In this post we will talk about the FTD Get Device Configuration and Push Device Configurations. These two options are available in FMC to allow replicating the configuration from one FTD appliance to another. The FTD Get Device Configuration allows us to replicate the configuration from a device to the device we are on. And the FTD Push Device Configurations allows us to do the way around. Basically the Push Device Configurations allows us to replicate the configuration of the device we are on to another.
For instance, say we want to replicate the configuration from device A to device B. So, whether we go to device A and use the option Push Device Configuration. Or, we go to device B and use the option Get Device Configuration.
A couple of reasons comes to my mind about why we would need to do that would be if we are replacing a device. Say we have a partially faulty device and we want to replace it with a new one. Or maybe we are deploying multiple FTD appliances where most of them have a bunch of common configs. Or yet, maybe we are upgrading from a platform to another. For instance, a Firepower 2110 to a 2130.
So far, those are the reasons that came to my mind that would validate using those features. If you think about any other reasons please share them in the comments below. After testing those commands, I found them very handy, and very quick to replicate the configuration. Now, I could test this only on virtual FTD appliances since my lab runs on VMware. However, this feature would also work on physical appliances in the same way as the virtual.
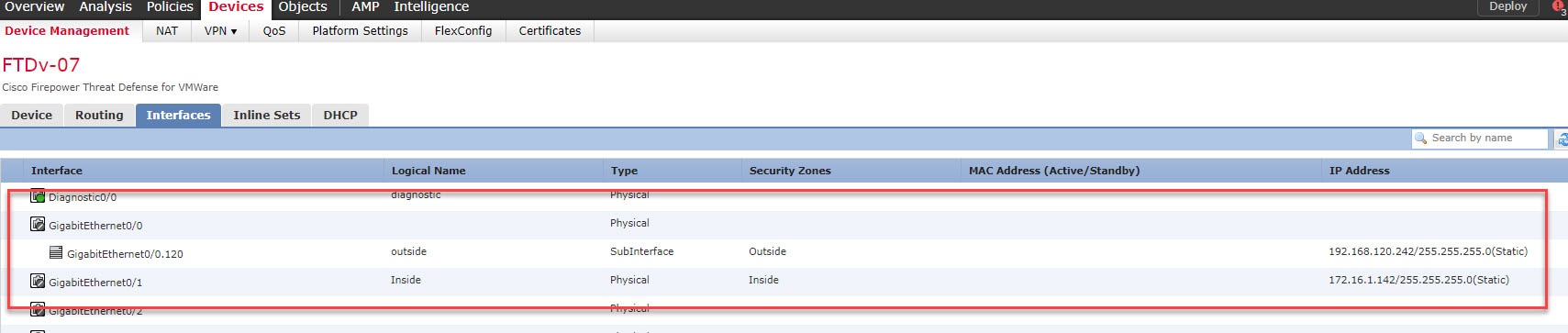
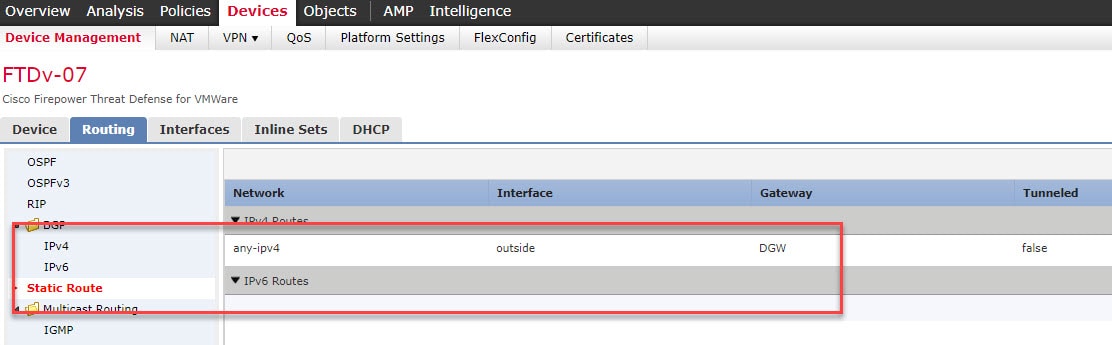
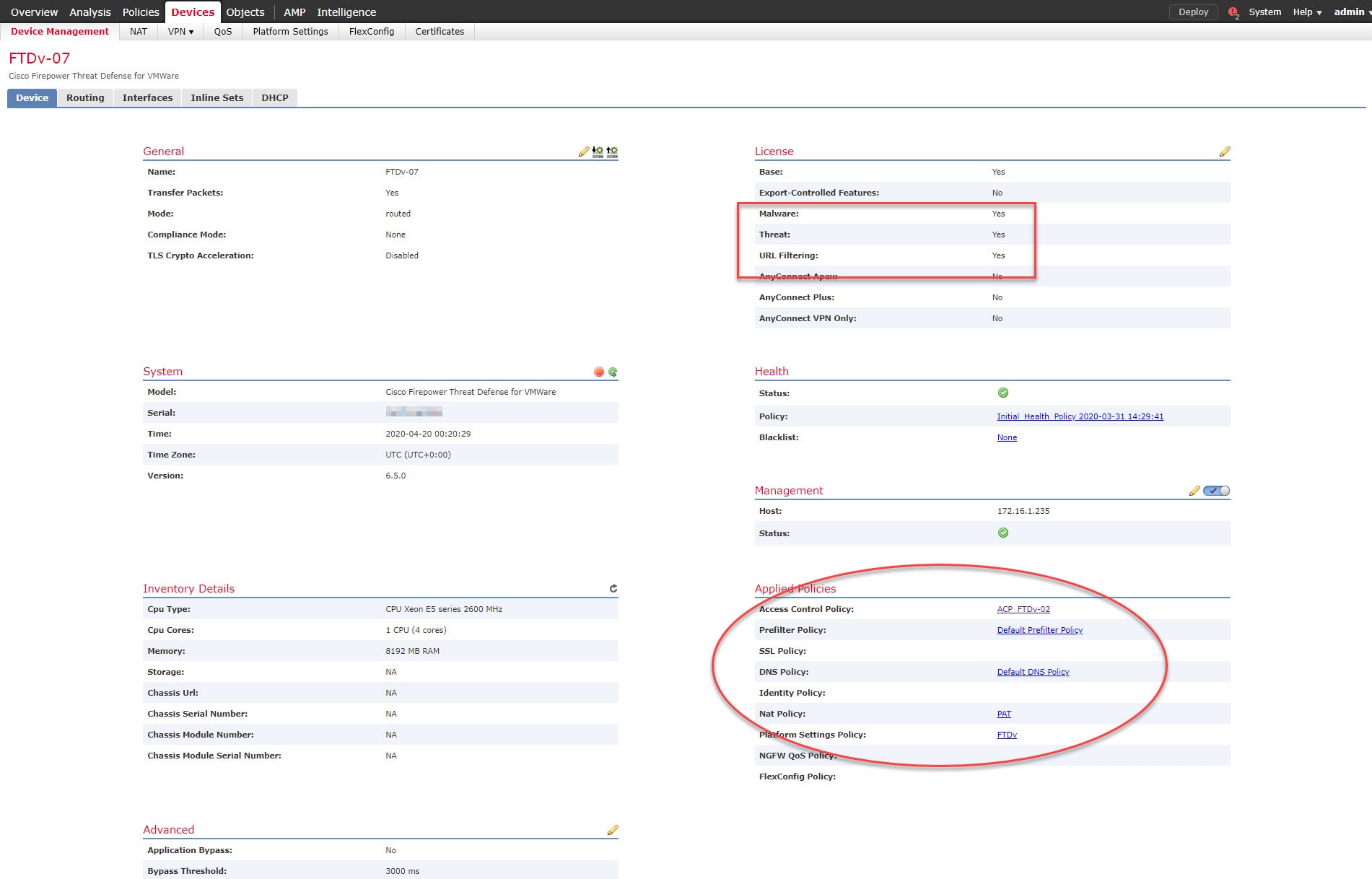
From what I could see and verify, the FTD Get Device Configuration and Push Device Configuration features literally copy and apply the whole configuration from a device to another. That includes policies, routing, IP addressing, sub-interfaces, Security Intelligence, pre-filter, DHCP server, DHCP Relay, etc etc. That will also include enabling the check boxes of the device licenses. The exception for this is the management interface IP addressing, which makes sense to me. All the management interface settings remains intact.
