In my previous post “FMC external authentication with RADIUS” I showed you how to configure FMC access with RADIUS. In this post instead, I will show you how to configure FTD CLI access with RADIUS, we will use ISE as our RADIUS server. The configuration is very similar to what we have done in the FMC post, and the main difference will be how to bind the FMC External Authentication Object to the FTD device.
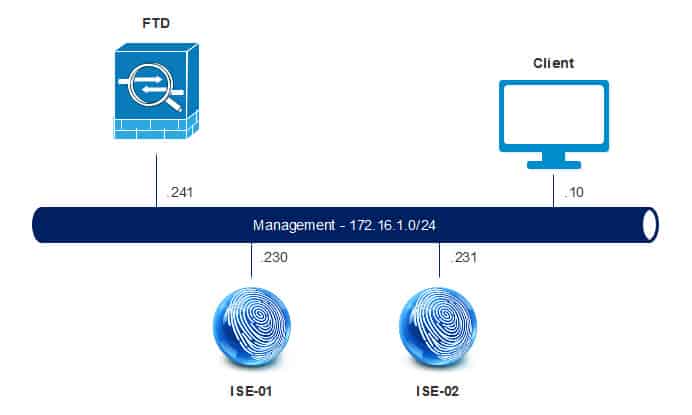
TOPOLOGY:
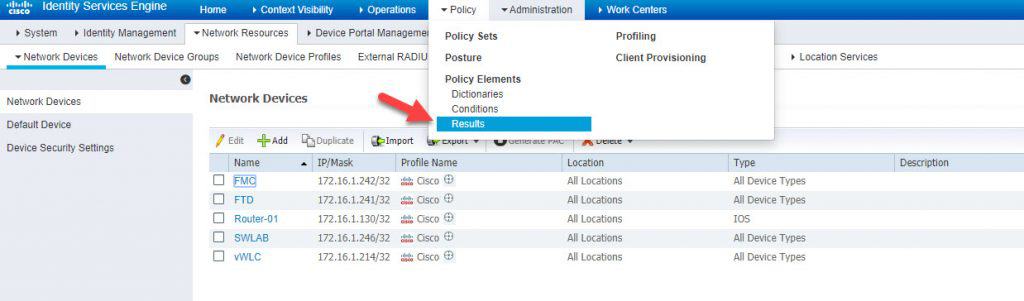
