What are the Snort HOME_NET and EXTERNAL_NET Variables?! To know that let’s see how Snort rules work. Snort rules rely on variables to know what traffic they should inspect and what to ignore. Each Snort rule has a header where a bunch of variables are defined such as the action to be taken, protocol, source IP, source port, destination IP and destination port. The most important two bits among these variables are the source and destination IP addresses.
These two variables define what should be protected and what should not. In Snort language, these two variables are called HOME_NET and EXTERNAL_NET. HOME_NET should include all the IP addresses that Firepower should protect which means all our IP addresses whether private or public, but what about the EXTERNAL_NET?! should it be anything else except our protected IP addresses that we defined in our HOME_NET?! or should it be anything including our HOME_NET?! let’s find out together :).
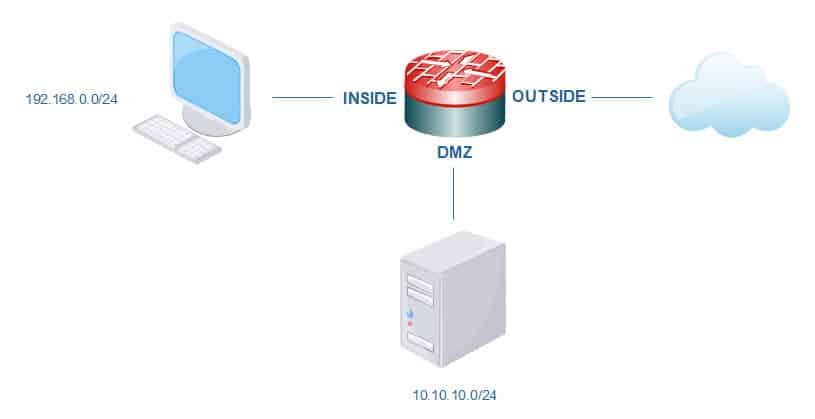
Let’s assume we have a Firepower appliance with three segments, we have the inside segment where we have all our internal hosts located on the subnet 192.168.0.0/24. We also have the DMZ segment where we have all our servers that are serving public traffic to the internet which are located on the subnet 10.10.10.0/24, and finally we have the outside segment which is directly connected to the internet. Below is our topology with all the three segments.
TOPOLOGY
Let’s define our Snort HOME_NET and EXTERNAL_NET variables as follows:
HOME_NET = 192.168.0.0/24 & 10.10.10.0/24
EXTERNAL_NET = Anything except HOME_NET
Excluding the HOME_NET from the EXTERNAL_NET is a common thing among the majority of us. We will see later in this post if this is a good thing to do or if it could go against our security.
DEFINING SNORT HOME_NET and EXTERNAL_NET VARIABLES