As you might be already thinking, what would happen if we replicate the configuration and the data interfaces IP addresses will be the same!. Well, this means that we will have IP conflicts on our network if both FTD appliances are up and running at the same time. That of course will be disruptive. However, the good news is that we can still remediate this situation.
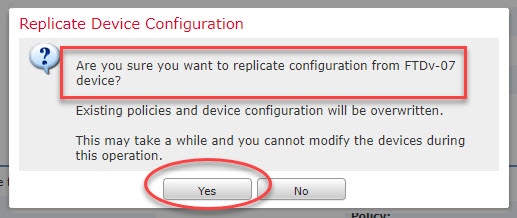
Say, we copied the configuration from device A to device B. Now both devices have same IP addresses (with different MAC addresses) assigned. However, the very important piece of detail is that copying the configuration does not mean we applied yet.
What I mean by this is that the way how the FMC does the replication is divided in phases. Phase one is to stage, in this phase the device B in our example gets its configuration assigned, and ready to be deployed. Therefore, until we apply those changes nothing will happen on device B. The second phase is actually deploying the changes. Once the deploy is completed, both devices will have same active configuration.
So, to remediate such a problem and depending if we are migrating from a device to another, or if we are adding a new device to our network. If we are migrating, then the solution would be to shutdown the data interfaces of the old device, or maybe shutdown the whole device. That should happen before or as soon as we hit deploy button on the FMC.
Please keep in mind that we don't actually need device A to be up at phase two. So we can just deploy the changes to device B while device A is shutdown. However, device A obviously must be up before we can get its configuration replicated to device B, but that is in phase one as we said.
However, if we are adding device B to our network as a new device, and this device needs to have the most of the configuration replicated but the IP addressing, then here is the fix. Basically, after phase one has been completed and before phase two, we can go to the device B and changing its data interfaces IP addresses, and anything else if required.
This means that when we go for phase two to actually deploy the changes to device B, it will apply both the changes that have been replicated from device A, as well as the changes we changed manually. As a result, we will have device B with all the configuration identical as device A, with the exception fro the data interfaces IP addresses that we changed. Now let's see how this works in action.
In our lab we have two FTD appliances, one is called FTDv-02 and the other is called FTDv-07. We will replicate the configuration from FTDv-02 to FTDv-07. As phase one, we will stage the configuration replication using the FTD Get Device Configuration feature. And as as a remediation action before we head to phase two, which is the actual deployment of the changes, we will shutdown the FTDv-07 data interfaces. But you can also change the IP addresses or any other thing before you hit deploy.
