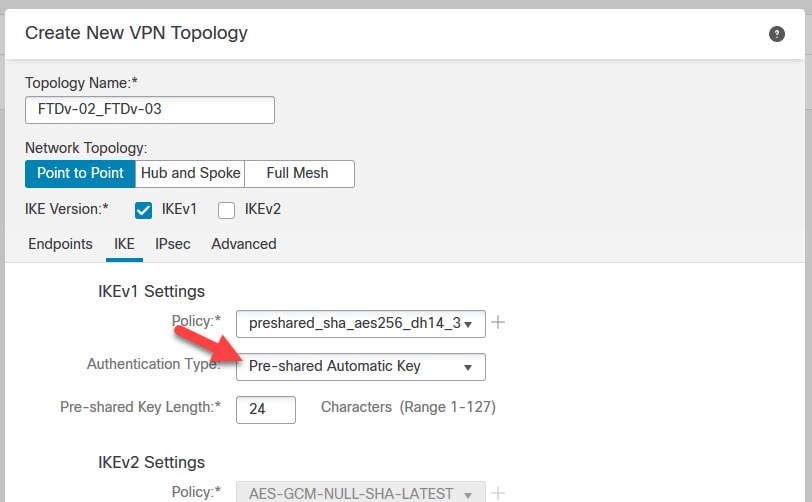
When we use the Preshared Automatic Key in our VPN topology, we are simply saying, hey FMC, take care of generating a preshared key for this VPN, and push it to the interested peers. We can set how long the Preshared Automatic Key can be, and the FMC will mix it with upper and lower characters along with numbers.
The Preshared Automatic Key can't be used if one of the two peers is not managed by the FMC, since as you could guess, the FMC would not be able to push any settings to the external peer.