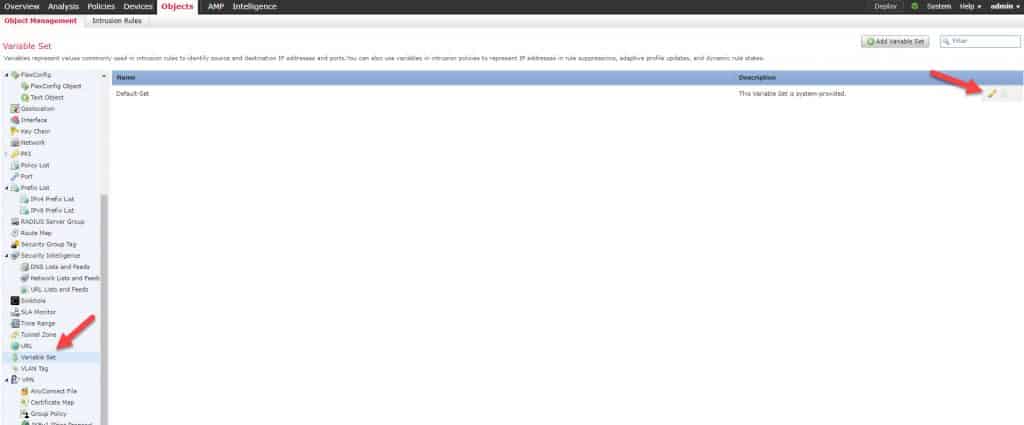
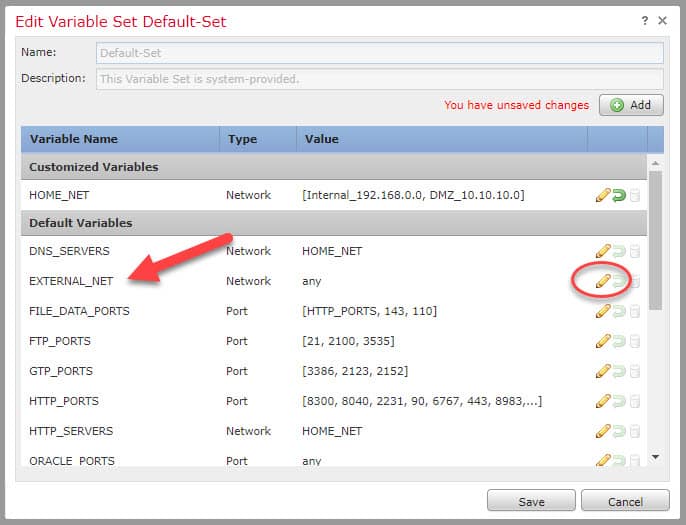
Let’s start with defining our variable set as mentioned above. To do so on the FMC, we need to go to Objects -> Object Management -> Variable Set and then click on the pencil icon on the top right:
Click on the pencil icon next to HOME_NET:
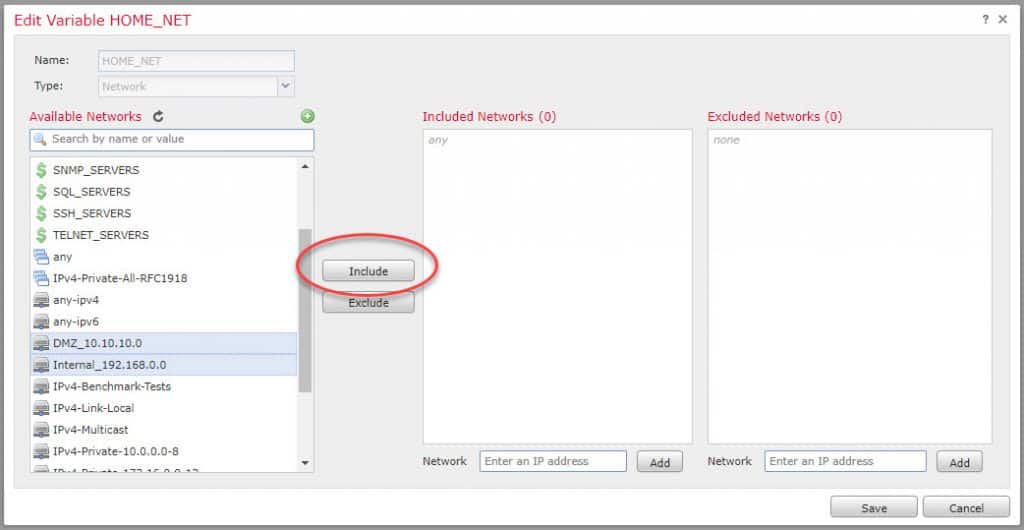
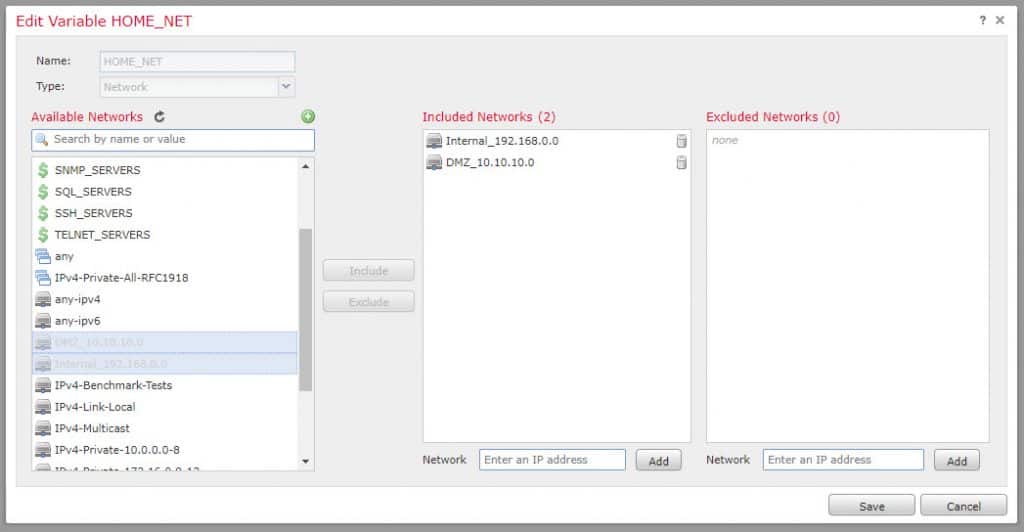
Search for the two variables that include our subnets and click Include and save:
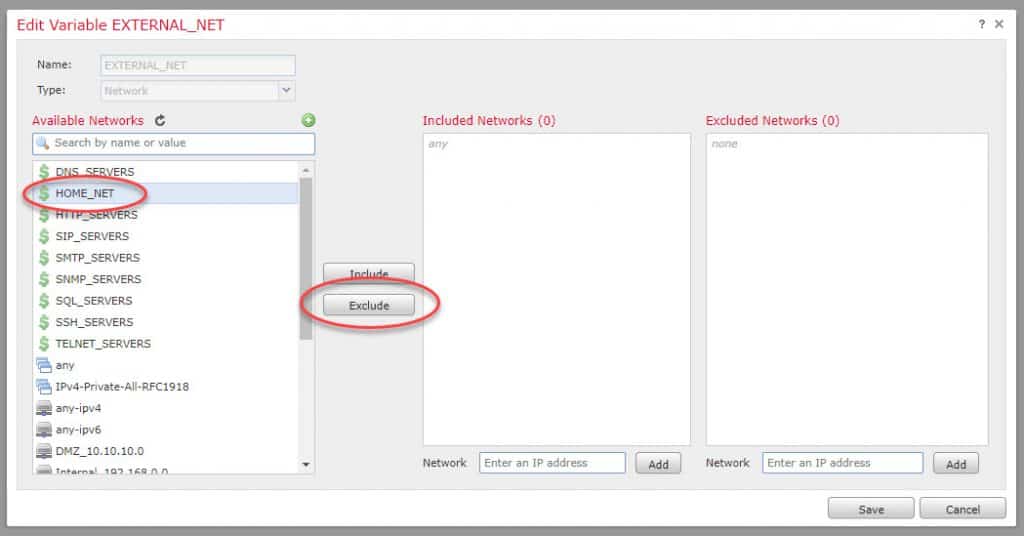
Click on the pencil icon next to EXTERNAL_NET:
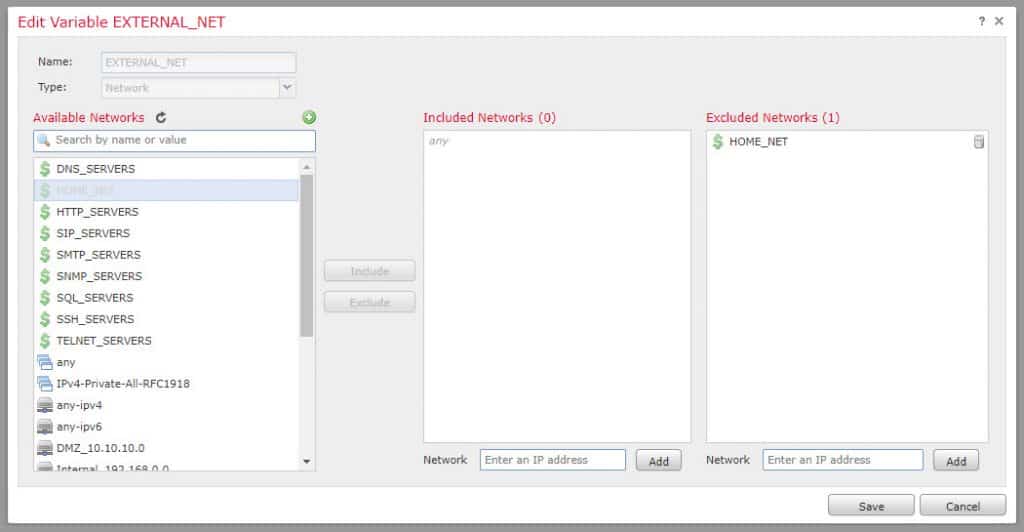
Search for the HOME_NET variable and click Exclude and save:
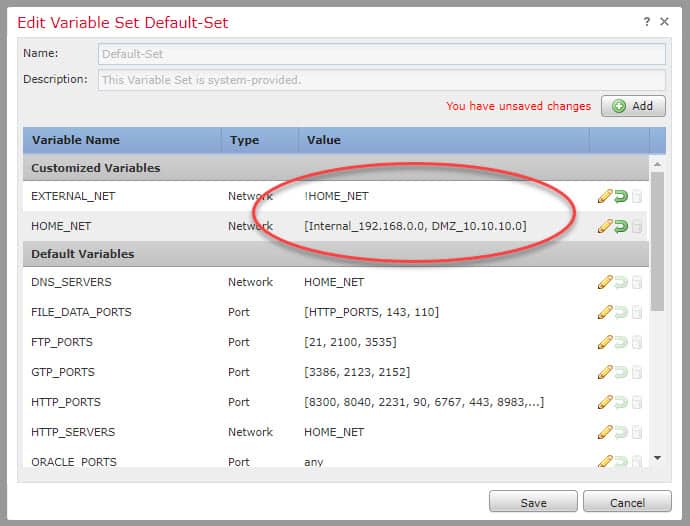
Here is how Snort HOME_NET and EXTERNAL_NET Variables look like now:
The exclamation mark used in the EXTERNAL_NET variable means “not equal to”, so our EXTERNAL_NET variable is defined as anything but our HOME_NET.