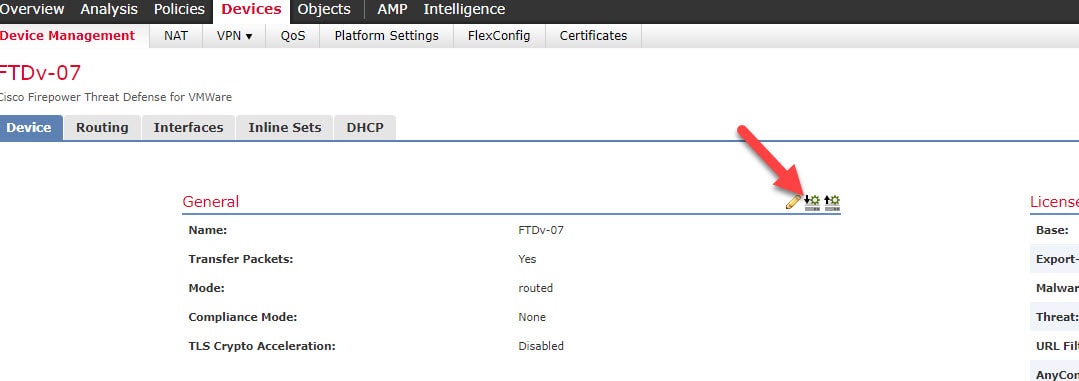
Step 1: Go to Devices > Device Management and click on FTDv-07
Step 2: Verify how the FTDv-07 does not have any configuration as yet since it has just been added to the FMC
Step 3: Click on the Get Device Configuration
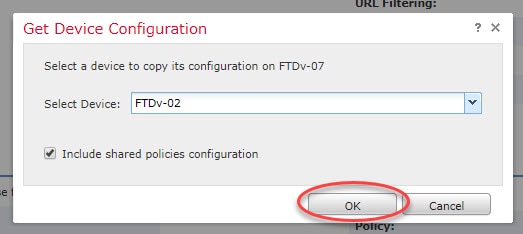
Step 4: Select FTDv-02 device from the list and click OK
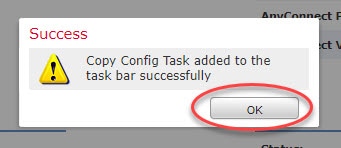
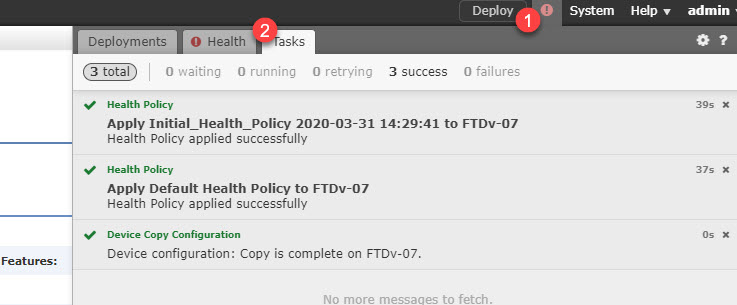