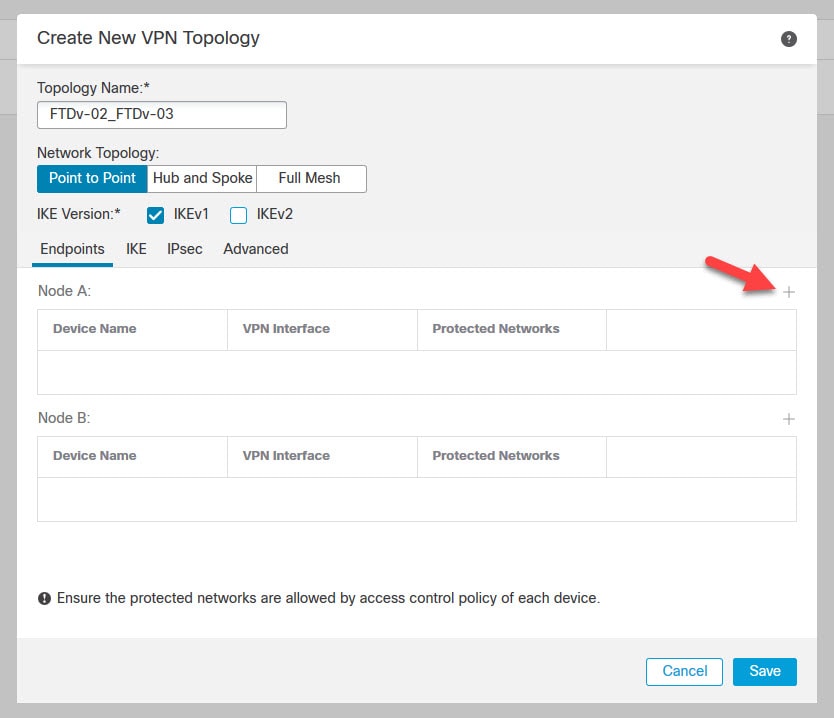
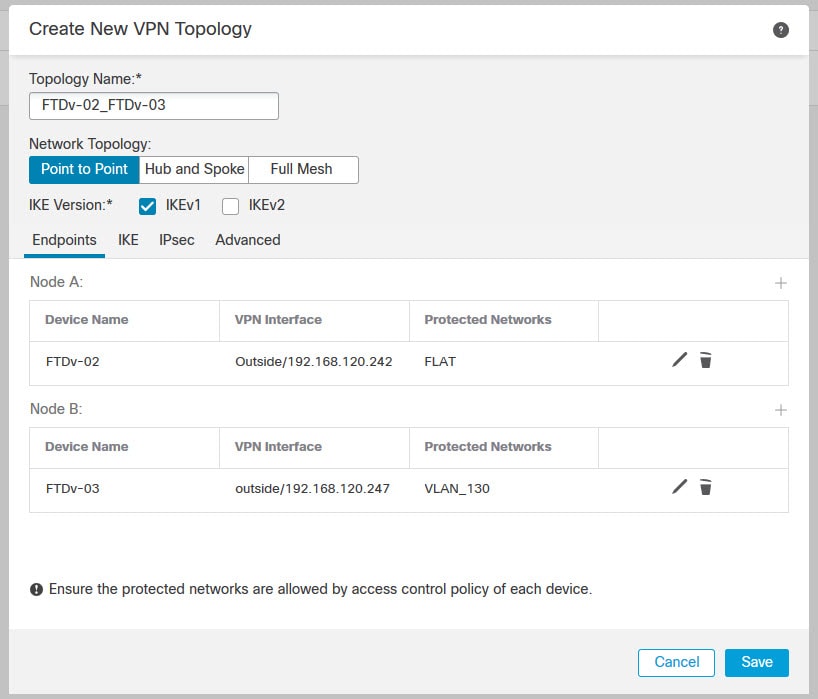
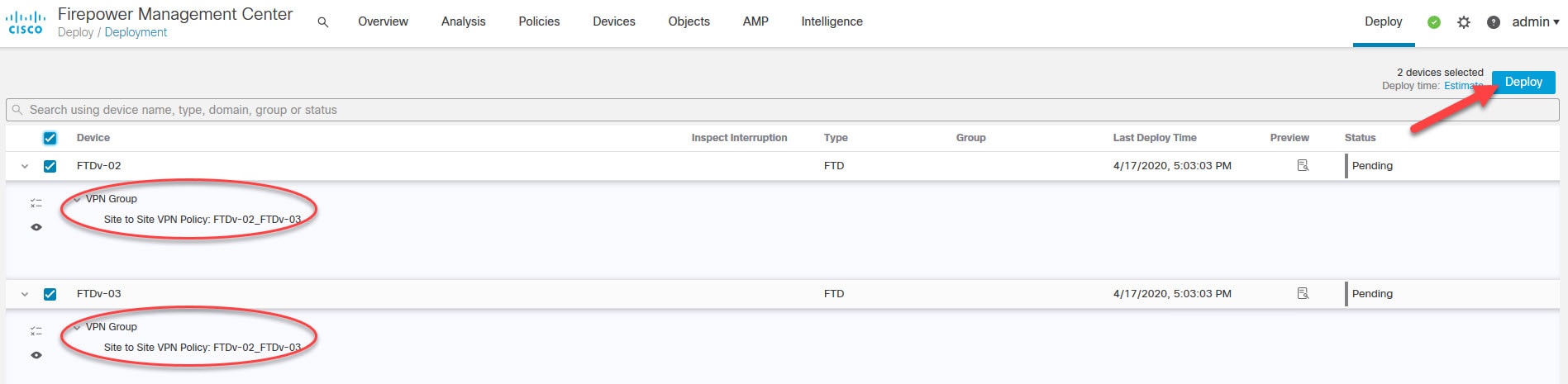
In this lab we will have two peers one is called FTDv-02 and another called FTDv-03. We will set up a site to site VPN between them and we will use the Preshared Automatic Key. Once we deploy the configuration from the FMC, we will go to check how this Preshared Automatic Key looks like on both appliances.