The configuration will be split into two parts, one for ISE and another for FMC. On ISE we need to add the FTD as a network device, configure the authZ profile and finally configure the policy set rules to match the traffic destined to the FTD device for CLI accesses. On FMC instead, we need to configure a new External Authentication Object that will be dedicated for FTD accesses, and then apply this new object to the FTD platform settings. Let’s see together how easy is going to be to configure FTD CLI access with RADIUS. We will start first with ISE configuration and then we will move on to FMC.
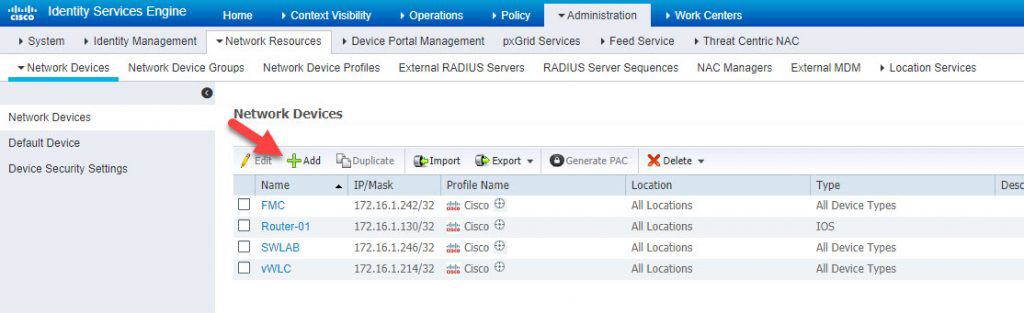
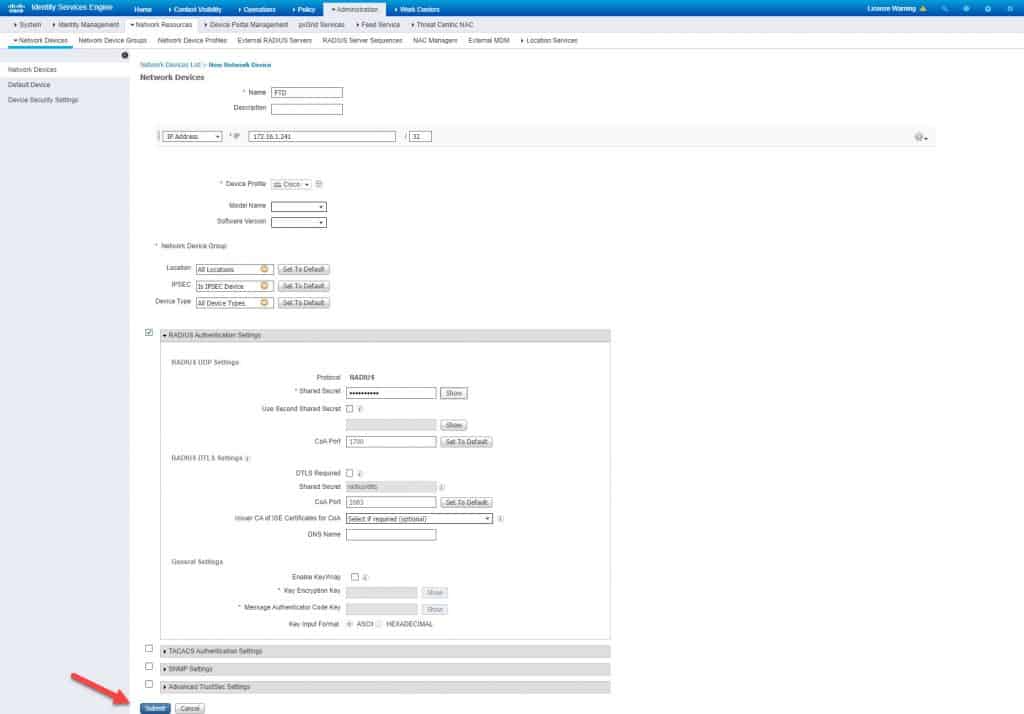
Step 1: Add FTD to the network devices
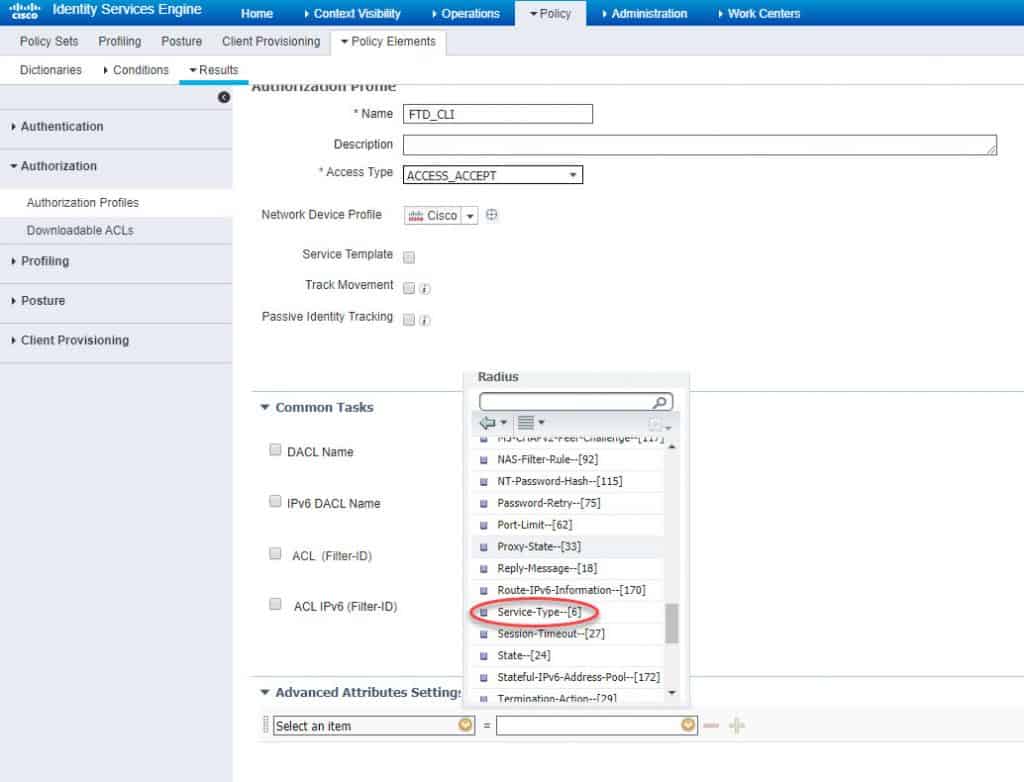
Step 2: Configure AUTHZ profile
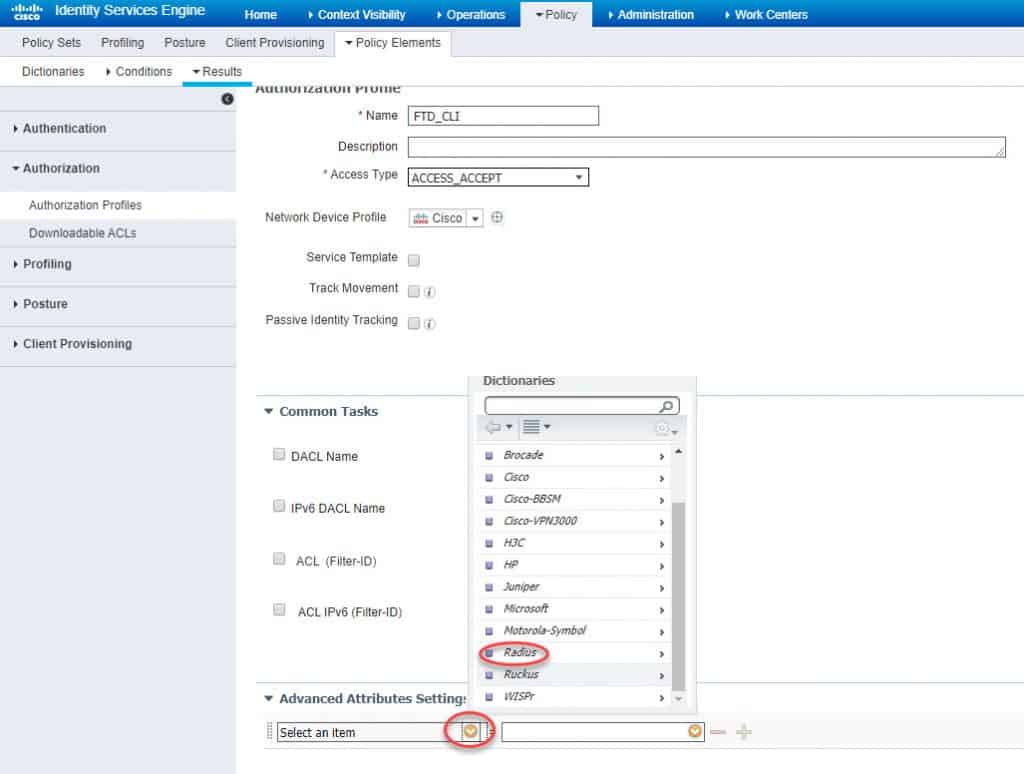
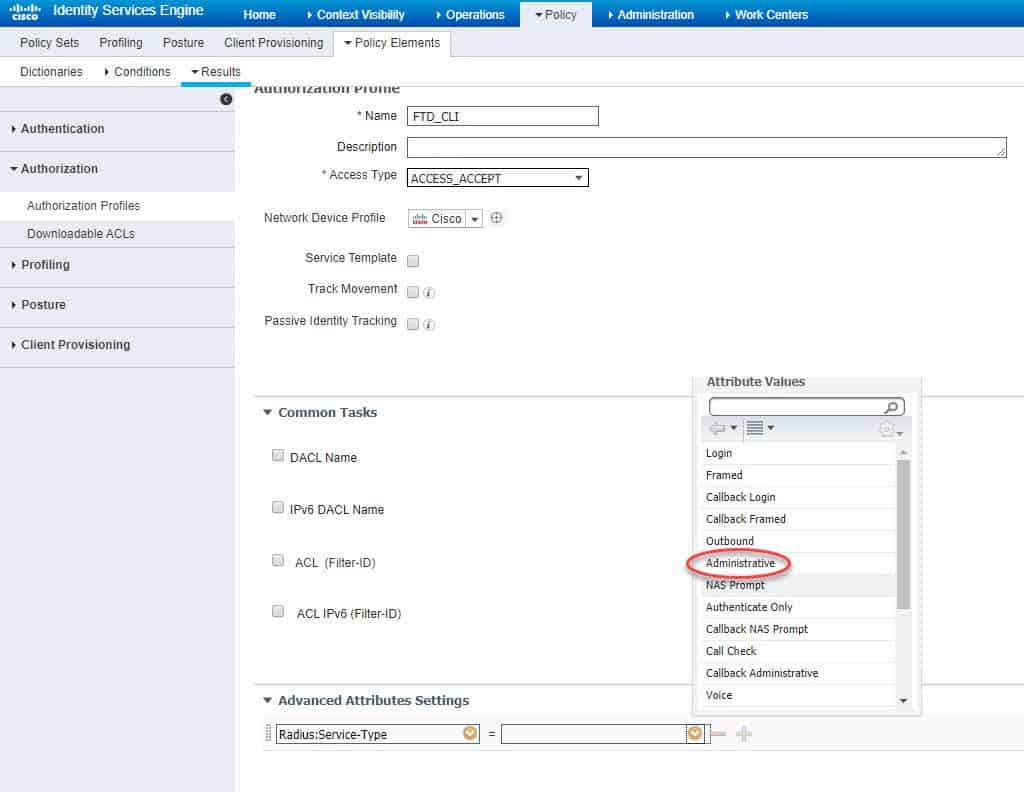
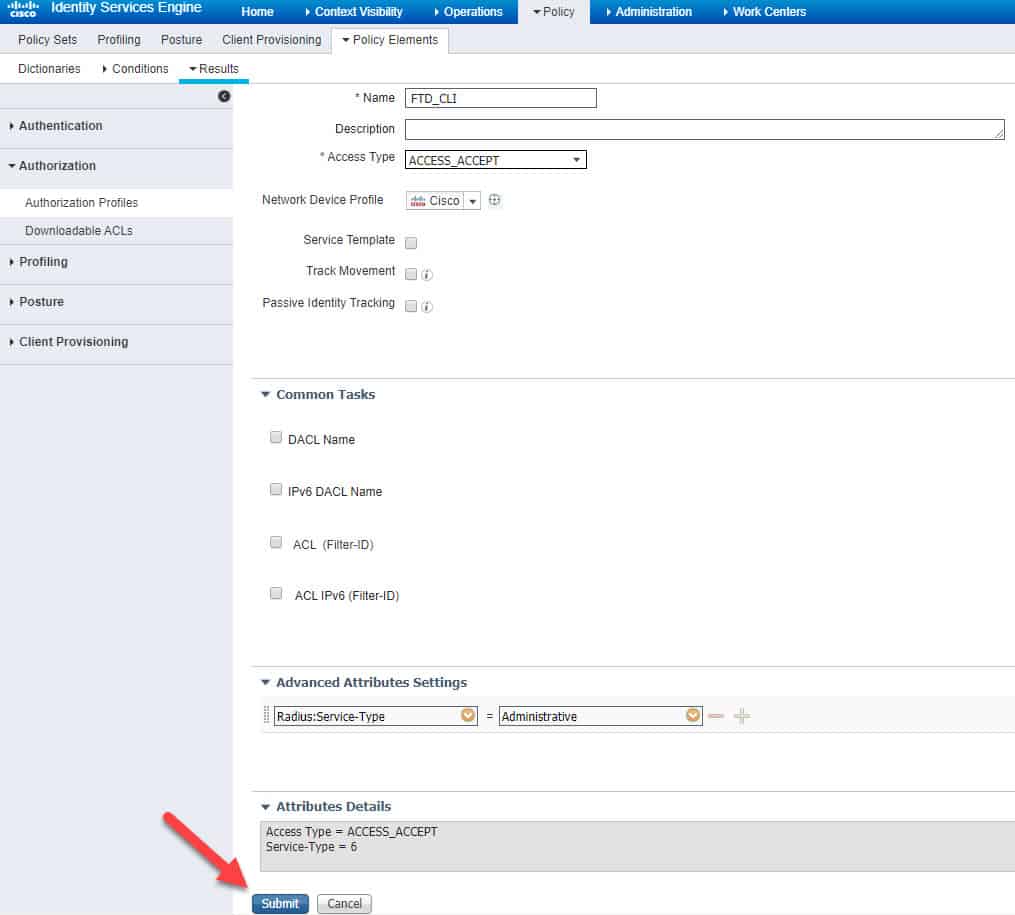
We will call the authZ profile FTD_CLI and we will configure the Service-Type RADIUS attribute with Administrative value:
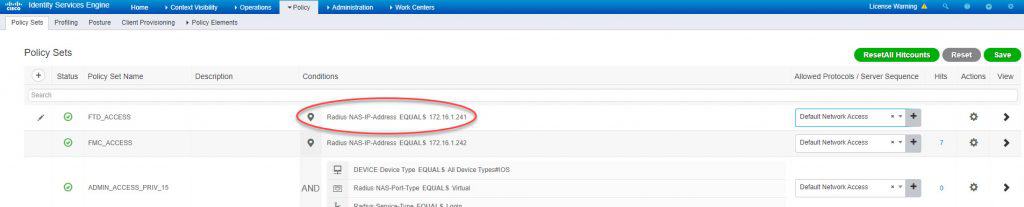
Step 3: Create policy set