Step 5: Go to Tasks tab to check the phase one (preparation) status
Step 6: Go back and check if the FTDv-07 now has any new changes pre-staged
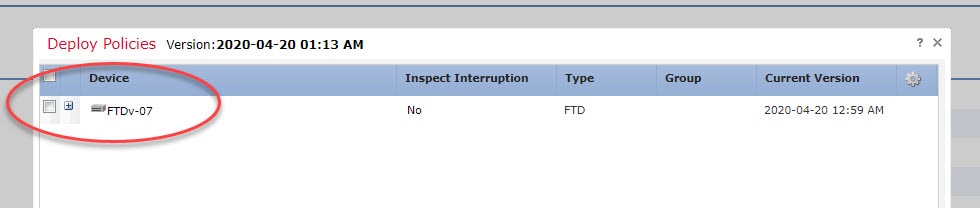
Let's go to check the devices ready for the deployment
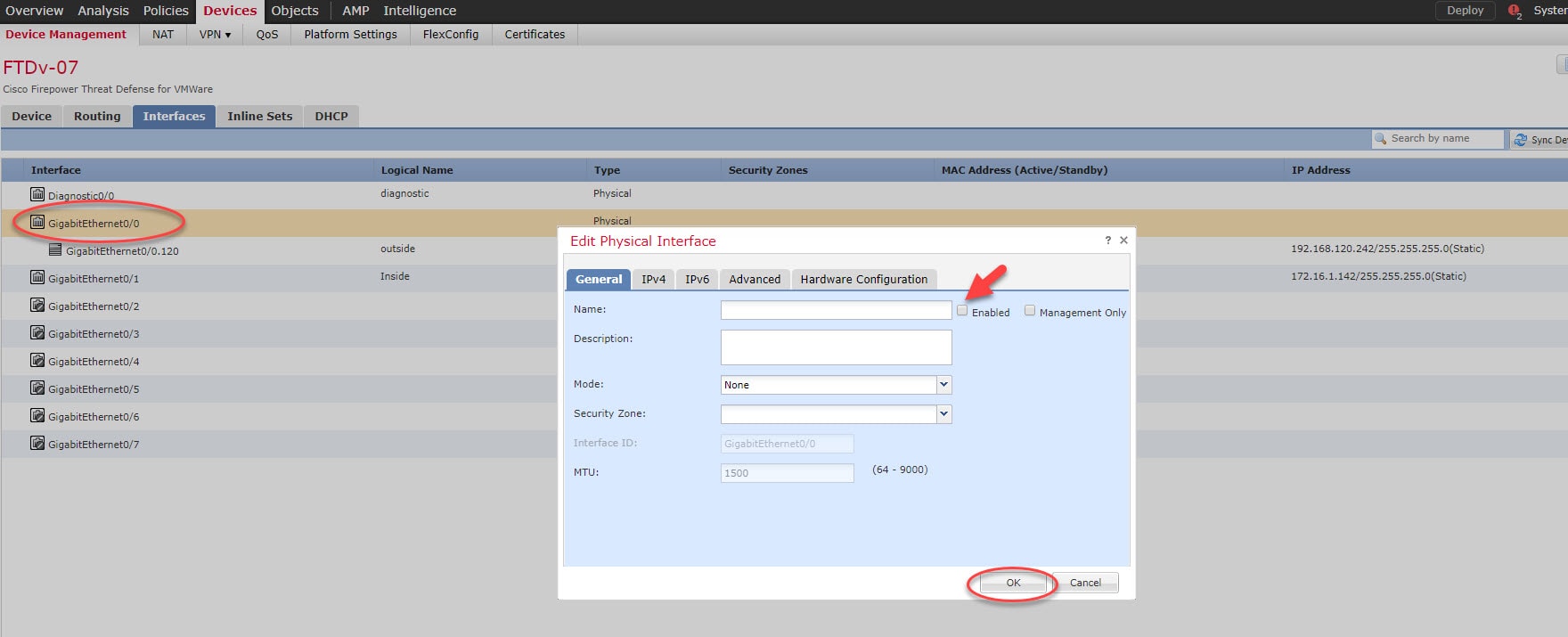
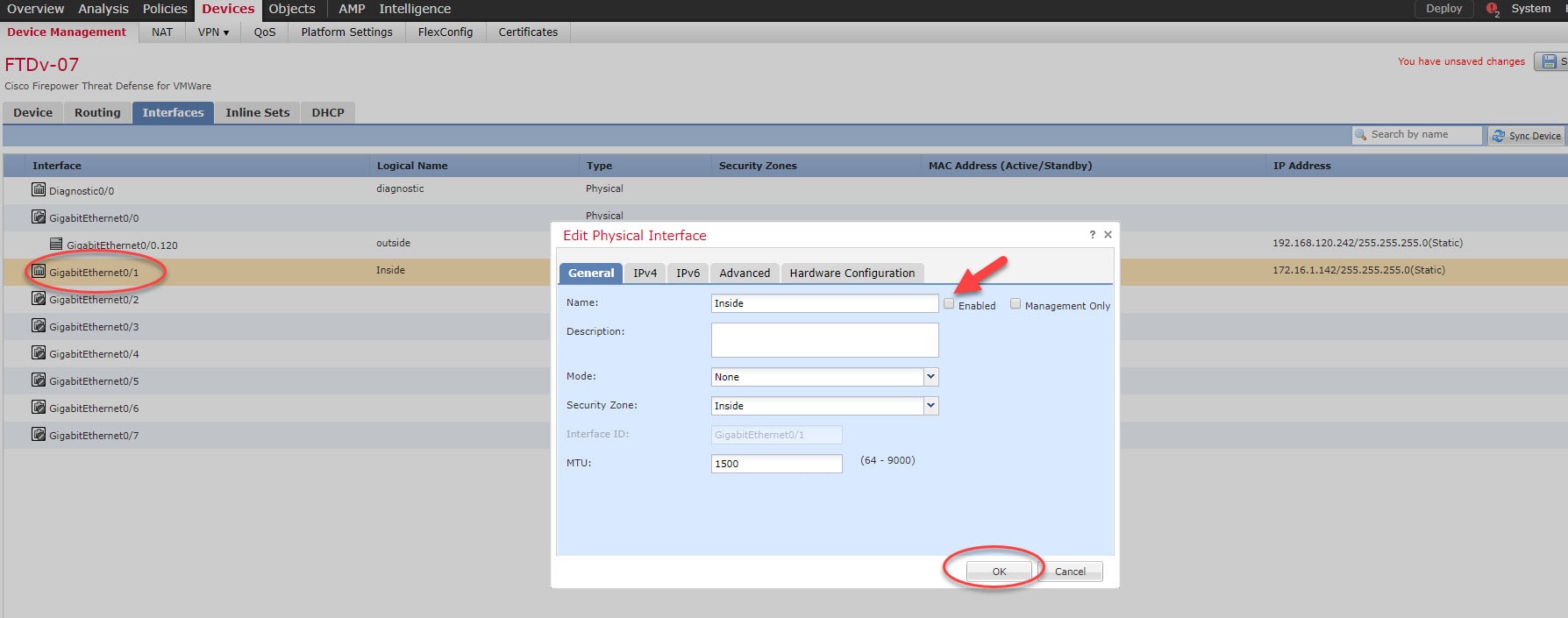
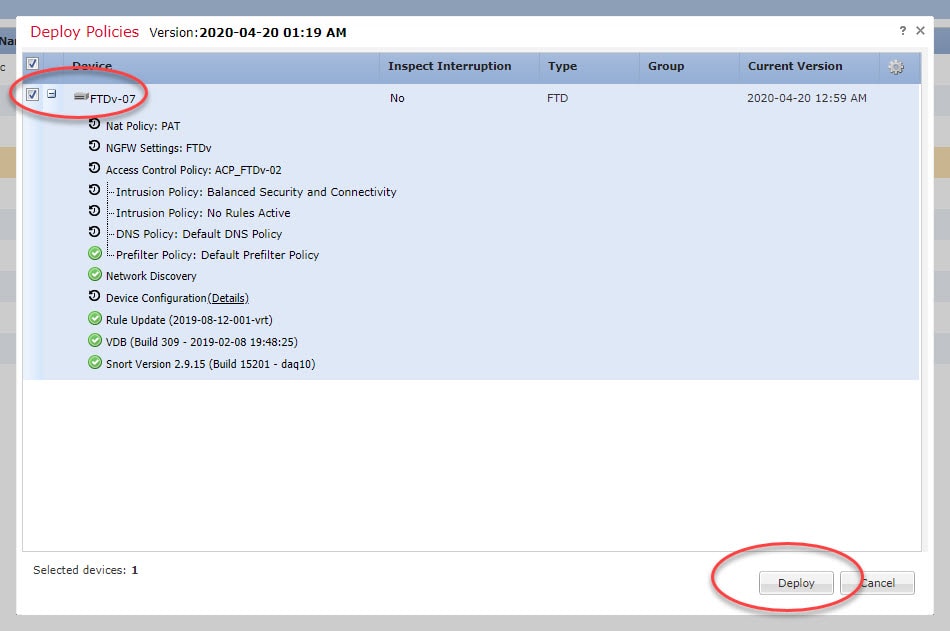
Step 7: Go back to Devices > Device Management > Interfaces and disable both Gi0/0 and Gi0/1 interfaces