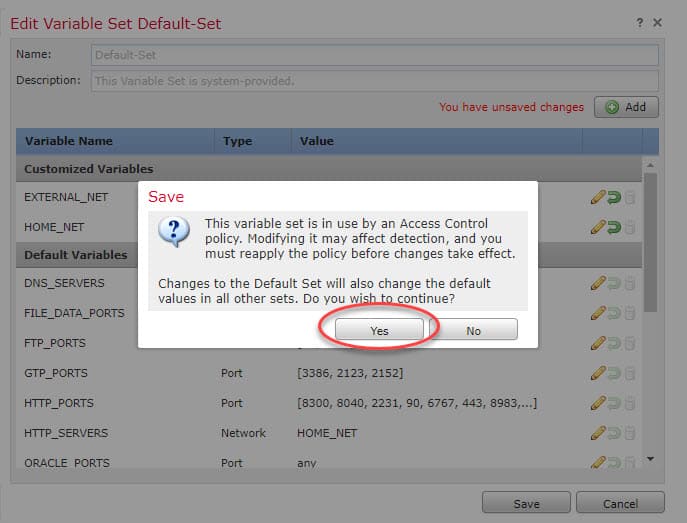
Save the changes:
SNORT RULE
Now let’s take this random Snort rule as an example:
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg:”SERVER-APACHE Apache HTTP Server mod_http2 denial of service attempt”; flow:to_server,established; content:”|01 00 00 00 00 01|”; content:”|09 01 00 00 00 01|”; within:50; content:”|09 01 00 00 00 01|”; within:25; content:”|09 01 00 00 00 01|”; within:25; metadata:service http; reference:cve,2016-8740; classtype:denial-of-service; sid:41688; rev:1; gid:1; )
TRAFFIC FLOW
Let’s assume there is an ongoing attack from the internet against our server in the DMZ segment. Based on the variable set we defined Snort should be able to see this attack because the traffic coming from the internet would fall into the EXTERNAL_NET variable and the traffic going to our server would fall in the HOME_NET variable. Same would happen if the attack is conducted against our internal host. Good, now let’s take another example.
Let’s say our internal host in the inside segment is now the attacker so the attack now is conducted from our internal host to the server in the DMZ. Would Snort see this attack?! the answer is no. The reason why Snort would not be aware about this attack at all is because this time as we can see the traffic coming from our internal host would not fall in the EXTERNAL_NET variable because the EXTERNAL_NET variable we defined includes everything except our HOME_NET and accordingly Snort rule will not be matched, this is why Snort in case is totally blind.
THE FIX
To fix this we need to include our HOME_NET into the EXTERNAL_NET variable, we can do so by reverting the EXTERNAL_NET variable to its default value which is any. By doing so, Snort now can see the attack coming from our internal host going to the server because this time the traffic coming from our internal host would fall into the EXTERNAL_NET variable which means Snort rule will be matched.
To revert the EXTERNAL_NET variable to its default value we need to click on the curved green arrow and save our changes:
As we can see now the EXTERNAL_NET variable moved to the Default Variables section, don’t forget to save the new changes.
I hope you enjoyed reading this Snort HOME_NET and EXTERNAL_NET Variables post and why we should include our HOME_NET in EXTERNAL_NET. As always, I would love to hear your feedback. Thanks for reading!
Share via:



Very detailed article and well explained. So this means we shouldn’t change either of the variable because?