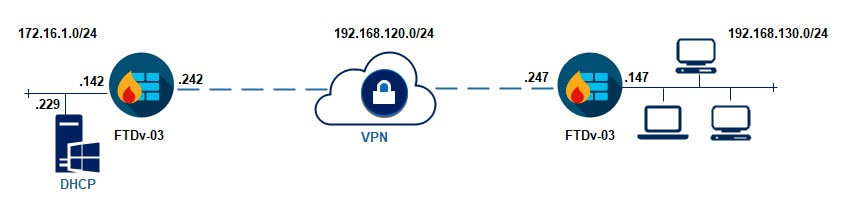
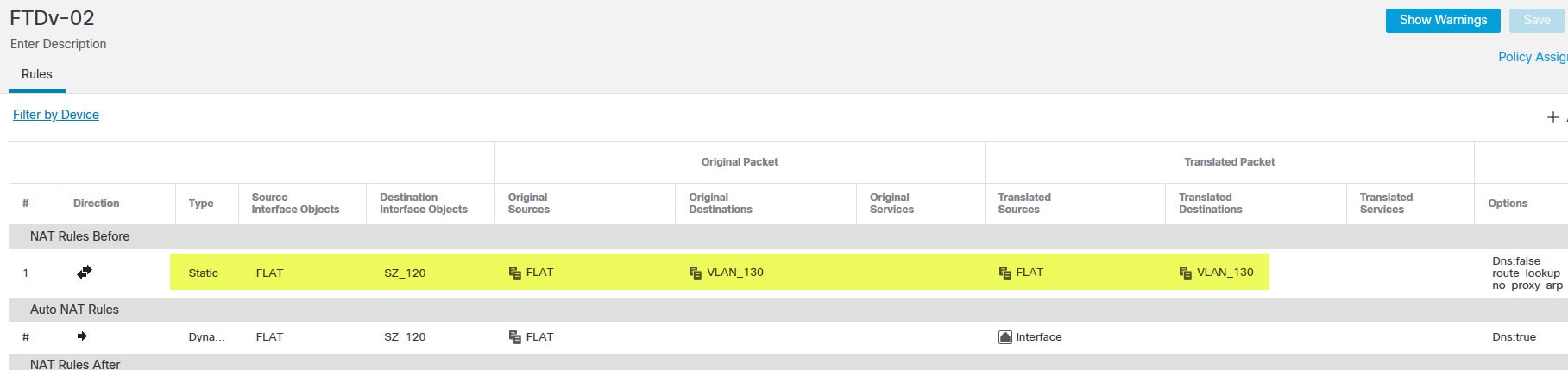
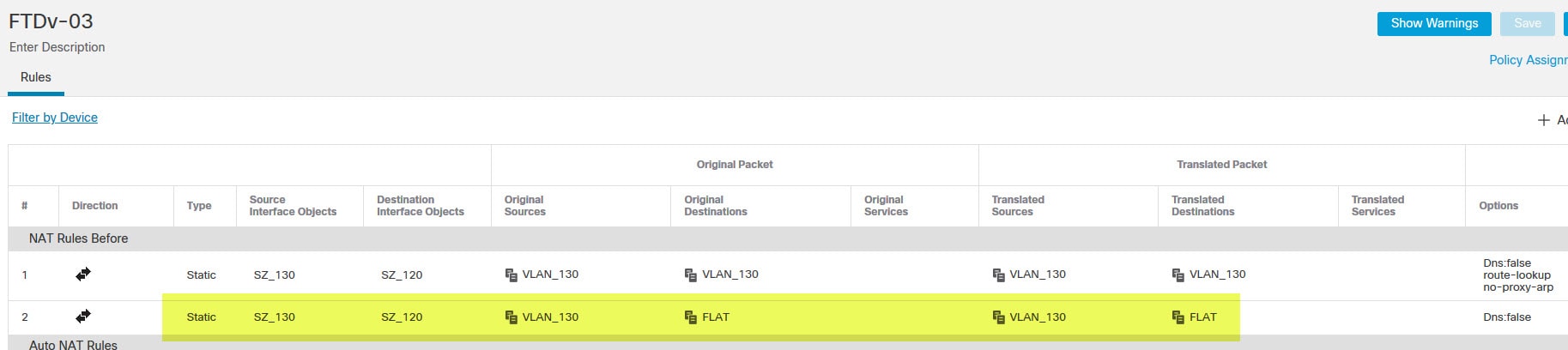
The lab will be focusing only on the VPN configuration part. The NAT exemption rules and all IP addressing have been already configured. You will see on the topology a DHCP server behind the FTDv-03. The reason why I put this server in the topology is because the next post will show how to configure DHCP Relay in the FMC.