We will call the policy set FTD_ACCESS and we will add a RADIUS NAS-IP-Address attribute to the top condition to match only the traffic coming from the FTD management interface IP address 172.16.1.241:
Click Save and open up the new policy set configuration page:
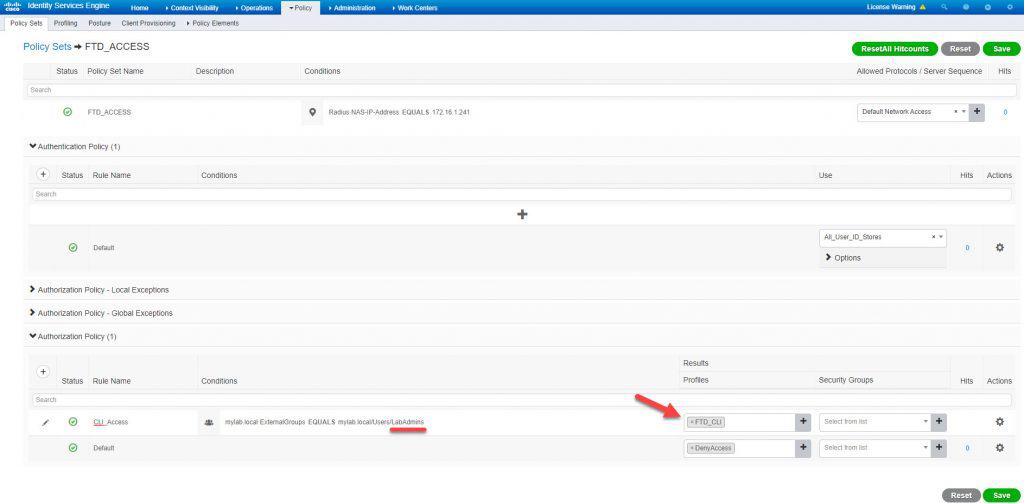
In the authZ rule CLI_Access we will subject the condition to check against the AD group LabAdmins and then we will assign the authZ profile FTD_CLI we created previously:
With the above we have completed ISE configuration, now we will move to the FMC part.