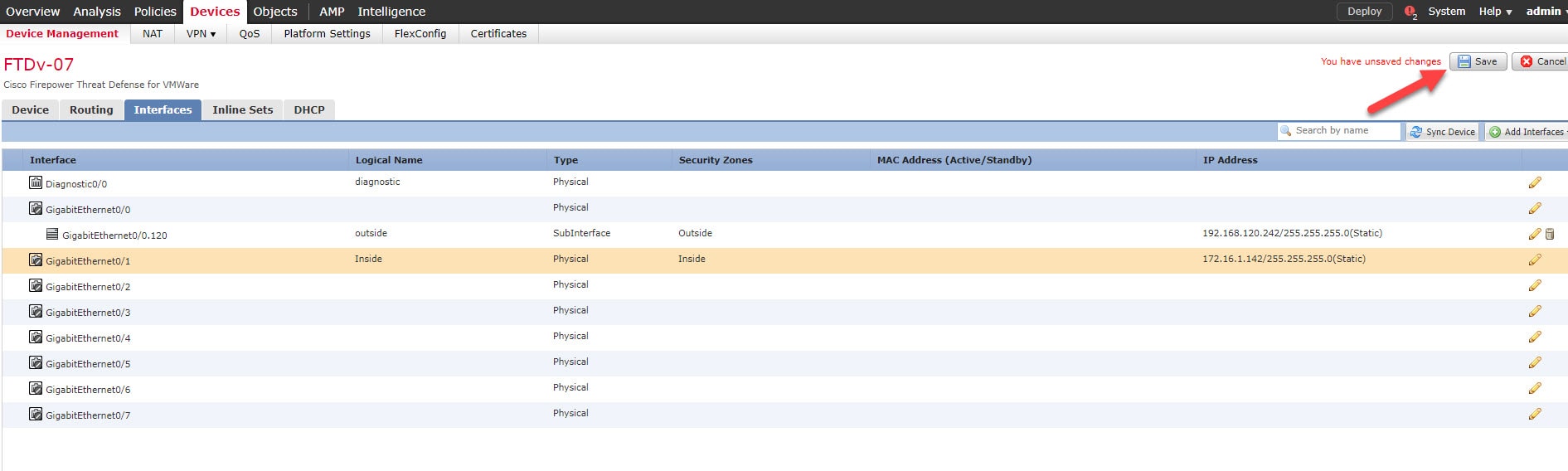
Step 7: Click on Save and deploy the changes
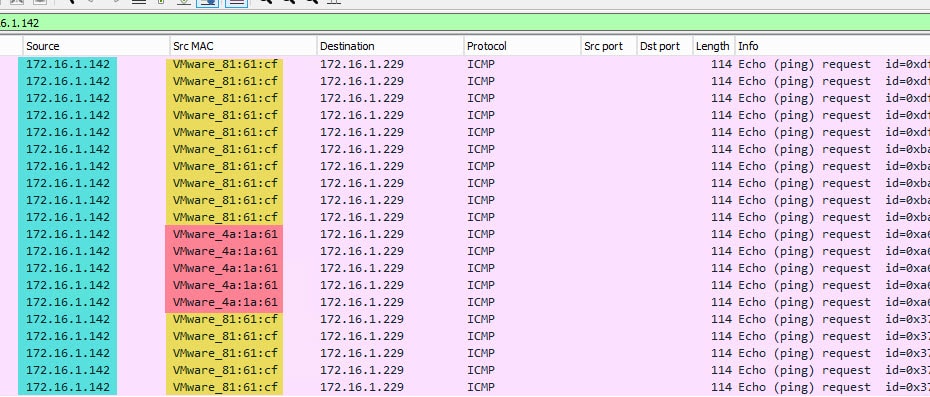
Just for the sake of demonstration, I simulated the scenario where both FTDv-02 and FTDv-07 were active on the network at the same time. And I initiated some ICMP traffic from both FTDv-02 and FTDv-07 to the destination 172.16.1.229. As you can see from the packet capture, the source IP of FTDv-02 and FTDv-07 inside interface is the same. However, the MAC address is different. This means that from the host 172.16.1.229 perspective, it will keep refreshing the ARP entry for the IP 172.16.1.142. This will cause disruption for the traffic passing through FTDv-02 or FTDv-07.
This wraps up this post on FTD Get Device Configuration and Push Device Configuration features.
Thank you for reading!