Topology
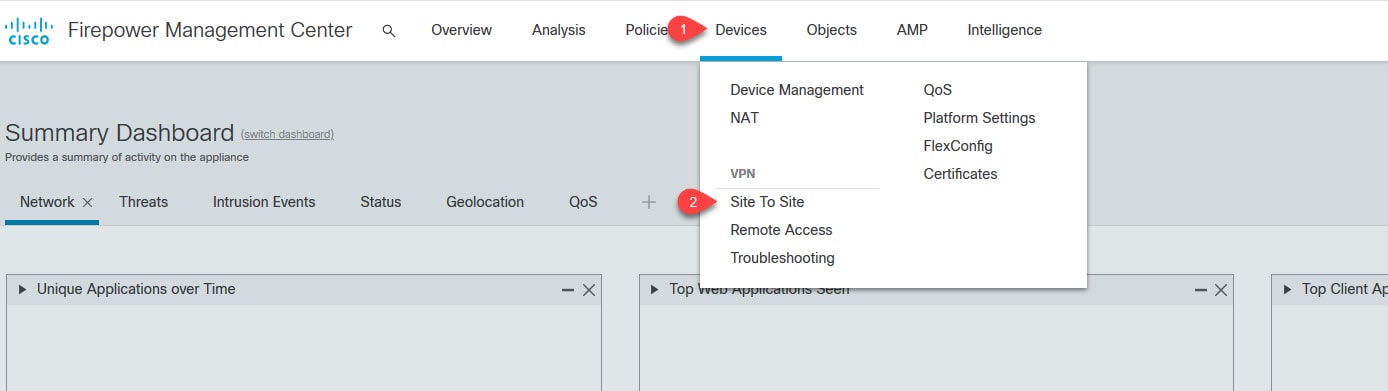
Step 1: Configure the site to site VPN
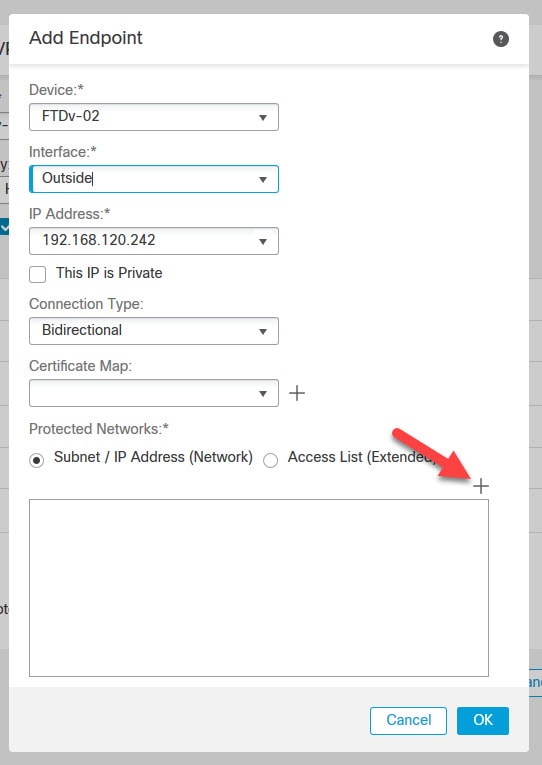
Go to Devices > VPN > Site to Site
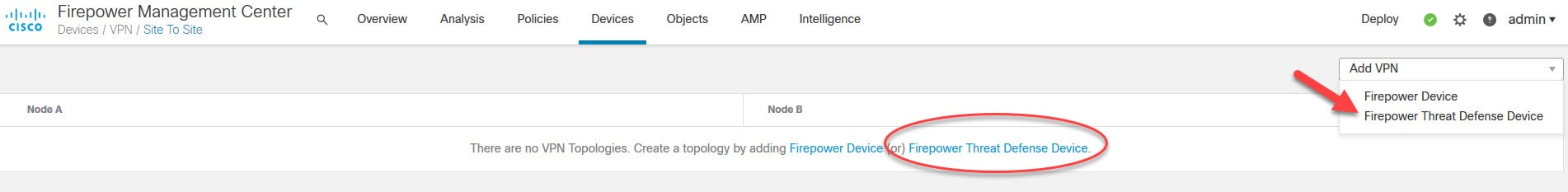
Go to Add VPN > Firepower Threat Defense Device
Configuration Verification
ftdv-03# sh run tunnel-group | be ipsec
tunnel-group 192.168.120.242 type ipsec-l2l
tunnel-group 192.168.120.242 general-attributes
default-group-policy .DefaultS2SGroupPolicy
tunnel-group 192.168.120.242 ipsec-attributes
ikev1 pre-shared-key *****
more system:running-config
<< omitted >>
tunnel-group 192.168.120.242 type ipsec-l2l
tunnel-group 192.168.120.242 general-attributes
default-group-policy .DefaultS2SGroupPolicy
tunnel-group 192.168.120.242 ipsec-attributes
ikev1 pre-shared-key nZHYFx6uBOZMNUls0sFZNRdm
ftd-02# sh run tunnel-group | be ipsec
tunnel-group 192.168.120.247 type ipsec-l2l
tunnel-group 192.168.120.247 general-attributes
default-group-policy .DefaultS2SGroupPolicy
tunnel-group 192.168.120.247 ipsec-attributes
ikev1 pre-shared-key *****
more system:running-config
<< omitted >>
tunnel-group 192.168.120.247 type ipsec-l2l
tunnel-group 192.168.120.247 general-attributes
default-group-policy .DefaultS2SGroupPolicy
tunnel-group 192.168.120.247 ipsec-attributes
ikev1 pre-shared-key nZHYFx6uBOZMNUls0sFZNRdm
As you can see, the Preshared Key that was pushed by the FMC is 24 characters long. That's because in our IKEv1 Settings we left to the default Preshared Key length of 24.
This wraps up our post about the FMC Automatic Preshared Key.
Thank you for reading!