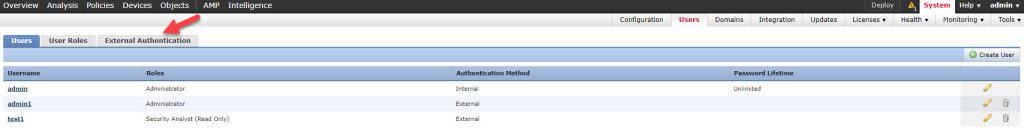
Step 4: Create external authentication object:
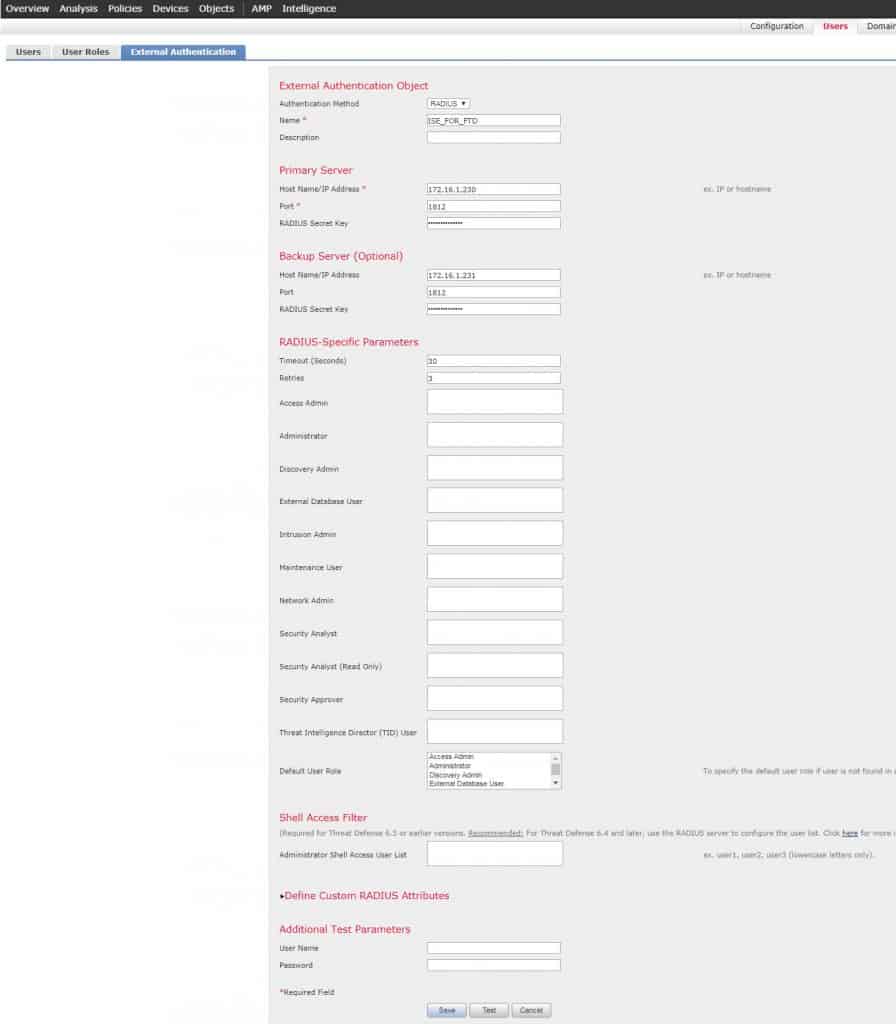
We will call the new External Authentication Object ISE_FOR_FTD. Next we need to fill up ISE PSNs details and save our configuration. Unlike the FMC configuration, note that we don’t need to define any RADIUS attribute in the user roles section. The reason behind this is because there are two types of CLI user roles with FTD, one is Config and another is Basic. The users authenticated and authorized through an external server are always granted Config user role which is an admin role, as long as they have the right authZ attribute. In our case the RADIUS attribute we configured in the authZ profile FTD_CLI is Service-Type Administrative. This will be enough for the FTD to grant the admin1 user admin level access.
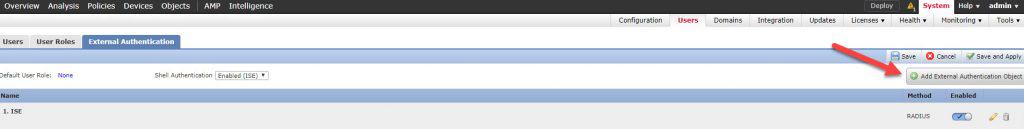
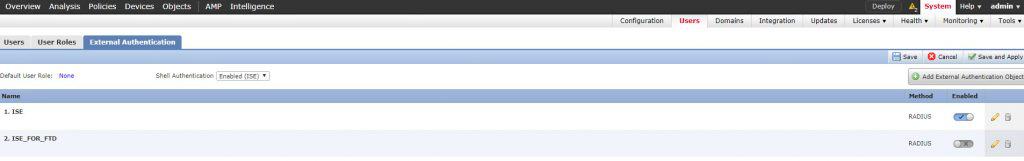
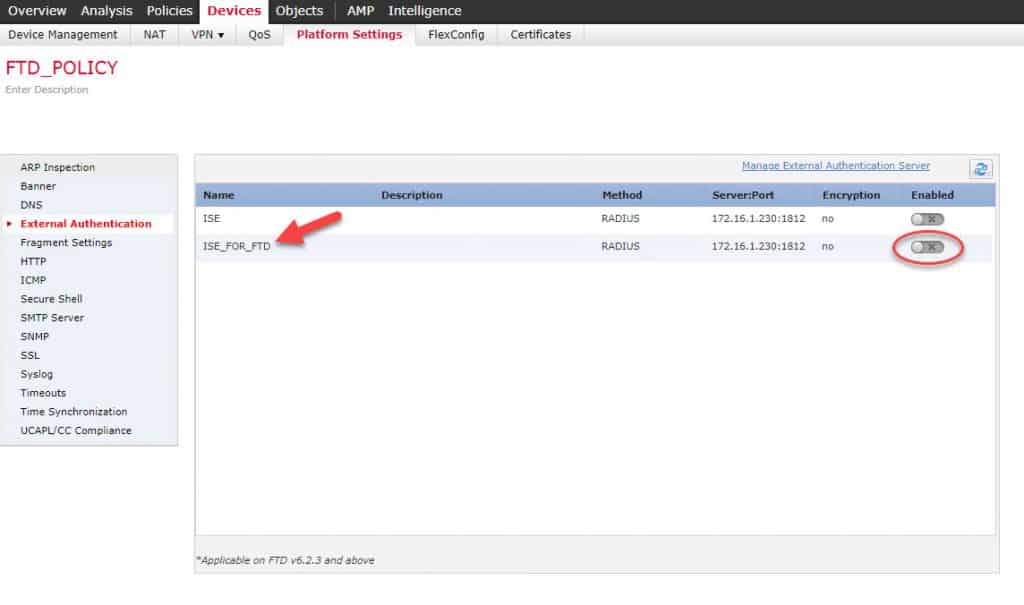
Once you click on the Save button you will get back to the External Authentication page:
As you can see, we did not enable the new External Authentication Object we created from the External Authentication page. The reason is because the object we created is going to be used for FTD accesses, so we will enable it from the FTD platform settings page. However, if we were to use the object for the FMC accesses, then we would have needed to enable it from the External Authentication page.
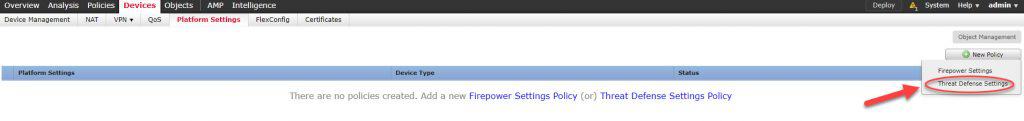
Step 5: Create FTD Platform Settings policy
There are two types of platform settings policies you can configure on FMC. One is for FTD appliances and another for Firepower 7000 and 8000 appliances, the one you use for FTD is the Threat Defense Settings. You might have already a platform settings policy applied to your FTD appliance, if that is the case you can just enable the External Authentication Object we created in your policy.
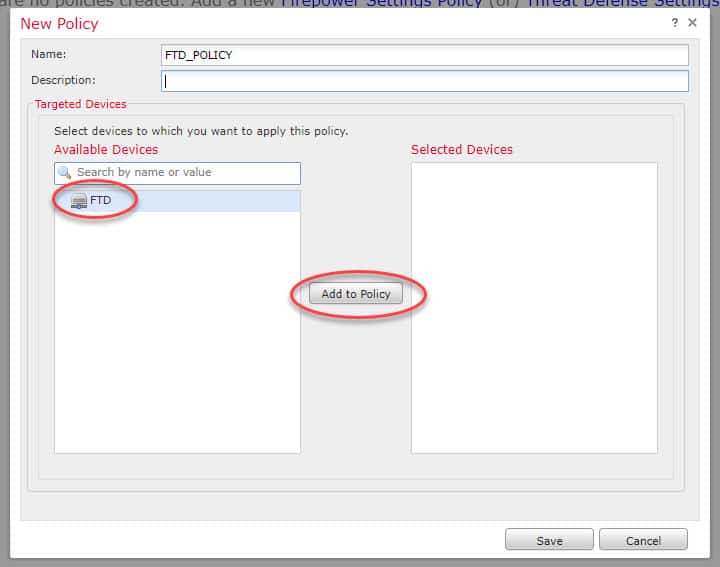
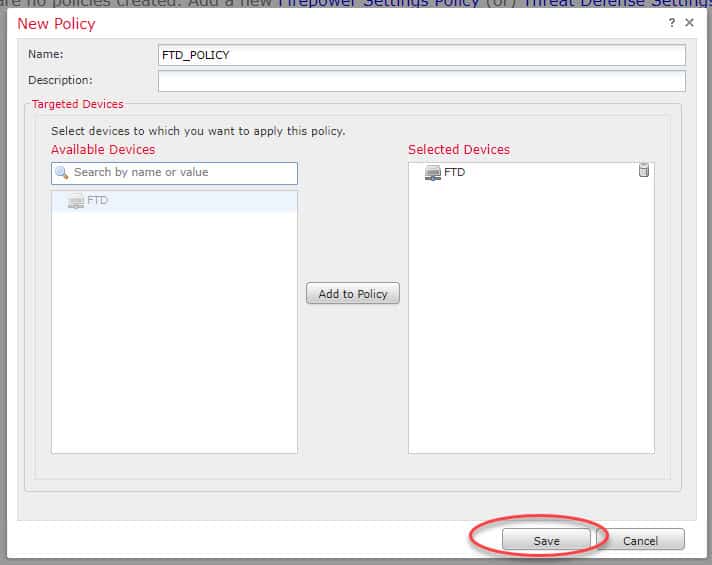
Select the FTD appliance you want to associate to this new policy:
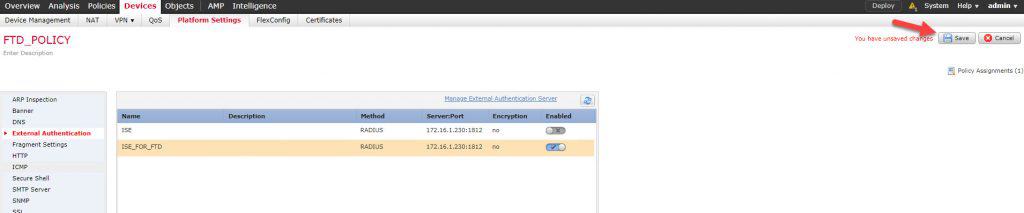
Now go to External Authentication section:
Enable the new policy and save:
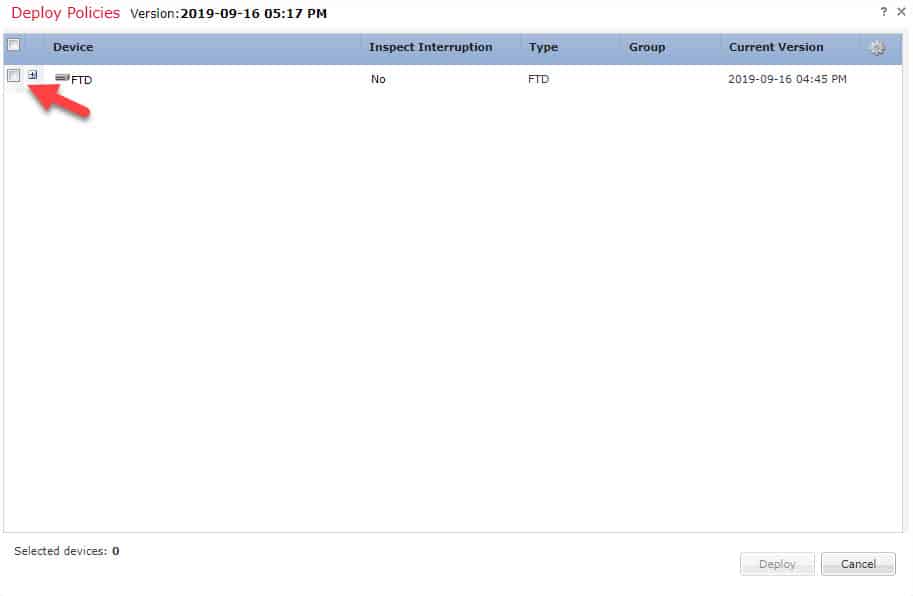
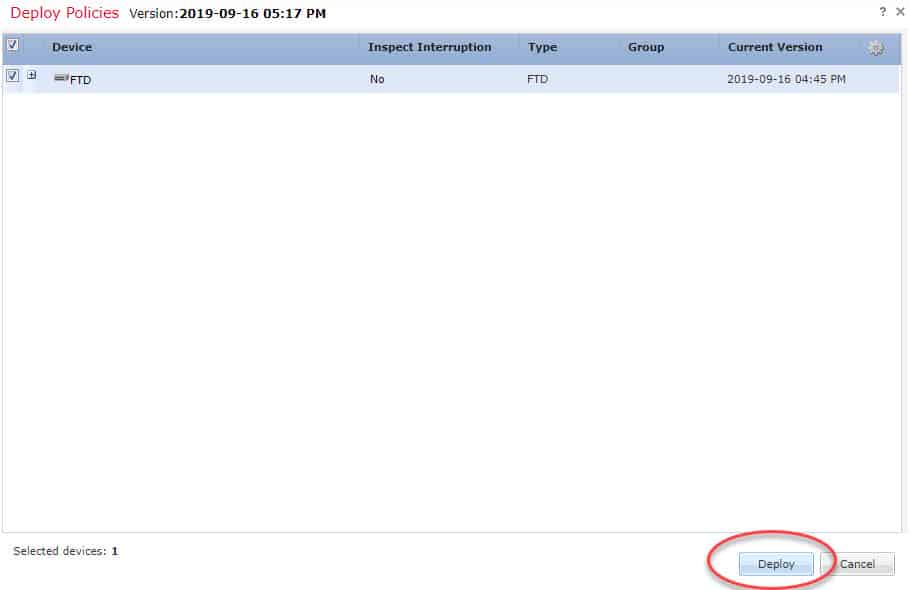
STEP 6: deploy the new changes to the FTD:
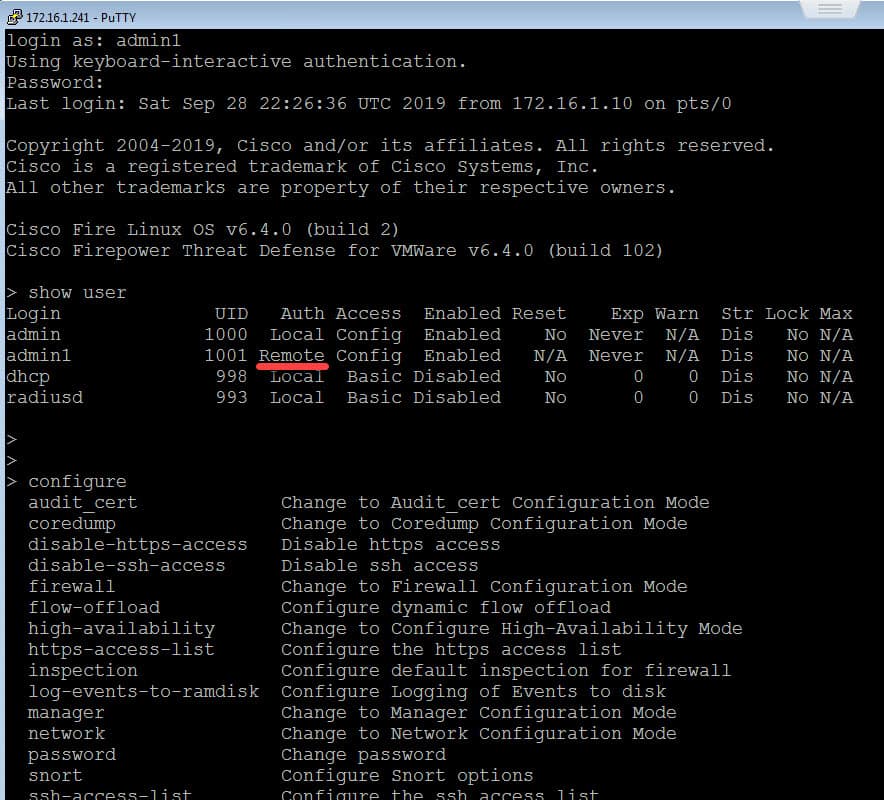
Now it is time to test. I will try to SSH to the FTD management interface from the client connected to the management subnet 172.16.1.0/24.
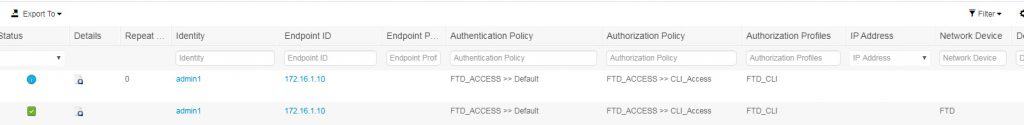
As you can see, we could successfully log into the FTD through CLI as an admin user through RADIUS external authC server. Also, notice how the Auth shows Remote for the admin1 user I used to log into the FTD CLI, that means the user admin1 has authenticated through a remote server, which in our case is the ISE PSN. Finally, let’s have a look at ISE RADIUS Live Logs:
This wraps up the FTD CLI access with RADIUS post. I hope you enjoyed reading this post, and as always, I would love to hear your feedback. Thanks for reading!
Share via:

Thanks for the useful article . . In this post, you’ve created config for a read/write admin account to access over CLI. What changes shall be made on ISE and FTD/FMC for a read-only account access of CLI?